10 OSINT Techniques Private Investigators Can’t Afford to Ignore
Discover the top 10 OSINT techniques used by modern investigative agencies, plus how transcription can turn audio into actionable, court-ready intelligence.

In the world of modern investigations, speed and precision are everything. Whether you're a private investigator tracking a cheating spouse, a corporate team uncovering internal fraud, or a law enforcement unit chasing leads across the web, your success depends on how fast and how well you gather and connect the dots.
This is where OSINT, or Open Source Intelligence, becomes your best ally. We're talking about publicly available data, including emails, websites, social media, breach dumps, podcasts, and even TikTok videos. But it's not just about gathering it, it's about making sense of it, quickly.
Here are 10 OSINT techniques every investigator should have in their toolkit. And yes, you'll see how transcription fits in as a powerful, often overlooked, tool for gathering intelligence.
1. Precision Google Searches (also called Google Dorking)
You’d be surprised how much people leave exposed online. Using smart search operators like site:, filetype:, or intitle:, investigators can dig up sensitive documents, login pages, directories, and even spreadsheets that are just sitting there in the open.
Want to find a company’s internal budget report that someone mistakenly uploaded? Try this:
site:example.com filetype:xls budget
This isn’t hacking, it’s public information. But it takes finesse. With the right query, you can get what you’re looking for in under 30 seconds.
2. Social Media Monitoring That Actually Works
People share everything these days, from what they’re eating and where they’re going to who they’re with. If you're not monitoring platforms like Facebook, Instagram, X (Twitter), Reddit, or even LinkedIn, you might be missing critical clues.
Let’s say a subject claims to be in New York. A quick Instagram scan shows they just posted from a bar in Miami. That one post could be the break you need.
Use tools like TweetDeck, Social-Searcher, or advanced platforms like Echosec to track hashtags, keywords, and geotags in real time.
3. Infrastructure Mapping, The Digital Footprint
Every email, domain, or IP address tells a story. Tools like Shodan, Censys, and SecurityTrails let you map out the technical infrastructure behind your target, including servers they use, devices they own, and domains they’ve registered.
For example, a suspect may run a shady e-commerce site under a fake business name. But a simple lookup might reveal they used the same SSL certificate on another site tied to their real identity.
When combined with other techniques, this kind of mapping helps build airtight digital profiles.
4. Transcription, Turning Voices Into Evidence
Let’s pause here because this one’s a game-changer for investigators.
Imagine you’ve got hours of recorded interviews, surveillance audio, or call logs. Listening to them all takes forever. But transcribe them, and suddenly you can search for keywords, highlight important names, and create court-ready documentation.
This is especially important for time-sensitive investigations. Need to find out if a suspect mentioned a location? A simple Ctrl+F in the transcript can beat hours of listening.
Pro tip: Always choose human investigative transcription when accuracy matters. Automated tools miss context, especially with background noise, accents, or overlapping voices. Services like GMR Transcription specialize in secure, confidential transcription for investigators, law firms, and agencies.
5. Reverse Image Search, Every Pixel Tells a Story
That profile picture you're looking at might have a past.
Upload it to Google Images, Yandex, or TinEye, and you might find the same face used on multiple fake accounts. Reverse image search is powerful in cases involving romance scams, identity fraud, or even fake company listings.
Even altered or cropped photos can sometimes be traced back to their original context.
6. Username Enumeration, Unmasking the Alias
Most people reuse usernames. That online handle from a gaming forum could link back to a Reddit account, a comment thread on a news article, or even a dating profile.
Tools like Sherlock, Maigret, or WhatsMyName automate this process, scanning hundreds of platforms in minutes.
Here’s where transcription comes into play again. If you recorded a suspect mentioning an alias during an interview, that one word could unlock an entire network of online activity.
7. Leaked Data, A Treasure Trove of Clues
Data breaches can be messy, but for investigators, they’re often pure gold.
By entering an email address into tools like HaveIBeenPwned, DeHashed, or GhostProject, you can uncover old logins, reused passwords, and even full profile details.
Say you're chasing someone involved in financial fraud. A breached credential might show up on a hacked trading platform or cryptocurrency site. That could give you motive, timeline, and connection in one stroke.
8. Scraping the Web (Legally) to Save Hours
You don’t have time to copy and paste hundreds of posts or listings. That’s where web scraping tools like Scrapy, Octoparse, or BeautifulSoup come in.
These tools let you automate the extraction of data from forums, business listings, or social feeds. Once gathered, that information can be analyzed or cross-checked against content from your case files or transcribed evidence.
Just make sure you're operating within legal and ethical limits.
9. GeoOSINT, Verifying Where It Happened
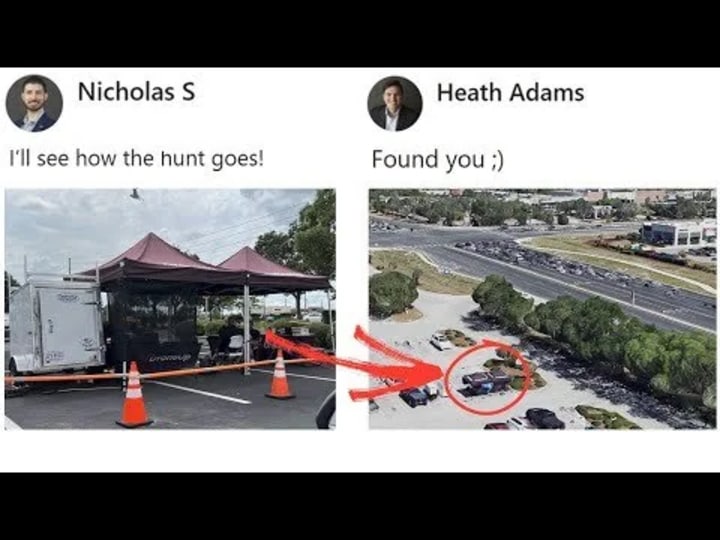
You don’t always need GPS data to confirm a location. Sometimes, shadows, skylines, or weather conditions in a photo or video can do the trick.
With tools like SunCalc, Google Earth, and Sentinel Hub, you can geo-locate and time-stamp content based on environmental clues.
If a suspect posts a video claiming to be in Chicago at 2 PM, but the lighting and sun angle suggest otherwise, that’s your leverage.
10. Monitoring Paste Sites and the Dark Web
Not all leaks happen on the surface web. Pastebin-style sites and dark web forums are often the first places where compromised data shows up.
Using platforms like SpiderFoot or IntelligenceX, you can set alerts for names, email addresses, or keywords tied to your case. It’s like setting a digital tripwire that notifies you the moment new data appears.
This level of early detection can be the difference between catching a criminal and chasing a cold trail.
Final Thoughts
Every one of these OSINT techniques has the potential to uncover that one clue you need. But it’s not about doing everything. It’s about doing the right things quickly and efficiently.
Transcription, especially, can transform audio recordings into searchable, scannable intelligence that you can cross-reference across multiple platforms. For private investigators, it’s no longer a nice-to-have. It’s essential.
About the Creator
Beth Worthy
Beth Worthy is President of GMR Transcription Services, Inc., a U.S. company offering 100% human transcription, translation, and proofreading for academic, business, legal, and research clients.






Comments
There are no comments for this story
Be the first to respond and start the conversation.