gadgets
The future is here; discover the latest gadgets and electronics on the market making life a whole lot simpler and cooler.
US Telecom Networks Hacked: Chinese Cyber Spies Use Sophisticated Malware
The Chinese state-sponsored hacking group known as Salt Typhoon has been identified as using a custom utility called JumbledPath to stealthily monitor network traffic and potentially capture sensitive data. These cyberattacks have targeted major U.S. telecommunication providers, raising significant concerns about national security and data privacy.
By WIRE TOR - Ethical Hacking Services12 months ago in 01
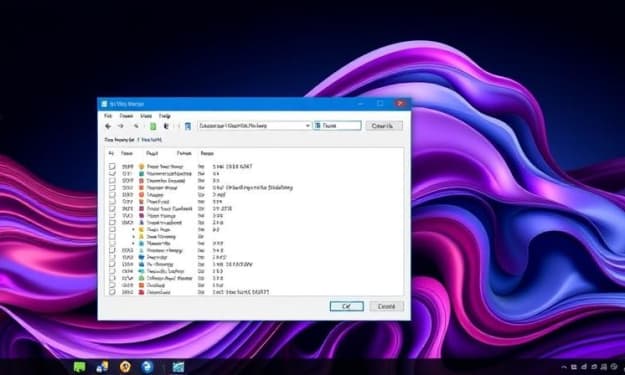
WinRAR's New Update Boosts Privacy by Removing Windows Metadata
Introduction WinRAR, one of the most widely used file archivers and compression tools for Windows, has just received a significant update with the release of version 7.10. This new update introduces several features aimed at improving performance, usability, and security. Among these, one of the most notable changes is the ability to strip sensitive metadata from the Mark-of-the-Web (MoTW) alternate data stream, increasing privacy for users who frequently download and share files.
By WIRE TOR - Ethical Hacking Services12 months ago in 01
Black Basta Ransomware Gang Exposed: Internal Chat Logs Leak Online
Leaked Chat Logs Expose Internal Conflict and Operations An unknown leaker has released what they claim to be an archive of internal Matrix chat logs belonging to the Black Basta ransomware operation. The leaked information sheds light on the gang’s internal operations, conflicts, and possible motivations behind their cybercriminal activities.
By WIRE TOR - Ethical Hacking Services12 months ago in 01
The Future of POS Systems: Trends & Innovations in 2025. AI-Generated.
POS systems have come a long way from simple cash registers to sophisticated digital solutions that integrate payments, inventory management, and customer analytics. As we move into 2025, several key trends and innovations are set to redefine how businesses interact with customers and manage operations. Let’s explore the future of POS systems and how AI, cloud-based POS, and contactless payments are shaping the industry.
By Nabeel WRKPR12 months ago in 01
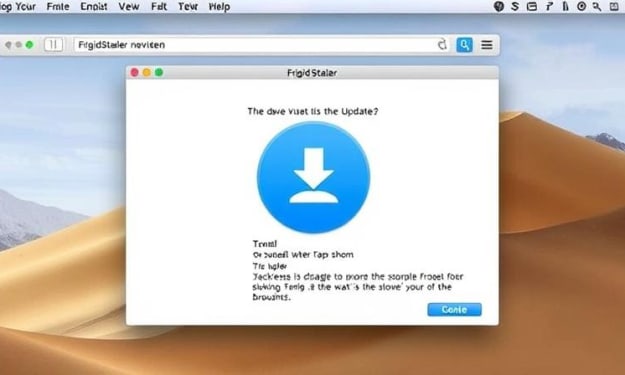
Beware of Fake Updates: FrigidStealer Malware Targets Mac Devices
The FakeUpdate malware campaigns are becoming increasingly complex, with two additional cybercrime groups, TA2726 and TA2727, now involved in delivering a new macOS infostealer malware called FrigidStealer. These threat actors are running campaigns that distribute malware via fake browser update notifications, affecting not only Mac users but also Windows and Android users.
By WIRE TOR - Ethical Hacking Services12 months ago in 01
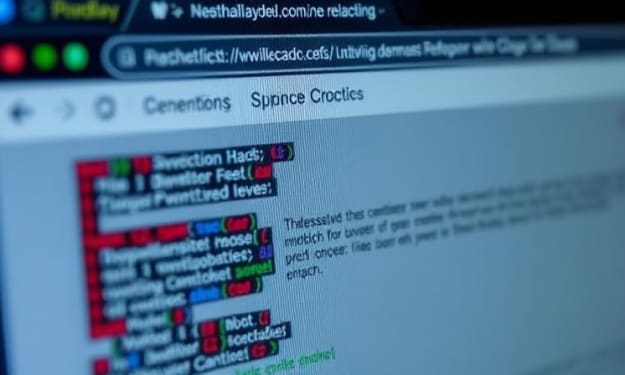
Cybercriminals Use Invisible Unicode to Mask JavaScript in Phishing Attacks
A new JavaScript obfuscation technique leveraging invisible Unicode characters to represent binary values is actively being used in phishing attacks. This novel method, first disclosed in October 2024, has been quickly adopted by threat actors targeting affiliates of an American political action committee (PAC).
By WIRE TOR - Ethical Hacking Services12 months ago in 01
Australian Fertility Services Giant Genea Hit by Security Breach
One of Australia’s largest fertility service providers, Genea, has confirmed a security breach after detecting suspicious activity on its network. The company revealed that unknown attackers had gained unauthorized access to its systems, prompting an urgent investigation to determine the extent of the breach and its potential impact on patients.
By WIRE TOR - Ethical Hacking Services12 months ago in 01
MiTM and DoS Attacks Enabled by Critical Flaws in OpenSSH
Introduction OpenSSH has recently released security updates to address two critical vulnerabilities that expose SSH servers to machine-in-the-middle (MiTM) and denial-of-service (DoS) attacks. One of these vulnerabilities has remained undiscovered for over a decade. The security research team at Qualys identified and reported these issues to OpenSSH maintainers, demonstrating their potential exploitability.
By WIRE TOR - Ethical Hacking Services12 months ago in 01