Salt Typhoon and the Widespread Hacking of Western Telecoms Networks
How China's technical typhoons split open US and European government and public phone/data networks
China's Salt Typhoon campaign represents a fundamental shift in state-sponsored cyber espionage, moving away from the opportunistic targeting of individuals towards the systematic subversion of national telecommunications infrastructure. Attributed to contractors working for the Chinese Ministry of State Security based in Chengdu, this operation has exposed a profound structural vulnerability at the heart of Western democratic governance.
The campaign is defined by a security paradox: the very mechanisms designed to assist domestic law enforcement, such as the Communications Assistance for Law Enforcement Act (CALEA) in the United States and the Investigatory Powers Act in the United Kingdom, became the primary channels for foreign intelligence gathering.
The exploitation of vulnerabilities
The technical core of Salt Typhoon lies in its exploitation of legally mandated “backdoors”.
Since 1994, US telecommunications providers have been required by CALEA to maintain access points for court-authorised wiretapping.
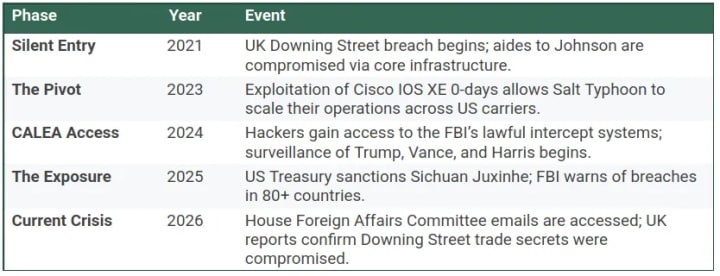
Salt Typhoon hackers did not need to break into individual smartphones; instead, they compromised the core network interfaces where these surveillance streams converge and dwelled in the networks. By gaining access to these systems, the bad actors were able to intercept metadata for millions of subscribers and monitor the unencrypted communications of high-value targets, including senior staff for the 2024 presidential campaigns of Donald Trump, JD Vance, and Kamala Harris.
In the UK, a parallel breach targeted the communications of aides to three successive Prime Ministers: Boris Johnson, Liz Truss, and Rishi Sunak. Between 2021 and 2024, the hackers maintained persistent access to the heart of Downing Street.
This dwell time allowed for the potential exposure of sensitive internal deliberations regarding the Huawei 5G ban and the formation of the AUKUS security pact. The breach demonstrates that no level of ministerial office is immune when the underlying infrastructure is compromised.
Salt Typhoon infiltration has been reported in over 80 countries (including Canada, Australia, New Zealand, UK, Europe, Southeast Asia, Africa, and others).
Technical mechanisms and persistence
The success of Salt Typhoon is attributed to a sophisticated suite of tools and a “low and slow” approach to network infiltration. Initial entry was often achieved through critical vulnerabilities in Cisco IOS XE routers, specifically CVE-2023–20198 and CVE-2023–20273. These flaws allowed the attackers to bypass authentication and gain administrative control over the devices that form the backbone of the internet.
Once inside, the actors utilised the Cisco “Guest Shell” — a virtualised environment intended for network automation — to hide their activities from standard security software. Persistence was maintained through modular backdoors such as GhostSpider and the Demodex rootkit.
These tools are designed to survive system reboots and firmware updates, leading to an average dwell time of 393 days.
Data exfiltration was conducted with surgical precision using techniques like JumbledPath and GRE tunnels, which disguised the stolen information as routine internal network traffic, making detection nearly impossible for traditional intrusion detection systems.
The counterintelligence coup
Perhaps the most damaging aspect of the campaign was the compromise of FBI counterintelligence databases. By accessing the records of who the FBI was investigating and which lines were under surveillance, the Chinese Ministry of State Security gained a “god’s eye view” of US domestic security operations.
This allowed Chinese intelligence officers to adjust their tactics in real-time, effectively immunising their assets from Western detection. This level of insight into the decision-making processes of the Five Eyes alliance has been described by some officials as a strategic disaster, potentially more significant than the 2020 SolarWinds hack.
A timeline of systemic failure
The progression of Salt Typhoon illustrates a steady escalation from infrastructure probing to the compromise of national leadership.
The end of the backdoor debate
The legacy of Salt Typhoon is likely to be the total reassessment of surveillance policy in the West. The “security paradox” has shown that a backdoor created for a “good guy” is eventually found and used by a “bad guy”.
As a result, 2026 has seen a clear shift towards mandatory end-to-end encryption and a massive US-led $3 billion programme to remove and replace Chinese-linked hardware from global networks. Such programmes are under way in all the AUKUS countries.
The era of trusting the infrastructure is over; the focus has shifted to zero-trust architectures where the network itself is assumed to be hostile.
Note
In case you have heard the words ‘Volt Typhoon’ and are puzzled, here is a brief explainer.
Salt Typhoon and Volt Typhoon are distinct yet complementary threats which represent markedly different strategic priorities.
Salt Typhoon, attributed to China’s Ministry of State Security (MSS), is an espionage operation without equal. Its primary objective is intelligence collection: intercepting communications metadata, call records, geolocation data, and content from high-value targets — US government officials, political figures, corporate leaders, and counterintelligence personnel. The campaign exploits vulnerabilities in telecommunications infrastructure to gain persistent access to backbone networks, lawful intercept systems, and router-level controls.
The focus is long-term surveillance rather than immediate disruption.
In contrast, Volt Typhoon, linked to elements of the People’s Liberation Army (PLA), is a pre-positioning campaign. The operation embeds itself in critical infrastructure sectors (electric grids, water treatment, transportation, ports, pipelines) using ‘living-off-the-land’ techniques to avoid detection.
Its goal is not to steal secrets today but to prepare the ground for potential kinetic conflict tomorrow — most analysts believe it is oriented towards a Taiwan contingency.
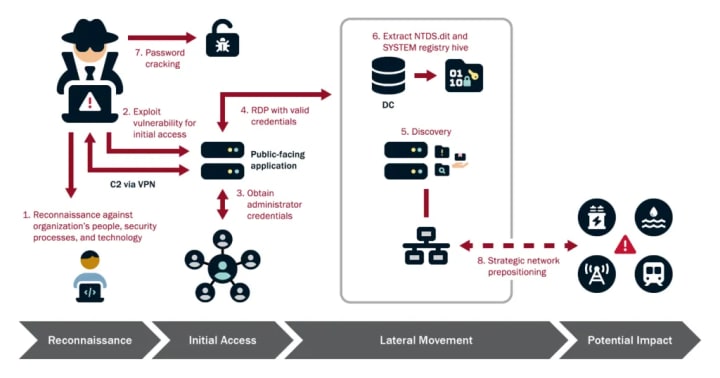
The intent is to create latent disruptive capability: backdoors, command-and-control footholds, and “digital time bombs” that could be activated to delay or degrade US and allied response in a crisis.
The two campaigns are complementary rather than contradictory.
Salt Typhoon provides the intelligence picture — who is where, what is being planned, how communications flow — while Volt Typhoon builds the sabotage infrastructure that could exploit that intelligence.
Implications
Salt Typhoon’s exposure in late 2024 and the continuing revelations into 2026 have several immediate and longer-term consequences.
First, it has accelerated US efforts to harden telecommunications infrastructure. The FCC’s new supply-chain restrictions, CISA’s red-teaming of telecom providers, and the Treasury’s sanctions on associated Chinese firms (including Integrity Technology Group/i-Soon in January 2025) are direct responses.
Second, the campaign has deepened mistrust between Washington and its telecom sector. Carriers face a dilemma: cooperate fully with government investigators and risk customer backlash over privacy, or limit disclosure and invite accusations of complicity. This tension will probably intensify in 2026 as congressional hearings continue and civil lawsuits emerge.
Third, Salt Typhoon reinforces the strategic asymmetry in cyber conflict. As I have often written about, China can afford to play a long game — persistent, low-visibility access — while Western defenders remain reactive, constrained by privacy laws, corporate liability, and political oversight.
The operation demonstrates that even heavily defended networks can be penetrated when the adversary controls the supply chain, the hardware, or the human element.
The most significant implication may be political rather than technical. The breach arrives at a time when US policy towards China is hardening under the Trump administration, with renewed focus on decoupling critical infrastructure from PRC-linked vendors.
Salt Typhoon provides ammunition for those advocating aggressive measures — export controls, entity list expansions, and possibly offensive cyber operations. Whether that leads to escalation or deterrence remains the central question.
The architecture of betrayal is now visible. The question is whether the West can dismantle it faster than China can rebuild it.
This is an edited version of the story originally published on Medium.com
I also write on Substack.
(c) James Marinero 2026. All rights reserved.
About the Creator
James Marinero
I live on a boat and write as I sail slowly around the world. Follow me for a varied story diet: true stories, humor, tech, AI, travel, geopolitics and more. I also write techno thrillers, with six to my name. More of my stories on Medium






Comments
There are no comments for this story
Be the first to respond and start the conversation.