Anna Shipman
Bio
Anna Shipman is a Cyber Security Consultant with a strong technical background and experience with a high analytical skillset. She has been involved in the information security industry for more than a decade.
Stories (37)
Filter by community
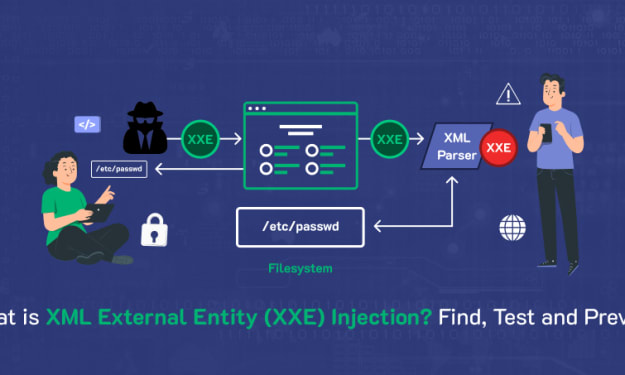
A Guide to XXE Vulnerabilities: What is XML External Entity Injection and How to Stop It
XML external entity injection or XXE, is a type of web security vulnerability and an application-layer cybersecurity attack. This vulnerability allows the hacker to interfere with an application while it is processing XML data.
By Anna Shipman7 months ago in 01
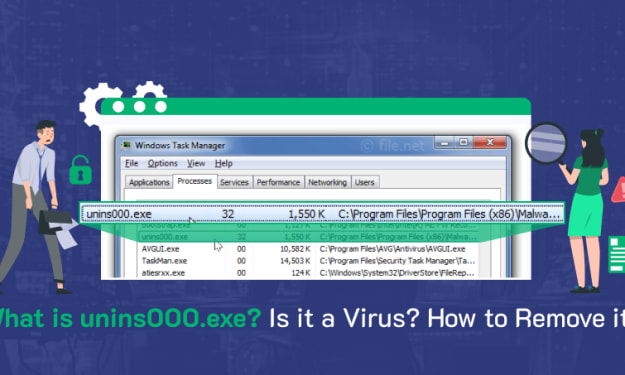
Is unins000.exe Causing Trouble? Here's What It Is and How to Get Rid of It
unins000.exe: Is It Safe or Should You Be Concerned? If you've stumbled upon a strange-looking file called "unins000.exe" on your Windows computer, you're probably wondering what it is and whether it's something to worry about. You're not alone. Many users find unfamiliar files on their systems and immediately jump to concerns about malware. It's a valid worry in today's digital world, but not everything unfamiliar is dangerous.
By Anna Shipman8 months ago in 01
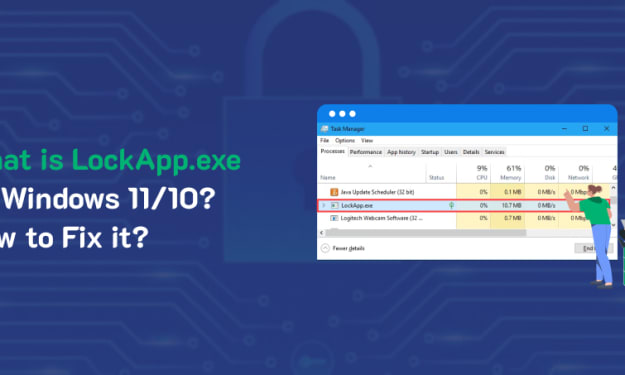
How to Resolve LockApp.exe Issue In Windows 11/10
Windows 11/10 is a robust operating system with security features and a user-friendly interface. However, like any other OS, it also comes with several glitches and errors. One such issue that users frequently encounter is related to LockApp.exe.
By Anna Shipman8 months ago in Geeks
Mastering Key Management to Minimize Cryptographic Risks
The popularity of mobile devices and cloud applications has created unlimited endpoints, leaving data vulnerable to security threats. Cryptographic failures rank no.2 in OWASP's top 10 web application security risks.
By Anna Shipman9 months ago in 01
Stay Safe in 2025: 10 Mobile App Security Trends and Solutions
In this Digital Era, mobile devices play a fundamental role in our daily lives. Recent studies reveal that the number of smartphone users worldwide has reached over 6.8 billion and is increasing day by day. These devices store most of the sensitive data, like personal and financial data
By Anna Shipman9 months ago in 01
Viruses vs. Worms vs. Trojans: Understanding the Key Differences
A tremendous surge has been seen in the number of systems infected with different types of malicious software over the past few years. Among the various types viruses, worms, and Trojan horses are some of the most well-known.
By Anna Shipman9 months ago in 01
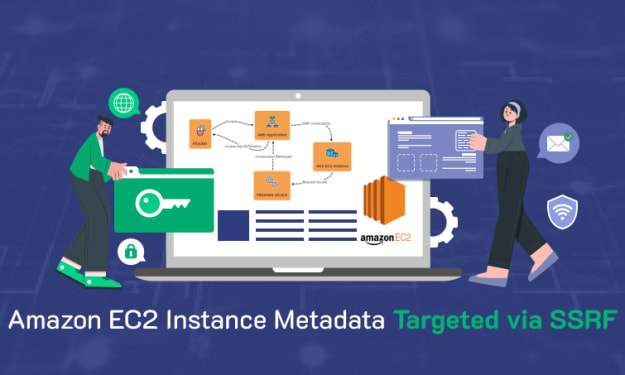
Amazon EC2 Metadata Exposed Through Server-Side Request Forgery (SSRF) Attack
On March 25, 2024, the National Security Agency (NSA) and the Cybersecurity and Infrastructure Security Agency (CISA) issued a joint advisory highlighting the increasing threat of Server-Side Request Forgery (SSRF) vulnerabilities. This advisory underscores the growing concern over SSRF, particularly in cloud environments where its exploitation can lead to significant security breaches.
By Anna Shipman9 months ago in 01
Definition of Server Side Request Forgery (SSRF). Know Its Types, Impact, and Prevention Practices
Introduction In the past few years, the risk of cyberattacks has grown enormously. In fact, more than 800,000 people experience data security breaches every year, which is quite concerning.
By Anna Shipman10 months ago in Education
What is Token-Based Authentication? Cover its Types, Importance, and Best Practices
Introduction As technologies continue to advance, it is crucial to have secure and stable mechanisms for authentication to protect essential data from malicious access. Token-based authentication is a technique that has proven effective in curbing security threats, chiefly because it is easy and secure.
By Anna Shipman11 months ago in 01
Top Code Signing Mistakes and Solution to Prevent Software Attacks in 2025
Introduction In today’s digital age, implementing software security measures is not only crucial but also a time-consuming and expensive process. These measures are often carried out by humans who are susceptible to errors. These mistakes cause security breaches in the software, ultimately causing nasty consequences to the company’s revenue.
By Anna Shipman11 months ago in 01