cybersecurity
Our personal, digital, national and military security depend on a safe cyber space.
Hackers Target Insight Partners in Latest High-Profile Cyberattack
Introduction New York-based venture capital and private equity firm Insight Partners recently disclosed that it suffered a cybersecurity breach in January 2025 following a sophisticated social engineering attack. The firm, which manages over $90 billion in regulatory assets and has invested in more than 800 software and technology companies worldwide, confirmed the incident in a public statement issued on Tuesday.
By WIRE TOR - Ethical Hacking Services11 months ago in 01
MiTM and DoS Attacks Enabled by Critical Flaws in OpenSSH
Introduction OpenSSH has recently released security updates to address two critical vulnerabilities that expose SSH servers to machine-in-the-middle (MiTM) and denial-of-service (DoS) attacks. One of these vulnerabilities has remained undiscovered for over a decade. The security research team at Qualys identified and reported these issues to OpenSSH maintainers, demonstrating their potential exploitability.
By WIRE TOR - Ethical Hacking Services11 months ago in 01
Puran Crypto Recovery: The Best Crypto Recovery Experts Helping Victims Recover Lost Assets. AI-Generated.
Understanding Crypto Scams and the Need for Recovery Experts The world of cryptocurrency has opened new avenues for financial transactions, offering both opportunity and risk. While it's decentralized and secure, the anonymity of digital transactions has also led to a surge in crypto scams, where fraudsters devise elaborate schemes to siphon off investors' funds. In response, the demand for adept recovery experts has soared, and leading this charge in Canada is Puran Crypto Recovery.
By Micah Carter11 months ago in 01
The Ultimate Guide to Recovering Stolen Cryptocurrency Assets
Cryptocurrency theft is on the rise, with hackers exploiting security vulnerabilities to steal digital assets from unsuspecting users. If you’ve fallen victim to crypto fraud or hacking, don’t panic—there are ways to recover your stolen funds. This guide will walk you through the steps you need to take to safely recover your stolen cryptocurrency and introduce Recuva Hacker Solutions, a trusted company specializing in asset recovery.
By forbes Caroline11 months ago in 01
Lost Crypto? How Blockchain Investigation Helped Trace 180,000 USDT
The prevalence of cryptocurrency scams has risen sharply, creating challenges for victims and investigators alike. Sophisticated fraud techniques have left individuals and institutions struggling to recover stolen funds.
By Micah Carter11 months ago in 01
Choosing the Best IT Support Provider in London: Key Questions Every Business Should Ask
When selecting the best IT support provider in London, businesses must consider more than technical expertise. The right provider should offer a blend of proficiency, reliability, and tailored services to align with your specific needs. Whether you are a growing London SMB or an established enterprise, finding a provider that offers scalable IT solutions, proactive support, and robust security is crucial for long-term success. Below are key questions to help guide your decision-making process.
By Fiora Hart11 months ago in 01
How to Choose the Right Replacement Keys for Your Laptop
When a laptop key breaks or stops working, it can be frustrating. Whether you’ve spilled coffee on your keyboard, dropped something on it, or just worn out the keys from years of use, there’s no need to panic. Replacing individual keys on your laptop is a relatively easy and cost-effective way to get your device back in working order. However, choosing the right replacement keys can sometimes be tricky. In this article, we’ll guide you through the process of selecting the right replacement keys for your laptop, with helpful tips and considerations to make sure you get the right fit for your device.
By Seo Musarrat11 months ago in 01
X Platform Blocks Signal Contact Links, Labels Them as Malicious
Introduction Social media platform X (formerly known as Twitter) has started blocking links to "Signal.me," a URL used by the Signal encrypted messaging app to share account details. This unexpected move has raised concerns among privacy advocates, journalists, and users of the secure messaging service. The platform now flags these links as malicious, preventing users from posting them in public posts, direct messages, or even profile bios.
By WIRE TOR - Ethical Hacking Services11 months ago in 01
South Korea Takes Action: DeepSeek AI App Downloads Paused Over Privacy Risks
Introduction DeepSeek, a Chinese artificial intelligence startup, has temporarily halted downloads of its chatbot applications in South Korea due to privacy concerns raised by local authorities. The move follows an investigation by South Korea's Personal Information Protection Commission, which identified issues related to data transparency and the handling of personal information. This development reflects a broader global conversation about data privacy, AI ethics, and the responsibilities of AI-driven platforms in safeguarding user data.
By WIRE TOR - Ethical Hacking Services11 months ago in 01
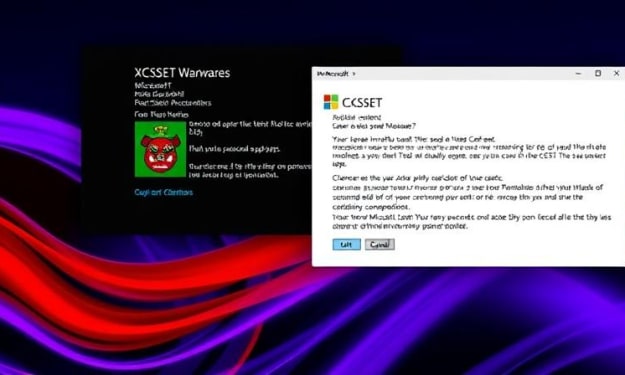
Microsoft Sounds Alarm on macOS Malware Stealing Crypto Assets
Introduction A new and more advanced variant of the XCSSET macOS modular malware has surfaced, marking a significant development in its evolution. This malware, which primarily targets Apple users, has been active for at least five years. The latest improvements indicate a renewed focus on enhancing its capabilities for data theft, particularly targeting sensitive information such as digital wallets and data from the Notes application.
By WIRE TOR - Ethical Hacking Services11 months ago in 01