How to Hack Yahoo Password: 100% Working Methods for Cybersecurity Defense
The Real Methods Hackers Use & How to Stop Them

Email accounts from major providers like Yahoo are often viewed as secure vaults for our personal and professional lives. However, the sophisticated realm of cybersecurity paints a different picture: no system is entirely impervious. This article delves into the advanced methods that a dedicated hacker might employ to compromise a Yahoo account and obtain a user's password. Our goal is not to facilitate illegal activity but to arm cybersecurity professionals and security-conscious users with critical knowledge. By understanding these offensive hack techniques, you can build formidable digital defenses, learn to recognize threats, and ultimately protect your assets more effectively.
🛑 Critical Educational Disclaimer
This guide is for educational purposes ONLY. Attempting to hack or access someone's Yahoo account without their explicit permission is illegal, unethical, and can result in severe legal consequences, including criminal charges. The information provided is designed to help cybersecurity professionals, ethical hackers, and security researchers understand vulnerabilities and strengthen security postures. It is not intended to facilitate illicit activities. Always practice responsible disclosure and ethical hacking.
PASS ACCESS
PASS ACCESS is an AI-powered application engineered to hack passwords for Yahoo Mail accounts using advanced algorithms for interception and cryptographic analysis. The tool can recover passwords without triggering security alerts from Yahoo. It is promoted as a solution for accessing old or lost accounts. The application's use is restricted to accounts the user is authorized to access.
You can download PASS ACCESS from its official website: https://www.passwordrevelator.net/en/passaccess

Advanced Hacking Methods: A Cybersecurity Deep Dive
To effectively protect a system, one must understand how it can be attacked. Here are some of the most sophisticated Yahoo hacking methods used in the wild that go far beyond simple password guessing.
1. Advanced Phishing & Spear Phishing Campaigns

Modern phishing is no longer about poorly written emails from a "prince." Spear phishing involves highly targeted campaigns where attackers craft personalized messages, often using information gleaned from social media or data breaches. They use look-alike domains that are nearly identical to the real Yahoo login page. Advanced tools like Evilginx2 can create real-time proxies that intercept login credentials and even bypass multi-factor authentication (MFA) by stealing session cookies, making the attack incredibly effective.
2. Session Hijacking & Cookie Theft
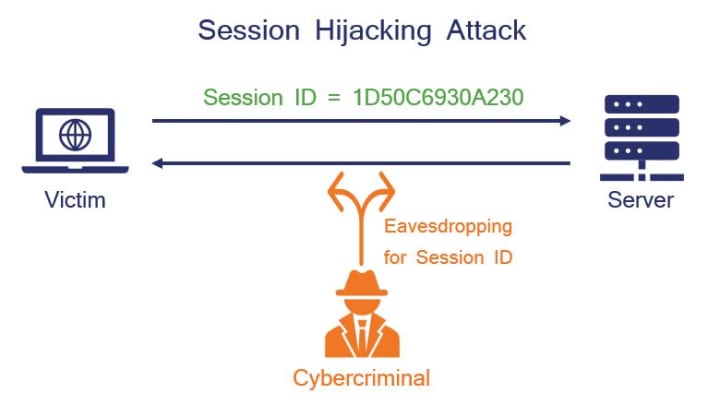
Why steal a password when you can steal the active session? Session hijacking involves stealing a user's browser cookies after they have logged in. An attacker can achieve this by exploiting a Cross-Site Scripting (XSS) vulnerability on a legitimate website the user visits. Alternatively, on unsecured public Wi-Fi, a Man-in-the-Middle (MITM) attack can intercept these cookies. Once obtained, the hacker can inject them into their own browser to gain full access to the Yahoo account without needing the password at all.
3. SIM Swapping Attacks
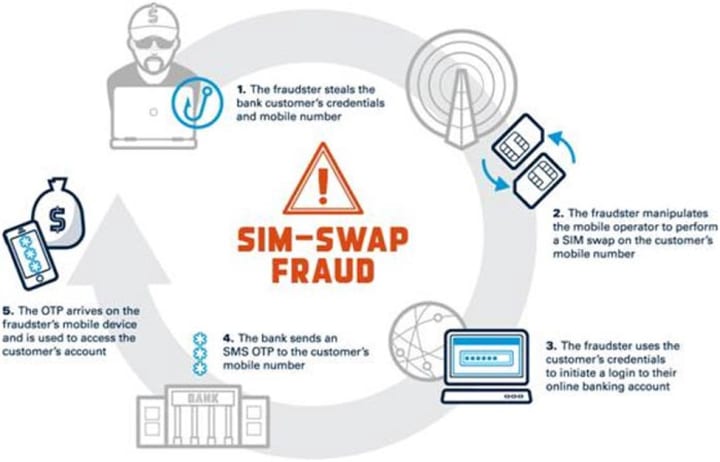
This method directly targets the weak link in SMS-based two-factor authentication. In a SIM swapping attack, the threat actor uses social engineering to convince a mobile carrier employee to transfer the victim's phone number to a SIM card they control. Once successful, all SMS messages, including Yahoo's password reset codes and MFA verification texts, are sent to the attacker's device. This allows them to easily recover and take over the account.
4. Zero-Day Exploits
A theoretical but ever-present threat, a zero-day exploit refers to a vulnerability in Yahoo's software or infrastructure that is unknown to the company. A highly skilled hacker who discovers such a flaw could potentially exploit it to gain unauthorized access to user accounts. While these exploits are rare, extremely valuable, and often used in targeted attacks, their existence underscores the need for continuous security monitoring and patching.
5. Supply Chain Attacks (Indirect Compromise)
Sometimes, the easiest way into an account is through a connected third party. Many users grant OAuth permissions to third-party apps. If one of these apps is compromised in a supply chain attack, the attacker could gain the access rights that app has to the user's Yahoo mailbox. This indirect method bypasses the need to attack Yahoo's core infrastructure directly.

Advanced Protection Methods: Fortifying Your Yahoo Account
Knowledge of these attack vectors empowers you to build a robust defense. Here’s how to protect your account.
Protection 1: Hardware-Based Multi-Factor Authentication (MFA)
Ditch SMS-based codes. A physical security key that uses the FIDO2/U2F standard (like a YubiKey) provides the strongest defense against phishing and SIM swapping. It verifies the website's authenticity, making stolen credentials useless to an attacker.
Protection 2: Advanced Password Management
Use a reputable password manager to generate and store long, unique, and complex passwords for every service you use. Opt for a manager with a zero-knowledge architecture, ensuring even the service provider cannot access your data.
Protection 3: Proactive Session Monitoring & Security Audits
Regularly check your Yahoo account security settings. Review "Recent activity" for unfamiliar logins and "Connected apps" to revoke access for services you no longer use. This is a crucial cybersecurity hygiene habit.
Protection 4: Operating System & Browser Hardening
Keep your OS and browsers updated to patch known vulnerabilities. Use security-focused browser extensions to block malicious ads and scripts, reducing the risk of drive-by downloads and malware that can lead to credential theft.
Account Recovery Methods: Regaining Control
If you suspect a breach, act swiftly. Here is how to recover your account.
- Immediate Action: Immediately use Yahoo's "Log out of all devices" feature and change your password. Scrutinize your account's recent activity log for any suspicious actions.
- Utilize Official Recovery: Follow Yahoo's official account recovery process. This is why keeping your recovery email and phone number up-to-date is critical for security.
- Report to Authorities: If sensitive personal or financial information was exposed, report the incident to the relevant law enforcement agencies and consider placing a fraud alert on your credit reports.
- Forensic Analysis: For organizations, a deeper forensic analysis is essential to determine the attack vector, contain the breach, and prevent future incidents.
Conclusion
The landscape of digital security is a constant arms race. Understanding how to hack a Yahoo password from a defensive cybersecurity perspective is not about enabling crime, but about preventing it. The sophisticated methods employed by modern hackers, from advanced phishing to SIM swapping, highlight the critical need for equally advanced defensive measures. By implementing hardware MFA, practicing rigorous password hygiene, and maintaining constant vigilance, you can transform your knowledge of threats into an impenetrable shield for your Yahoo account.
FAQ - Frequently Asked Questions
Q: Is it truly possible to 'hack' a 'Yahoo account' in today's 'cybersecurity' landscape?
A: While Yahoo employs robust security measures, advanced hacker methods like targeted social engineering, zero-day exploits, or SIM swapping can potentially bypass defenses, making continuous vigilance and education crucial.
Q: What is the most common 'method' 'hacker's' use to compromise a 'Yahoo password'?
A: Today, sophisticated phishing campaigns (especially those designed to bypass MFA) and SIM swapping are among the most effective, as they often target human vulnerabilities or telecom infrastructure rather than the platform's code itself.
Q: 'How to protect' my 'Yahoo account' from these advanced 'hacking' 'methods'?
A: Implement hardware-based MFA, use a dedicated password manager, regularly monitor your account activity and connected apps, and continuously learn about current cybersecurity threats.
Q: Can a 'Yahoo' 'password' be 'hacked' without user interaction?
A: Yes, through techniques like session hijacking (via XSS), malware designed for credential theft, or the exploitation of a zero-day vulnerability. These methods require less direct user interaction than phishing.
Q: What should I do immediately if I suspect my 'Yahoo account' has been 'hacked'?
A: Immediately change your password, log out of all devices, review recent activity for anything suspicious, and contact Yahoo support to initiate the official account recovery process.
Q: Are there legitimate tools 'how to learn' about 'hacking' and 'cybersecurity' for 'Yahoo' 'account' 'security'?
A: Absolutely. Ethical hacking courses (e.g., Offensive Security Certified Professional), penetration testing labs, and security research forums provide invaluable, legitimate insights into vulnerabilities and defense strategies.
Q: 'How to recover' my 'Yahoo account' if the 'hacker' changed my recovery options?
A: Your best recourse is to contact Yahoo's official support immediately. They have specific procedures for identity verification to help legitimate owners regain control, though this process can be complex and time-consuming.
Keywords: Yahoo account security, hacking methods, cybersecurity, password protection, advanced phishing, spear phishing, session hijacking, cookie theft, SIM swapping, zero-day exploits, supply chain attacks, multi-factor authentication (MFA), password manager, account recovery, ethical hacking, cyber defense, digital security.
About the Creator
Alexander Hoffmann
Passionate cybersecurity expert with 15+ years securing corporate realms. Ethical hacker, password guardian. Committed to fortifying users' digital safety.






Comments
There are no comments for this story
Be the first to respond and start the conversation.