The Top Cyber Security Threats of 2023 and How to Protect Yourself
Stay Safe Online: A Guide to Protecting Yourself from the Latest Cyber Attacks

The Top Cyber Security Threats Of 2023 and How to Protect Yourself:

As technology continues to evolve and more of our daily activities move online, the risk of cyber attacks is growing. It's important to be aware of the most pressing cyber security threats so you can take steps to protect yourself. Here are the top cyber security threats to watch out for in 2023:
RANSOMEWARE:
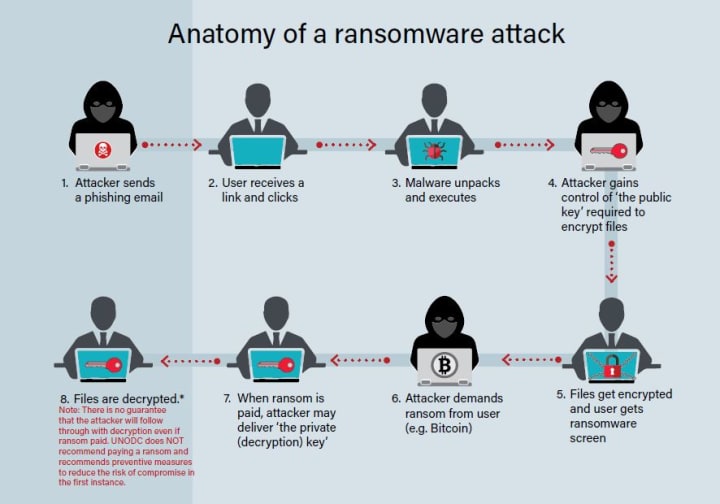
Ransomware is a type of malware that infects a computer or network and encrypts important files, making them inaccessible to the victim. The attacker then demands payment (often in the form of cryptocurrency) in exchange for the decryption key, hence the name "ransomware."
• Ransomware attacks can cause significant damage to both individuals and organizations. In addition to the cost of paying the ransom, victims may also incur expenses related to downtime, data recovery, and repairs to the affected systems.
• To protect against ransomware attacks, it's important to follow best practices for cybersecurity, such as:
• Keeping your software and devices up-to-date with the latest security patches.
• Using strong and unique passwords, and enabling two-factor authentication where possible.
• Backing up important data regularly to an external and disconnected source.
• Avoiding suspicious emails, attachments, and links, especially those related to unsolicited invoices, job offers, and other urgent requests.
• Installing and maintaining robust anti-virus and anti-malware software.
• If you do become a victim of a ransomware attack, do not pay the ransom. Instead, contact law enforcement and seek the help of cybersecurity experts to assist in your recovery.
PHISING SCAMS :

Phishing scams are a type of cyber attack that aim to trick individuals into revealing sensitive information, such as passwords, credit card numbers, and other personal data. These scams often take the form of fake emails or websites that appear to be from a trustworthy source, such as a bank, a well-known company, or a government agency.
Phishing scams are typically designed to be as convincing as possible, and attackers often use social engineering techniques to manipulate their targets into taking action. For example, a phishing email might claim to be from a bank and ask the recipient to log in to their account to resolve a security issue. The link in the email would lead to a fake website that looks like the bank's real website, but is actually controlled by the attacker.
To protect against phishing scams, it's important to be aware of the warning signs and to take the following steps:
• Verify the authenticity of emails and websites before entering any personal information.
• Be cautious of unsolicited emails or links, especially those that contain urgent or threatening language.
• Always hover over links to see the URL before clicking on them, and look for the padlock symbol in the address bar to verify the security of a website.
• Keep your software and devices up-to-date with the latest security patches.
• Use strong and unique passwords, and enable two-factor authentication where possible.
• By following these steps and being vigilant against phishing scams, you can help protect your personal and financial information from cyber criminals.
CLOUD SECURITY:
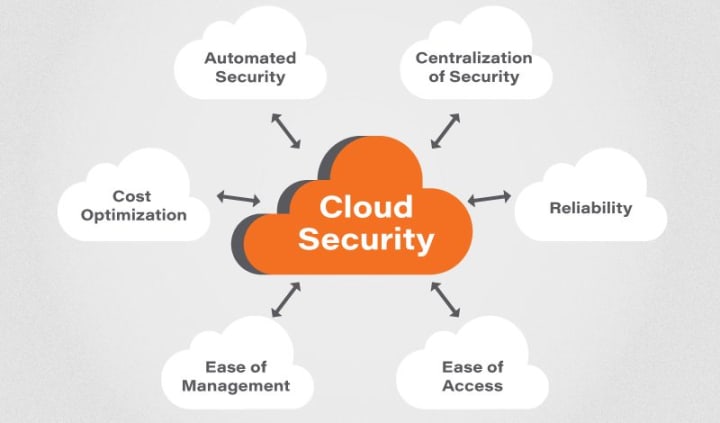
Cloud security refers to the set of measures and technologies used to protect data, applications, and infrastructure that are hosted in the cloud. As more organizations adopt cloud computing, it's increasingly important to ensure that the cloud environment is secure and that sensitive data is protected from unauthorized access, theft, and other security threats.
Here are some common cloud security concerns and how they can be addressed:
• Data Privacy: Data privacy is a major concern for organizations that store sensitive information in the cloud. Encryption and other data protection measures can help ensure that only authorized users have access to sensitive data.
• Data Loss: Data loss in the cloud can occur due to hardware failure, human error, or malicious activity. Regular backups and disaster recovery plans can help minimize the risk of data loss.
• Account Hijacking: Cloud service providers offer multiple accounts, making it possible for an attacker to take over a legitimate account and gain access to sensitive data. Strong passwords and multi-factor authentication can help prevent account hijacking.
• Insufficient Access Controls: Improper access controls can allow unauthorized users to access sensitive data. It is important to implement role-based access controls, monitor user activity, and regularly review access permissions.
• Compliance: Organizations must comply with various regulations, such as the EU's General Data Protection Regulation (GDPR) and the Payment Card Industry Data Security Standard (PCI DSS), when storing and processing sensitive data in the cloud. Cloud service providers can help ensure compliance with these regulations.
To ensure the security of cloud-based systems, organizations should adopt a comprehensive cloud security strategy that includes secure architecture, risk assessment, incident response planning, and regular security testing and monitoring. Working with a reputable cloud service provider can also help ensure the security of cloud-based systems and protect against potential security threats.
IoT SECURITY:

Internet of Things (IoT) security refers to the measures and technologies used to protect IoT devices, networks, and the data generated by these devices. With the increasing number of connected devices, IoT security has become a critical issue for organizations and individuals alike.
Here are some common IoT security concerns and how they can be addressed:
• Device Vulnerabilities: Many IoT devices have security vulnerabilities that can be exploited by attackers. Regular software updates, secure boot processes, and strong passwords can help mitigate these vulnerabilities.
• Insecure Network Communications: IoT devices communicate with each other and with cloud-based services over the internet, which can make them vulnerable to cyber attacks. Secure protocols, such as SSL/TLS, and encrypted communications can help prevent unauthorized access to sensitive data.
• Lack of Physical Security: IoT devices are often deployed in environments that are accessible to the public, such as homes, offices, and public spaces. Tampering with these devices can compromise their security. Physical security measures, such as enclosures and locks, can help prevent unauthorized access to these devices.
• Unsecured Data: IoT devices generate large amounts of data, which can include sensitive information. Encryption, secure storage, and access controls can help protect this data from unauthorized access and theft.
• Malware: IoT devices can be infected with malware, which can allow attackers to take control of these devices and steal sensitive data. Regular security scans and software updates can help prevent malware infections.
To ensure the security of IoT systems, it's important to adopt a comprehensive IoT security strategy that includes secure design, risk assessment, incident response planning, and regular security testing and monitoring. Organizations should also work with trusted IoT service providers and hardware manufacturers to ensure the security of IoT devices and networks
AI-POWERED ATTACKS :

Artificial intelligence (AI) has the potential to revolutionize the way cyber attacks are carried out. AI-powered attacks are automated and can evolve quickly, making them difficult to detect and defend against.
Here are some common AI-powered attack scenarios:
• Deepfakes: Deepfake technology can be used to create realistic, fake videos and images that can be used to spread disinformation and manipulate public opinion.
• AI-Powered Phishing: AI can be used to automate phishing attacks and make them more sophisticated and convincing. This can result in more victims falling for these attacks and exposing sensitive information.
• AI-Powered Malware: AI can be used to automate the distribution of malware, making it easier for attackers to infect large numbers of devices and steal sensitive information.
• AI-Powered DDoS Attacks: AI can be used to automate the generation of large volumes of traffic, which can be used to overload and bring down websites and networks.
• To defend against AI-powered attacks, organizations should adopt a proactive and multi-layered approach that includes:
• User education and awareness: Employees should be educated on how to identify and avoid AI-powered attacks.
• Advanced threat protection: Advanced threat protection solutions can help detect and prevent AI-powered attacks by using machine learning algorithms to analyze network traffic and identify malicious activity.
• Network segmentation: Segregating sensitive data and systems from the rest of the network can help limit the damage caused by an AI-powered attack.
• Regular security testing: Regular security testing and monitoring can help organizations identify potential vulnerabilities and prevent AI-powered attacks.
By implementing these measures, organizations can better defend against AI-powered attacks and protect sensitive information from falling into the hands of cybercriminals.
To protect yourself from these cyber security threats, it's important to follow best practices for online safety. Here are some steps you can take:
• Use strong passwords and two-factor authentication.
• Keep your software and devices up to date with the latest security patches.
• Be cautious of emails and websites that look suspicious or ask for personal information.
• Use antivirus software and a firewall to protect your devices.
• Backup your important data regularly in case of a ransomware attack.
By being aware of these threats and taking steps to protect yourself, you can help ensure your online security and privacy.
About the Creator
BHUVANESH
Gather And Share Informative Social Messages




Comments (1)
NICE IMFORMATION