cybersecurity
Our personal, digital, national and military security depend on a safe cyber space.
Discerning the Difference: A Guide to Trustworthy Crypto Recovery Services
The permanent loss of cryptocurrency due to hacks or scams creates a desperate need for solutions. This has given rise to a complex industry of digital asset recovery services. Within this space, the line between a legitimate professional service and a predatory scam can be dangerously thin. This guide aims to provide clear, actionable information to help individuals identify trustworthy help and understand the critical importance of reporting fraudulent activity.
By Tyler Hamiltonabout a month ago in 01
A Comparative Examination of Crypto Recovery Domains: Authenticity vs. Deception
The irreversible nature of cryptocurrency transactions means that a single mistake or successful hack can lead to devastating, permanent loss. In this high-stakes environment, a market for asset recovery services has emerged, promising hope to victims. However, this very niche is also a fertile ground for deception, where distinguishing between a legitimate service and a sophisticated scam is critically important. By examining common traits and red flags, individuals can learn to navigate this complex landscape with greater caution and clarity.
By Tyler Hamiltonabout a month ago in 01
Amazon Issues Attack Warning. AI-Generated.
Amazon has issued an urgent warning to customers after identifying a surge in coordinated attacks targeting user accounts, payment details, and personal information. These threats have grown more advanced, making it harder for shoppers to recognize fraudulent messages mixed with legitimate Amazon alerts. With a record number of online purchases happening year-round, attackers are using the high volume of communication to hide their scams effectively.
By Md. Nurul Afsar2 months ago in 01
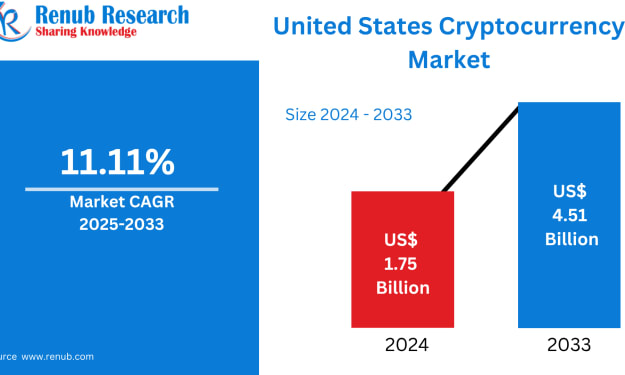
United States Cryptocurrency Market Size and Forecast (2025–2033). AI-Generated.
A Transforming Financial Era The United States Cryptocurrency Market is entering a defining phase. According to Renub Research, the market is projected to increase from US$ 1.75 billion in 2024 to US$ 4.51 billion by 2033, registering a CAGR of 11.11% from 2025 to 2033. This steady rise signals a major shift—cryptocurrencies are no longer viewed merely as speculative assets but as a legitimate, growing pillar of the American financial ecosystem.
By Janine Root 2 months ago in 01
Elite Shungite: The Rare Healing Stone With Powerful Natural Benefits
Elite shungite has become one of the most talked-about natural minerals in the wellness world. From water purification to energy protection and spiritual grounding, this rare stone is believed to offer powerful benefits that go beyond ordinary crystals. Because of its unique carbon structure and limited availability, elite shungite is often seen as the purest and most effective form of shungite available today.
By Shahid Abbas 2 months ago in 01
How to Protect SaaS Applications from API Misconfiguration Breaches
Introduction APIs are the backbone of modern SaaS applications, enabling seamless integration, data exchange, and automation across platforms. They allow users to interact with applications, sync information with third-party tools, and perform complex workflows in real time. However, this convenience comes with hidden risks: even small misconfigurations can create vulnerabilities that expose sensitive data or allow unauthorized access.
By Sam Bishop2 months ago in 01
How to Hack Yahoo Password: 100% Working Methods for Cybersecurity Defense. AI-Generated.
Email accounts from major providers like Yahoo are often viewed as secure vaults for our personal and professional lives. However, the sophisticated realm of cybersecurity paints a different picture: no system is entirely impervious. This article delves into the advanced methods that a dedicated hacker might employ to compromise a Yahoo account and obtain a user's password. Our goal is not to facilitate illegal activity but to arm cybersecurity professionals and security-conscious users with critical knowledge. By understanding these offensive hack techniques, you can build formidable digital defenses, learn to recognize threats, and ultimately protect your assets more effectively.
By Alexander Hoffmann2 months ago in 01
WiFi Hacking: The Ultimate Guide to Threats and Your 10-Step Protection Plan. AI-Generated.
WiFi is the oxygen of our digital lives, powering everything from smart homes to online banking. Yet, this convenience creates an invisible battlefield where your personal data is the prize. Understanding WiFi hacking isn't about paranoia; it's about digital self-defense.
By Alexander Hoffmann2 months ago in 01
How to Stay Safe Online: A Complete Cybersecurity Guide. AI-Generated.
In today’s digital world, staying safe online is no longer optional. From financial fraud to identity theft and cyberbullying, threats are everywhere. Whether you use the internet for work, school, or daily communication, understanding how to protect yourself is essential. This complete cybersecurity guide breaks down the key steps every user should take to stay secure.
By Muhammad Irfan Afzal2 months ago in 01
Why Every Modern Business Needs a Strong Cybersecurity Partner
Today’s business world is more digital than ever. Companies use cloud services, online tools, mobile apps, and remote work systems to run their daily operations. While all this technology makes work faster and easier, it also creates new dangers. Cyberattacks have become a normal part of the digital environment, and they are happening every single day. Because of this, having a trusted cybersecurity partner is not just helpful—it is essential for any business that wants to stay safe and grow confidently.
By Preethu Sonu2 months ago in 01