Fizza Jatniwala
Stories (10)
Filter by community
The Role of Penetration Testing in Compliance: Meeting HIPAA, PCI-DSS, and GDPR Standards
While electronic threats continue to be better devised, organizations with such sensitive information are always expected to be on tightrope adherence to very high strict regulatory standards. This therefore includes HIPAA, PCI-DSS, and GDPR amongst many other standards for any organization. One of the strongest ways of achieving and maintaining these standards of compliance is through penetration testing, a process for identifying vulnerabilities before the malicious actors find them. If you have an interest in pursuing a career in cybersecurity or are learning about cybersecurity in Thane, it's useful to understand how penetration testing works in regulatory compliance.
By Fizza Jatniwalaabout a year ago in 01
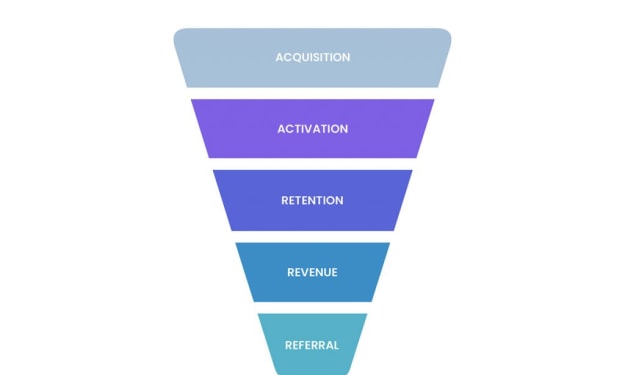
Optimizing the Funnel: Strategies to Increase Retention at Each Stage
Retention at all stages of the marketing funnel has become a critical factor in the highly competitive digital landscape of today. Each step of the funnel is crucial in taking the user through it-from the very start when they just become interested to a long time from then. It not only increases conversions but also brings in relationships that are long-lasting with your audience. For businesses and marketers in Hyderabad who will excel with these techniques, a digital marketing course in Hyderabad gives you the essential tools to understand and improve each stage of the funnel.
By Fizza Jatniwalaabout a year ago in 01
Disaster Recovery Solutions Across Azure and AWS: A Comparative Guide
In this digitally-enabled world, business needs to prepare for the unthinkable—be it a natural disaster, a cyber attack, or human error. For business resilience, it is advisable to leverage DR strategies that would minimize downtime and data loss and prevent a halt in business. Two of the leading cloud service providers, Azure and AWS, offer robust disaster recovery solutions that help organizations plan better for the worst.
By Fizza Jatniwalaabout a year ago in 01
Multi-Tenant vs. Single-Tenant Cloud: Pros and Cons for Your Business Needs
With the rise of cloud computing and the chaos it has created in the operations of businesses, the multi-tenant and the single-tenant cloud architectures become absolutely imperative for any organization to choose from. Both the models have their respective advantages but also bring their own set of trade-offs. Understanding the concept of these models helps businesses make the right infrastructure investment not only in line with their needs but also budgetary requirements coupled with security.
By Fizza Jatniwalaabout a year ago in 01
How to Use Metasploit Effectively for Network Penetration Testing
Metasploit is one of the most powerful and popular tools used by cybersecurity professionals in network penetration testing. As an open source platform, it develops a comprehensive framework in discovering, exploiting, and validating vulnerabilities across networks and systems. The article explains how to use Metasploit effectively for network penetration testing and why learning Metasploit can be an essential skill if one is studying in the field of cybersecurity.
By Fizza Jatniwalaabout a year ago in 01
How to Create a Winning Digital Marketing Strategy for 2024
By 2024, the digital marketing landscape is now moving faster than ever. New technologies, changes in consumer behavior, and new market trends have brought to bear the absolute need for winning digital marketing strategy. Whoever you are, a seasoned marketer or entering this realm for the first time, knowing the core elements of a good strategy will help navigate through these changes. In this blog, we will discuss the essential ingredients of a winning digital marketing strategy and also how to adopt them. If you're serious about learning more on this subject, you can browse for a digital marketing course.
By Fizza Jatniwalaabout a year ago in 01
Cybersecurity for Cloud Computing: Best Practices for Ethical Hackers to Ensure Cloud Security
Many organizations are still migrating their data and services to cloud platforms because cloud computing is the new backbone for digital transformation. It offers scalability, cost efficiency, and flexibility, among many advantages presented; however, it has unique cybersecurity challenges, which create common threats such as misconfigurations, unauthorized access, and data breaches.
By Fizza Jatniwalaabout a year ago in 01
The Evolution of AutoML: Are Data Scientists Becoming Obsolete?
Evolution of AutoML: Are Data Scientists Becoming Obsolete? AutoML is a technological advancement that has seen the machine learning field transform significantly over the last few years. Generally, the idea behind AutoML is to reduce and automate tasks that were too complex, hence making it easier to apply machine learning in such contexts. While this development raises questions pertaining to the future of data science, it is necessary that one knows more about the subtleties of AutoML and what this technique promises. Any person interested in doing a data science course in Mumbai needs to know where AutoML has been and where it will take the landscape of data science.
By Fizza Jatniwalaabout a year ago in 01
The Role of AI in Defending Against Cyber Attacks
As cyber threats continue to evolve at scale and complexity, businesses and organizations have been unable to keep track with the tactics that upgrade hackers. Traditional methods of cyber protection are valuable but prove largely inadequate against advanced cyberattacks. In response, Artificial Intelligence stands out as a significant tool that can enhance the security mechanism for protection. Through real-time review of vast amounts of data, detecting patterns, and predicting potential attacks, AI has become the current state-of-the-art feature in security strategies.
By Fizza Jatniwalaabout a year ago in 01
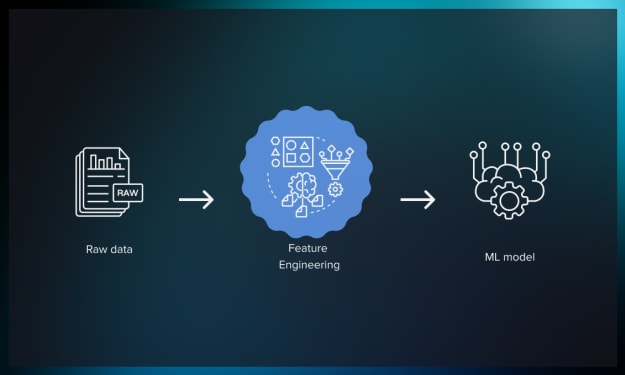
How Feature Engineering Drives Success in Machine Learning
The Performance of any model in the arena of machine learning critically depends on the quality of the data going into it. Model selection and algorithms are important, but feature engineering is that unsung hero, which can really make or break your machine learning project. If one is thinking about getting enrolled in a data science course, one really needs to learn about feature engineering in order to be good at machine learning.
By Fizza Jatniwalaabout a year ago in 01