how to
How tos for tech whizes and luddites alike; tips, tricks and shortcuts to optimize your computer, smartphone or internet mastery.
The Accessibility Crisis of 2026: What No One Wants to Admit
Every January, the internet fills with glossy predictions about the future - tech trends, workplace trends, fashion trends, AI trends. But there’s one category that rarely makes the list, even though it affects millions of people every single day:
By Tracy Stine5 days ago in 01
How to Mask Your IP for Privacy and Security
Every click, every search, every download leaves a digital footprint, and websites, advertisers, and sometimes even hackers can trace you through your IP address. The good news is that you don’t have to stay exposed. Hiding your IP address is simpler than most people think, and doing it correctly can protect your privacy, secure your data, and even give you access to content that was previously unavailable. Next, we’ll take a look at the different ways to hide your IP and how to choose the method that works best for you.
By Swiftproxy5 days ago in 01
Lauren Sánchez’s Bikini Top Hangs by Just Strings in Yacht Photos
Lauren Sánchez showed off her bold style in a bikini top featuring delicate strings. As reported by Page Six, the former journalist was seen on a luxury yacht along with Jeff Bezos, Leonardo DiCaprio, and his partner Vittoria Ceretti.
By Dena Falken Esq6 days ago in 01
Ethereum Price Soars Above $3200 as Jeff Bezos Announces Space Travel Payment — Can It Rocket Higher?
Key Takeaways Jeff Bezos’ space company has expanded crypto payments to include Ethereum. Ethereum’s price rally has been driven by optimism around the Fusaka upgrade and renewed institutional demand via ETF inflows.
By Dena Falken Esq6 days ago in 01
The Real Methods of Gmail Hacking: How Accounts Are Compromised and How to Protect Yourself. AI-Generated.
The Illusion of Invulnerability A Gmail account is more than just an email inbox—it's a digital passport to our online identity, connecting our social media, financial services, cloud storage, and professional communications. Many users operate under the dangerous assumption that Google's security is impenetrable, but the reality is that human error and sophisticated attacks create vulnerabilities that hackers exploit daily. This comprehensive guide will explore the actual methods used to compromise Gmail accounts, examine the tools employed by malicious actors, and provide actionable strategies to fortify your digital presence against these threats.
By Alexander Hoffmann6 days ago in 01
The Real Methods of Outlook Hacking: How Accounts Are Compromised and How to Protect Yourself. AI-Generated.
Microsoft Outlook, with over 400 million active users, is a prime target for cybercriminals. This article isn't a guide to hacking; it's a forensic look at the real methods attackers use to compromise Outlook accounts. By understanding these techniques, you can build an impenetrable defense. We will delve into the dark underbelly of cyber threats, expose the tools used (for educational awareness only), and equip you with the knowledge to shield your digital life.
By Alexander Hoffmann6 days ago in 01
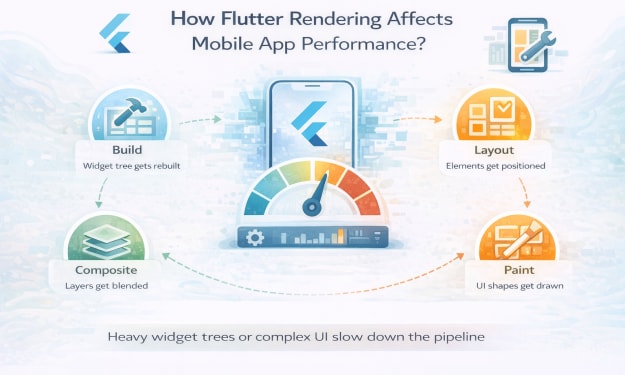
How Flutter Rendering Affects Mobile App Performance?
I still remember the first Flutter app I shipped to production. The UI felt smooth. Almost suspiciously smooth. Animations flowed like they were rehearsed. Then a user emailed support saying the app felt “heavy” after ten minutes of use. Not broken. Just tired.
By Mary L. Rodriquez6 days ago in 01
Upgrading Batch Asphalt Plants for Polar Conditions
Manufacturers are increasingly focused on enhancing the capabilities of batch asphalt plants to meet the unique challenges posed by polar region road construction. Upgrades to the anti-freeze batching system and thermal insulation components are pivotal in ensuring that these plants operate effectively in extremely cold conditions. This article explores how these technical optimizations impact the performance of asphalt batch mix plants and their overall pricing.
By Macroad Asphalt Plant7 days ago in 01
How to Create QR Code: A Complete Guide with QR Code Generator Pricing . AI-Generated.
QR codes have become a powerful bridge between offline and online experiences. From restaurant menus and business cards to marketing campaigns and product packaging, QR codes offer a fast, contactless way to share digital content. As more brands adopt this technology, understanding how to create QR code solutions effectively—and choosing the right platform—has never been more important.
By Kashif Khan7 days ago in 01
The Anti-Brand Teaching Business
A lot of people don't want to be a "personal brand." They don't want to post their face every day. They don't want to turn their life into content. They don't want to explain themselves to the internet. They just want to teach, get paid, and keep their privacy.
By Destiny S. Harris8 days ago in 01