What Is Cyber Security? A Complete Beginner’s Guide (By: Streak Ranker)
What Is Cyber Security? A Complete Beginner’s Guide

Defining Cybersecurity: Your Digital Guardian
Cybersecurity is the comprehensive practice and technology dedicated to safeguarding digital systems, networks, devices, and data from malicious digital attacks, unauthorized access, damage, or theft. In an increasingly interconnected world, where digital interactions are integral to daily life, business, and governance, cybersecurity plays a critical role in preserving sensitive information and ensuring the continuous operation of digital assets. It involves a dynamic combination of technologies, strategic processes, and human vigilance to counter sophisticated and constantly evolving cyber threats.
The core objective of cybersecurity is to maintain the security posture of digital environments. This encompasses protecting personal information, intellectual property, financial data, and critical infrastructure from a wide array of cybercriminal activities, including hacking, phishing, ransomware, and identity theft. By implementing robust security measures, organizations and individuals can mitigate risks, minimize potential damages from breaches, and ensure the resilience of their digital ecosystems.
Key Insights into Cybersecurity for Beginners
Foundational Principles: Cybersecurity is built upon the CIA triad—Confidentiality, Integrity, and Availability—ensuring data is protected, accurate, and accessible to authorized users.
Multifaceted Defense: Effective cybersecurity involves a layered approach using various technologies (firewalls, antivirus, encryption), processes (incident response, risk management), and human awareness to protect against diverse threats.
Empowering Individuals: Basic cybersecurity practices like strong passwords, multi-factor authentication, regular software updates, and cautious online behavior are crucial for personal digital safety and can significantly mitigate risks.
The Cornerstone of Cybersecurity: The CIA Triad
At the heart of cybersecurity lies the fundamental framework known as the CIA triad. This acronym represents three core security principles that guide the development and implementation of all cybersecurity measures:

Ensuring global data security is paramount in today's digital landscape.
Confidentiality: Protecting Secrets
Confidentiality ensures that sensitive information is accessible only to authorized individuals. It prevents unauthorized disclosure of data, whether it's personal identifiable information (PII), proprietary business data, or national security secrets. Techniques such as encryption, access controls, and strict authentication protocols are employed to uphold confidentiality. For example, encrypting a hard drive ensures that even if a device is stolen, the data remains unreadable to an unauthorized party.
Integrity: Preserving Accuracy and Trustworthiness
Integrity guarantees that data remains accurate, consistent, and unaltered throughout its lifecycle. It protects information from unauthorized modification or destruction, ensuring its reliability and trustworthiness. Measures like data backups, checksums, digital signatures, and version control are used to maintain data integrity. If data integrity is compromised, it could lead to incorrect decisions, financial losses, or a complete loss of trust in the information system.
Availability: Ensuring Access When Needed
Availability ensures that systems, applications, and data are accessible to authorized users when and where they are needed. This principle focuses on preventing service disruptions, whether due to hardware failures, network outages, or denial-of-service (DoS) attacks. Strategies include redundant systems, disaster recovery plans, robust network infrastructure, and regular maintenance to maximize uptime and accessibility. Without availability, even confidential and integral data becomes useless if it cannot be accessed.
Common Cyber Threats: Navigating the Digital Minefield
Cyber threats are constantly evolving, becoming more sophisticated and diverse. Understanding these common attack vectors is crucial for developing effective defenses:
Phishing: A prevalent social engineering technique where attackers impersonate trustworthy entities (e.g., banks, government agencies) to trick individuals into revealing sensitive information like usernames, passwords, and credit card details. This can occur via email, text messages (smishing), or phone calls (vishing).
Ransomware: A type of malicious software that encrypts a victim's files, making them inaccessible. The attacker then demands a ransom (usually in cryptocurrency) for the decryption key. Notorious examples include WannaCry, which affected organizations globally.
Malware: A broad term for malicious software, including viruses, worms, Trojans, spyware, and adware. Malware aims to damage, disrupt, or gain unauthorized access to computer systems.
Man-in-the-Middle (MITM) Attacks: Where an attacker secretly intercepts and relays communications between two parties who believe they are communicating directly. This allows the attacker to eavesdrop or alter the conversation.
IoT Vulnerabilities: Exploiting security weaknesses in internet-connected devices, from smart home appliances to industrial sensors. These devices often lack robust security features, making them easy targets for attackers to gain entry into networks.
Unauthorized Access: Gaining entry to systems or networks without proper authorization, often through stolen credentials, exploited vulnerabilities, or weak access controls.
Denial of Service (DoS) / Distributed Denial of Service (DDoS) Attacks: Overwhelming a system, server, or network with a flood of internet traffic to disrupt normal operations, making resources unavailable to legitimate users.
A Layered Defense: Key Components of Cybersecurity
Effective cybersecurity employs a multi-layered defense strategy, often referred to as "defense in depth," to protect digital assets from various attack vectors. Each layer adds an additional barrier, ensuring that even if one layer is breached, others remain to protect the system.
Prevention and Protection: Building the Fortifications
This foundational layer focuses on proactive measures to stop unauthorized access before it happens. Key tools and practices include:
Firewalls: Act as a barrier between a trusted internal network and untrusted external networks, controlling incoming and outgoing network traffic.
Antivirus Software: Detects, prevents, and removes malicious software.
Encryption: Transforms data into a coded format to prevent unauthorized access, ensuring confidentiality.
Access Controls: Mechanisms that determine who can access what resources and under what conditions, including strong passwords and user authentication.
Detection and Monitoring: Constant Vigilance
Even with strong preventive measures, threats can bypass defenses. This layer involves continuous surveillance to identify suspicious activities or breaches as they occur:
Intrusion Detection Systems (IDS): Monitor network traffic for suspicious activity and alert security personnel.
Security Information and Event Management (SIEM): Collects and analyzes security event data from various sources to provide a centralized view of security posture.
Behavioral Analytics: Identifies anomalous patterns in user or system behavior that might indicate a threat.
Response and Mitigation: Damage Control and Recovery
Once a threat is detected, a rapid and coordinated response is critical to minimize damage and restore normal operations:
Incident Response Plan: A predefined set of procedures to follow when a security incident occurs, outlining roles, responsibilities, and steps for containment, eradication, and recovery.
Patch Management: Regularly applying software updates and security patches to address known vulnerabilities.
Data Backups: Creating copies of data that can be restored in case of data loss or corruption due to an attack.
Risk Management: Strategic Protection
This involves assessing the value of digital assets, identifying potential risks, and implementing strategies to mitigate them. It’s a foundational step that informs all other cybersecurity efforts, ensuring resources are allocated effectively to protect the most critical assets.
Education and Awareness: The Human Element
Since many cyberattacks exploit human error (e.g., clicking on phishing links), educating users and employees on security best practices is paramount. Regular training can significantly reduce an organization's vulnerability to social engineering attacks.
Legal and Regulatory Compliance: Adhering to Standards
Organizations must adhere to various laws and regulations (e.g., GDPR, HIPAA, CCPA) related to data privacy and security. Compliance ensures that digital assets are protected according to established legal frameworks, preventing hefty fines and reputational damage.

Navigating GDPR and other regulations is crucial for global digital operations.
Why Cybersecurity Matters in Today's Digital World
In an era where data is often considered the new oil, its protection is not merely a technical concern but a fundamental necessity for individuals, businesses, and governments alike. The increasing reliance on technology for virtually every aspect of modern life has amplified the stakes, making cybersecurity an indispensable discipline.
For individuals, inadequate cybersecurity can lead to devastating consequences such as identity theft, financial fraud, and privacy breaches. Personal data, including financial details, health records, and social security numbers, can be compromised, leading to significant personal and economic hardship. The widespread use of online banking, e-commerce, and social media platforms means that individual digital footprints are larger than ever, presenting more opportunities for malicious actors to exploit.
For businesses, the impact of cyberattacks extends beyond immediate financial losses. Data breaches can severely damage a company's reputation, eroding customer trust and leading to long-term revenue decline. Operational disruptions caused by ransomware or DoS attacks can halt business processes, resulting in lost productivity and significant recovery costs. Furthermore, intellectual property theft can undermine a company's competitive advantage and innovation pipeline. Compliance failures with data protection regulations, such as GDPR or HIPAA, can also lead to substantial legal penalties and regulatory scrutiny.
Governments and critical infrastructure sectors face even higher stakes. Cyberattacks on national infrastructure—such as power grids, water treatment plants, or transportation systems—can have catastrophic societal consequences, jeopardizing public safety and national security. Espionage and sabotage carried out through cyber means pose a constant threat to national sovereignty and international relations.
The global shortage of trained cybersecurity professionals further underscores the criticality of this field. As cyber threats become more sophisticated and prevalent, the demand for skilled individuals capable of designing, implementing, and managing robust security defenses continues to outpace supply. This growing skills gap highlights the urgent need for investment in cybersecurity education and professional development.
A Beginner's Roadmap to Cybersecurity Mastery
Embarking on a journey into cybersecurity can seem daunting, but a structured approach can simplify the learning process. Whether for personal protection or career advancement, building a solid foundation is key.
Foundational Knowledge: Starting Strong
Begin by grasping the core concepts of computer systems, networking, and security principles. Understanding how computers communicate, the basics of operating systems, and fundamental security terminology will provide a robust framework. Resources like online courses from platforms such as Codecademy and Coursera offer excellent beginner-friendly introductions.
Practical Skills: Learning by Doing
Theoretical knowledge is enhanced significantly by hands-on practice. Engage in activities that build practical skills:
Network Analysis: Learn to capture and analyze network traffic to understand how data flows and where vulnerabilities might exist.
Password Testing: Experiment with tools to test password strength and understand common cracking techniques.
Home Lab Setup: Create a virtual or physical home lab environment to safely experiment with different operating systems, security tools, and attack simulations.
Implementing Basic Protections: Everyday Cybersecurity
For immediate personal protection, integrate fundamental cybersecurity practices into your daily digital habits:
Regular Software Updates: Always keep your operating system, web browsers, and applications updated to patch known security vulnerabilities.
Strong, Unique Passwords: Use complex, unpredictable passwords for all accounts and consider a password manager to securely store them.
Multi-Factor Authentication (MFA): Enable MFA whenever possible, adding an extra layer of security beyond just a password.
Data Encryption: Encrypt sensitive files and devices to protect data from unauthorized access if they are lost or stolen.
Regular Backups: Periodically back up important data to an external drive or cloud service to ensure recovery in case of data loss due to attacks or failures.
Cautious Online Behavior: Be skeptical of suspicious emails, links, or unsolicited requests for personal information. Avoid using public Wi-Fi for sensitive transactions.

Securing your Wi-Fi router is a fundamental step in home network protection.
Certification and Continued Learning: Professional Growth
For those considering a career in cybersecurity, certifications are invaluable. The CompTIA Security+ is widely recognized as an excellent entry-level certification that covers essential security concepts, threats, and best practices. Continuous learning is vital in this rapidly evolving field; stay informed about emerging threats and new defense strategies through industry news, blogs, and advanced courses.
Understanding Cybersecurity Through Data Visualization
To better understand the various facets of cybersecurity and the perceived effectiveness of different security measures, the following charts provide a visual representation. These charts are based on opinionated analyses of general best practices and typical threat landscapes, offering a conceptual overview rather than precise statistical data.
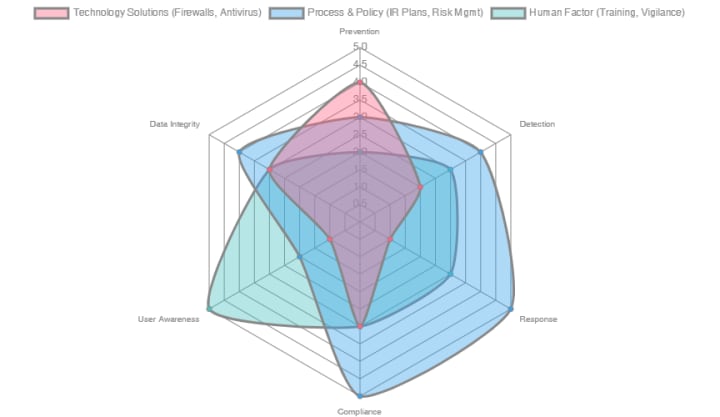
Effectiveness of Cybersecurity Measures (Radar Chart)
This radar chart illustrates the relative effectiveness of different cybersecurity measures across key security dimensions. Each point on the axis represents a crucial aspect of security, rated from 0 (least effective) to 5 (most effective) in a generalized context. This helps visualize where different measures typically excel and where they might require support from other layers.
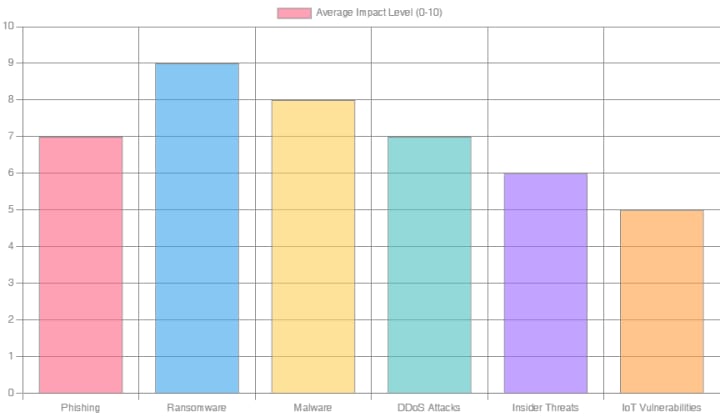
Impact of Common Cyber Threats (Bar Chart)
This bar chart assesses the general impact level of various common cyber threats on a scale from 0 to 10. The impact considers factors such as financial loss, data compromise, operational disruption, and reputational damage. This helps beginners understand which threats tend to have the most significant consequences.
Conclusion: Securing Our Digital Future
Cybersecurity is not merely a technical discipline but a vital societal imperative in our increasingly digital world. From safeguarding individual privacy to protecting national critical infrastructure, its importance cannot be overstated. For beginners, understanding the foundational principles of confidentiality, integrity, and availability, coupled with a knowledge of common threats, forms the bedrock of effective defense. Implementing practical measures like strong passwords, multi-factor authentication, and regular software updates empowers individuals to take charge of their digital safety. As cyber threats continue to evolve, continuous learning and vigilance remain essential. The field offers immense opportunities for those willing to learn, contributing to a more secure and resilient digital future for everyone.
About the Creator
Streak Ranker
Grow Faster with the Top-Rated Digital Marketing Agency (Streak Ranker) – Trusted for Real Results and Expert Support.






Comments
There are no comments for this story
Be the first to respond and start the conversation.