Amazon EC2 Metadata Exposed Through Server-Side Request Forgery (SSRF) Attack
SSRF is rising as a top cloud threat, enabling attackers to access internal systems and steal credentials. Learn how to detect and defend against it.
On March 25, 2024, the National Security Agency (NSA) and the Cybersecurity and Infrastructure Security Agency (CISA) issued a joint advisory highlighting the increasing threat of Server-Side Request Forgery (SSRF) vulnerabilities. This advisory underscores the growing concern over SSRF, particularly in cloud environments where its exploitation can lead to significant security breaches.
What is Server-Side Request Forgery (SSRF)?
SSRF is a web application vulnerability that allows an attacker to induce the server-side application to make HTTP requests to an arbitrary domain of the attacker's choosing. This can lead to unauthorized access to internal systems, sensitive data exposure, and other malicious activities.
Threat of SSRF in Cloud Environments
While SSRF has been known to security professionals for years, its exploitation has become more prevalent with the widespread adoption of cloud services. In cloud environments like Amazon Web Services (AWS), SSRF vulnerabilities can be particularly dangerous. Attackers can exploit SSRF to access internal metadata services, retrieve temporary credentials, and potentially gain unauthorized access to cloud resources.
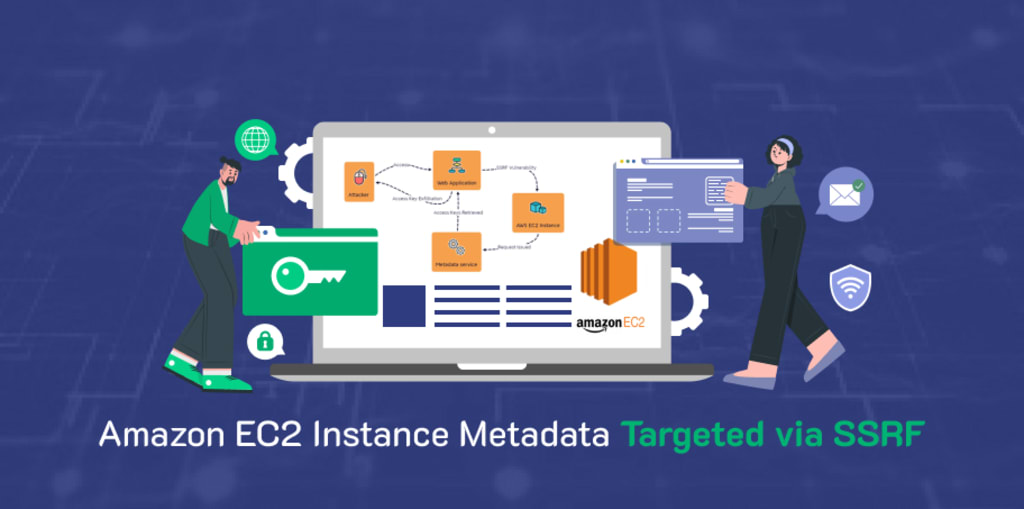
Exploiting EC2 Instance Metadata via SSRF
In AWS, each EC2 instance has access to a metadata service that provides information about the instance, including temporary security credentials. This service is accessible via a special IP address. If an application within the EC2 instance is vulnerable to SSRF, an attacker can exploit this to access the metadata service and retrieve sensitive information.
For example, an attacker could craft a request that tricks the vulnerable application into fetching data from the metadata service. This could include temporary security credentials that the attacker can then use to access other AWS services, potentially leading to a full compromise of the cloud environment.
Past SSRF Exploits
Several high-profile security incidents have involved SSRF vulnerabilities. In 2019, a former AWS employee exploited an SSRF vulnerability in Capital One's infrastructure to access over 100 million customer records. This breach highlighted how SSRF, combined with misconfigured security controls, can lead to significant data breaches.
More recently, advanced persistent threat (APT) groups, including nation-state actors, have been observed leveraging SSRF vulnerabilities for initial access and lateral movement within target networks. These attackers exploit improperly configured APIs, unrestricted outbound traffic, and trust relationships within internal networks to achieve their objectives.
Mitigating SSRF Vulnerabilities
To protect against SSRF attacks, organizations should implement the following best practices:
- Input Validation: Ensure that all user-supplied input is properly validated and sanitized to prevent malicious requests.
- Restrict Outbound Traffic: Limit the server's ability to make outbound requests, especially to internal services.
- Use Metadata Protection: In AWS, use Instance Metadata Service Version 2 (IMDSv2) to add an extra layer of protection against unauthorized metadata access.
- Implement Network Segmentation: Separate sensitive internal services from public-facing applications to reduce the attack surface.
- Monitor and Logging: Continuously monitor network traffic and maintain logs to detect and respond to suspicious activities promptly.
Conclusion
SSRF vulnerabilities pose a significant threat to modern cloud environments. As attackers become more sophisticated, it's crucial for organizations to understand the risks associated with SSRF and implement robust security measures to mitigate them. By staying informed and proactive, organizations can better protect their infrastructure and sensitive data from potential SSRF exploits.
About the Creator
Anna Shipman
Anna Shipman is a Cyber Security Consultant with a strong technical background and experience with a high analytical skillset. She has been involved in the information security industry for more than a decade.






Comments
There are no comments for this story
Be the first to respond and start the conversation.