WIRE TOR - Ethical Hacking Services
Bio
WIRE TOR is a Cyber Intelligence Company that Provides Pentest & Cybersecurity News About IT, Web, Mobile (iOS, Android), API, Cloud, IoT, Network, Application, System, Red teaming, Social Engineering, Wireless, And Source Code.
Stories (108)
Filter by community
Mirai Malware Targets Unpatched TBK DVRs in Global Botnet Campaign
A newly emerged variant of the infamous Mirai malware botnet is actively exploiting a command injection vulnerability in TBK DVR-4104 and DVR-4216 devices. This vulnerability, tracked as CVE-2024–3721, enables attackers to gain unauthorized control over the compromised digital video recorders (DVRs), potentially enlisting them into powerful botnets used for cyberattacks.
By WIRE TOR - Ethical Hacking Services9 months ago in 01
🚨The North Face Hit by Credential Stuffing Attack in April 2025, Exposing Customer Data🚨
The North Face Data Breach: April 2025 Credential Stuffing Attack Exposes Customer Data The North Face Data Breach: April 2025 Credential Stuffing Attack Exposes Customer Data.
By WIRE TOR - Ethical Hacking Services9 months ago in 01
🚨Cisco IOS XE Arbitrary File Upload Vulnerability Exploited🚨
Critical Cisco IOS XE Arbitrary File Upload Vulnerability Exploited A newly disclosed critical flaw in Cisco IOS XE, tracked as CVE-2025–20188, is raising alarms across the cybersecurity community. Technical details now made public demonstrate how attackers can exploit the bug to achieve remote code execution (RCE), placing enterprise wireless infrastructure at serious risk. Although a complete plug-and-play exploit is not yet available, the detailed analysis by researchers leaves very little to the imagination. This puts the burden on CISOs and security teams to act quickly before threat actors operationalize the exploit.
By WIRE TOR - Ethical Hacking Services9 months ago in 01
Apple Removes iCloud End-to-End Encryption in the UK Following Government Pressure
Apple has made the controversial decision to no longer offer its optional iCloud end-to-end encryption feature, Advanced Data Protection (ADP), in the United Kingdom. The move follows demands from the UK government for a backdoor to access encrypted cloud data, sparking a heated debate over digital privacy, national security, and the future of encrypted communications in the country.
By WIRE TOR - Ethical Hacking Servicesabout a year ago in 01
Hackers Target Craft CMS: CISA Confirms Code Injection Flaw Exploitation
The U.S. Cybersecurity & Infrastructure Security Agency (CISA) has issued a warning about a remote code execution (RCE) vulnerability in Craft CMS that is being actively exploited in attacks. The flaw, tracked as CVE-2025-23209, is classified as high severity with a CVSS v3 score of 8.0 and affects Craft CMS versions 4 and 5.
By WIRE TOR - Ethical Hacking Servicesabout a year ago in 01
Crypto Giant Bybit Hit by $1.46 Billion ETH Cold Wallet Heist
In a shocking cyber heist, cryptocurrency exchange Bybit has confirmed that an unknown attacker has stolen over $1.46 billion worth of cryptocurrency from one of its Ethereum (ETH) cold wallets. The incident, now regarded as the largest crypto theft in history, has sent shockwaves throughout the digital asset industry.
By WIRE TOR - Ethical Hacking Servicesabout a year ago in 01
US Telecom Networks Hacked: Chinese Cyber Spies Use Sophisticated Malware
The Chinese state-sponsored hacking group known as Salt Typhoon has been identified as using a custom utility called JumbledPath to stealthily monitor network traffic and potentially capture sensitive data. These cyberattacks have targeted major U.S. telecommunication providers, raising significant concerns about national security and data privacy.
By WIRE TOR - Ethical Hacking Servicesabout a year ago in 01
WinRAR's New Update Boosts Privacy by Removing Windows Metadata
Introduction WinRAR, one of the most widely used file archivers and compression tools for Windows, has just received a significant update with the release of version 7.10. This new update introduces several features aimed at improving performance, usability, and security. Among these, one of the most notable changes is the ability to strip sensitive metadata from the Mark-of-the-Web (MoTW) alternate data stream, increasing privacy for users who frequently download and share files.
By WIRE TOR - Ethical Hacking Servicesabout a year ago in 01
Black Basta Ransomware Gang Exposed: Internal Chat Logs Leak Online
Leaked Chat Logs Expose Internal Conflict and Operations An unknown leaker has released what they claim to be an archive of internal Matrix chat logs belonging to the Black Basta ransomware operation. The leaked information sheds light on the gang’s internal operations, conflicts, and possible motivations behind their cybercriminal activities.
By WIRE TOR - Ethical Hacking Servicesabout a year ago in 01
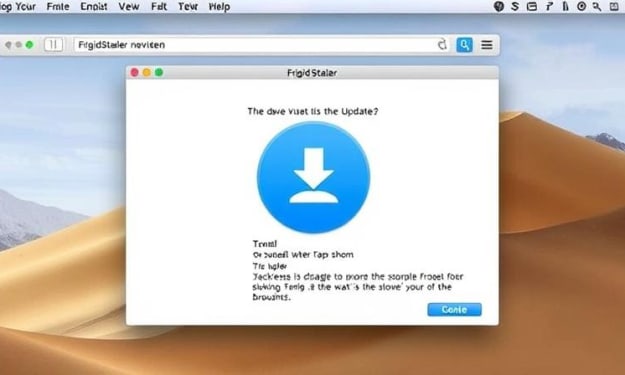
Beware of Fake Updates: FrigidStealer Malware Targets Mac Devices
The FakeUpdate malware campaigns are becoming increasingly complex, with two additional cybercrime groups, TA2726 and TA2727, now involved in delivering a new macOS infostealer malware called FrigidStealer. These threat actors are running campaigns that distribute malware via fake browser update notifications, affecting not only Mac users but also Windows and Android users.
By WIRE TOR - Ethical Hacking Servicesabout a year ago in 01
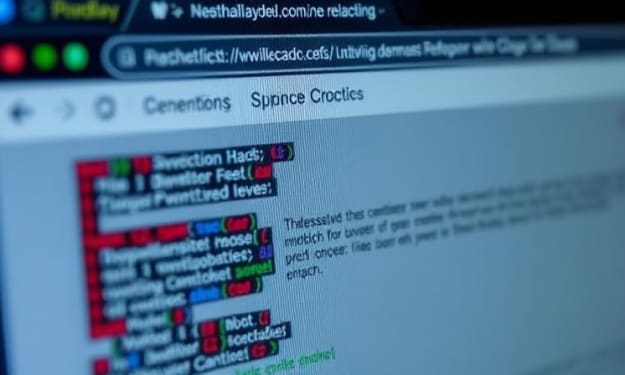
Cybercriminals Use Invisible Unicode to Mask JavaScript in Phishing Attacks
A new JavaScript obfuscation technique leveraging invisible Unicode characters to represent binary values is actively being used in phishing attacks. This novel method, first disclosed in October 2024, has been quickly adopted by threat actors targeting affiliates of an American political action committee (PAC).
By WIRE TOR - Ethical Hacking Servicesabout a year ago in 01