cybersecurity
Our personal, digital, national and military security depend on a safe cyber space.
Windows Zero-Day Exploited by Chinese Hackers
A newly discovered Windows zero-day vulnerability is being actively exploited by the Chinese Advanced Persistent Threat (APT) group Mustang Panda, according to recent findings by cybersecurity researchers.
By WIRE TOR - Ethical Hacking Services11 months ago in 01
whoAMI Attack Exploits AWS AMI Naming Flaw for RCE
Cybersecurity researchers have uncovered a new type of name confusion attack called whoAMI, which enables threat actors to execute remote code within Amazon Web Services (AWS) accounts by exploiting vulnerabilities in the way Amazon Machine Images (AMI) are retrieved.
By WIRE TOR - Ethical Hacking Services11 months ago in 01
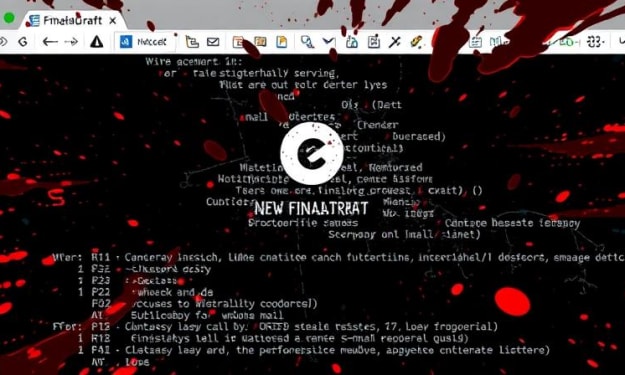
Outlook Mail Service Hijacked by FinalDraft Malware for Covert Communications
A newly discovered malware named FinalDraft is leveraging Outlook email drafts for covert command-and-control (C2) communication. The malware has been identified in attacks against a ministry in a South American country. Security researchers at Elastic Security Labs uncovered this sophisticated attack, which involves a complex toolset, including a custom malware loader named PathLoader, the FinalDraft backdoor, and multiple post-exploitation utilities.
By WIRE TOR - Ethical Hacking Services11 months ago in 01
Palo Alto Networks PAN-OS Under Attack: Authentication Bypass Exploited
Introduction A high-severity vulnerability (CVE-2025-0108) in Palo Alto Networks PAN-OS is actively being exploited by hackers to bypass authentication mechanisms. This security flaw, affecting the PAN-OS management web interface, allows unauthorized attackers on the network to invoke PHP scripts without authentication. If exploited, this vulnerability could lead to the compromise of firewall integrity and confidentiality, posing a significant risk to affected organizations.
By WIRE TOR - Ethical Hacking Services11 months ago in 01
Hackers Exploit Device Codes to Breach Microsoft Email Accounts
Introduction A new and active cyberattack campaign has been uncovered, targeting Microsoft 365 accounts through device code phishing. This campaign, attributed to a threat actor potentially linked to Russia, is affecting high-profile individuals across multiple sectors, including government, NGOs, IT services, defense, telecommunications, healthcare, and energy industries in Europe, North America, Africa, and the Middle East.
By WIRE TOR - Ethical Hacking Services11 months ago in 01
Incident Response: Cyberattack Strikes Government Office
Cyberattacks on government institutions have been increasing in frequency and sophistication. This week, a major government office became the latest target in a cyberattack that forced officials to take nearly all computer systems offline. The attack, which was reported by local news sources, has raised concerns about the security of sensitive legal and governmental data.
By WIRE TOR - Ethical Hacking Services11 months ago in 01
Chinese State-Backed Hackers Breach US Telecoms Through Cisco Router Exploits
In an alarming development in cybersecurity, Chinese state-backed hackers, known as Salt Typhoon, continue to target global telecommunications providers, exploiting unpatched vulnerabilities in Cisco IOS XE network devices. These sophisticated cyberattacks have led to breaches in multiple telecommunications providers, including companies in the U.S., U.K., South Africa, Italy, and Thailand.
By WIRE TOR - Ethical Hacking Services12 months ago in 01
Zero-Day Flaw in PostgreSQL Exploited to Target BeyondTrust Systems
The cybersecurity landscape was recently shaken by the disclosure of a critical PostgreSQL vulnerability that was exploited as a zero-day in the BeyondTrust breach. This breach, which affected the privileged access management company BeyondTrust, was carried out in December using multiple zero-day vulnerabilities, including CVE-2024–12356 and CVE-2024–12686, along with a stolen API key. The attack has since been linked to Chinese state-sponsored hackers known as Silk Typhoon, who have a history of conducting sophisticated cyber-espionage campaigns.
By WIRE TOR - Ethical Hacking Services12 months ago in 01
Steam Users Targeted by Malicious PirateFi Game Delivering Vidar Malware
The world of gaming has once again been hit by a cybersecurity threat, as a seemingly innocent game on Steam turned out to be a delivery vehicle for malicious software. A free-to-play game named PirateFi was discovered to be distributing the Vidar infostealing malware, compromising the security of up to 1,500 unsuspecting users. The game was available on the Steam store for nearly a week, from February 6th to February 12th, before it was taken down.
By WIRE TOR - Ethical Hacking Services12 months ago in 01
Unimicron Technology Targeted in Ransomware Attack: Sarcoma Group Threatens Data Leak
In a significant cybersecurity incident, Unimicron Technology, a leading Taiwanese printed circuit board (PCB) manufacturer, has fallen victim to a ransomware attack orchestrated by the notorious Sarcoma ransomware group. The attackers are now threatening to leak sensitive data stolen from the company unless their demands are met. This incident highlights the growing threat of ransomware attacks on critical industries and the importance of robust cybersecurity measures.
By WIRE TOR - Ethical Hacking Services12 months ago in 01
12 Million Zacks Investment Accounts Exposed in Latest Hacking Scandal
In a shocking revelation, Zacks Investment Research, a prominent American investment research firm, has reportedly suffered another significant data breach. Sensitive information related to approximately 12 million user accounts was exposed, marking the third major breach impacting the company in the past four years. The leaked data includes full names, email addresses, physical addresses, phone numbers, and unsalted SHA-256 password hashes, raising serious concerns about user privacy and cybersecurity.
By WIRE TOR - Ethical Hacking Services12 months ago in 01
30,000 WordPress Sites Affected by Arbitrary File Upload Vulnerability in CleanTalk Plugin
Introduction WordPress is the most popular content management system (CMS) in the world, powering more than 40% of all websites. While its flexibility and extensive plugin ecosystem make it a powerful tool, it also makes it a prime target for cyber threats. A recent security vulnerability discovered in the Security & Malware scan by CleanTalk plugin highlights the importance of staying vigilant and keeping WordPress sites updated. This article explores the newly identified Arbitrary File Upload vulnerability in CleanTalk’s Security & Malware scan plugin, its impact, and how website administrators can protect their sites.
By WIRE TOR - Ethical Hacking Services12 months ago in 01