Choosing the Right Token Model: Utility, Security, or Governance?
A Comprehensive Guide to Utility, Security, and Governance Tokens in Modern Blockchain Ecosystems

New blockchain protocols also allow for multiple tokens to be used to support transactions or coordinate governance such as by rewarding certain behavior. The token model selected for a project can have large implications for the legal analysis, economic viability, adoption, and governance of the token.
The token model includes the function of the token, the rights granted to its holders and its behavior during value exchange. Tokenization finds application in decentralized finance, asset management and the shared economy. Challenges include regulatory, as well as a lack of clarity on tokenomics. In the United States, SEC rules and in the European Union, MiCA regulation differentiate utility, security and governance tokens in their respective policies, practices and intentions.
Incentives can also result in regulatory oversight, trust erosion, and challenges to the system's usability. However, well-designed token incentive mechanisms can ease engagement, coordination, governance, and many other activities. As the blockchain ecosystem matures and grows into DeFi, supply chains, gaming and social media projects, aligning a token strategy and use case with duration is becoming increasingly important.
Utility Tokens: Functionality and Ecosystem Integration
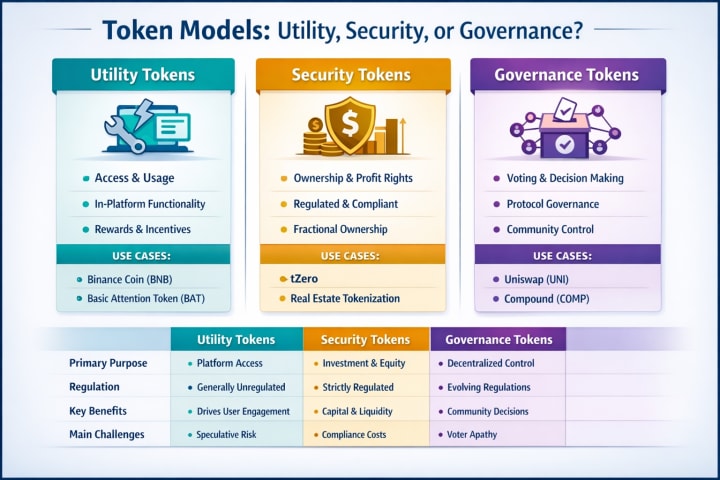
Utility tokens, or user tokens, are the 'workhorse' of any blockchain. A utility token is essentially a token which gives the user a certain product or service, but no ownership or profit rights. In short, the utility token defines how an user can interact and use a digital ecosystem, making utility tokens the preferred choice for projects focused on user interaction, platform growth or utilization of dApps.
Core Characteristics of Utility Tokens
Utility tokens can be distinguished from security or governance tokens by the following characteristics:
- Functional Use: Utility tokens are often used to gain access to certain features of a protocol or product. For example, Binance Coin (BNB) is used to pay trading fees on the Binance exchange, and Filecoin (FIL) is used to pay for decentralized data storage.
- Non-Investment Orientation: Non-Investment Orientation: Utility tokens confer no ownership interest or right to a return on the investment to the holder but rather a right to receive a good or service. Utility tokens are not security tokens; if misclassified as the latter, the project is subject to securities regulation.
- Incentive Alignment: Utility tokens can incentivize behavior within the ecosystem, such as providing computing power, engaging with content, or validating a transaction.
Strategic Benefits and Challenges
As well as the development of network effects from the use of utility tokens on a platform:
- User Engagement: Utility tokens can be used to access a platform's services or features, often resulting in a positive feedback loop in which an user's engagement drives demand for the token.
- Scalability of Incentives:Projects can release a reward to any early adopters, less experienced content creators, or validators for actions that help scale the ecosystem.
- Regulatory Considerations: A properly structured utility token might not be considered a security, which means that it would not be subject to securities regulations and would be available to a larger audience.
Utility tokens are subject to many issues faced by cryptocurrency tokens, including market volatility, overissuance, and misalignment of incentives. This means that a utility token may be treated as a security token if it has been issued for speculation rather than use on the platform. Another aspect of an economic model that may fail is imbalanced tokenomic design, where early adopters of a blockchain ecosystem are not rewarded fairly with tokens.
Real-World Example
The most famous example of a utility token that has been successfully deployed is the Basic Attention Token (BAT) built into the Brave web browser software. BAT gives utility to the Brave web browser by rewarding users for viewing ads that respect users' privacy, and paying content publishers using BAT. BAT is an example of a measurable utility-driven demand as it is used for platform utility, which an effective utility token would be looking to create.
Security Tokens: Investment, Compliance, and Institutional Integration
Security tokens are described as tokens representing any equity, right to revenue or profit sharing a holder may have in a project, and contrasted with utility tokens that provide access to a product or service that an organization provides. Security tokens are blockchain equivalents of stocks, bonds or investment funds, and are subject to the same regulatory framework, investor expectations and token economy characteristics.
Defining Features of Security Tokens
Security tokens share some characteristics with customary security types like common stocks:
- Ownership and Equity Rights: Depending on the asset class, security tokens can give the rights to receive dividends, to vote, or to receive revenue generated by the asset. In real estate tokenization, security tokens represent fractional ownership of an underlying asset.
- Expectation of Profit: The main difference between security tokens and utility tokens is whether the holder of the asset expects a profit to be made by the efforts of others. This distinction creates the need for security tokens to fall under the jurisdiction of securities regulators such as the US Securities and Exchange Commission (SEC).
- Regulatory Oversight: Security tokens are typically subject to similar regulations as regular securities when it comes to issuing them, trading them, and disclosing information, including Know your customer (KYC), anti-money laundering (AML) requirements, and reporting requirements particularly relevant to securities.
Strategic Advantages
Security tokens offer unique opportunities for blockchain projects and institutional actors.
- Access to Capital Markets: Tokenizing equity or debt instruments allows to access a global pool of investors which results in a lower cost of capital and greater liquidity.
- Fractional Ownership: Tokenization allows users to own, or gain a right to benefit from, fine-grained shares of real estate, fine art, collectibles, shares of privately held or publicly traded companies, or similar assets too expensive to own outright.
- Enhanced Transparency and Efficiency: Automated settlement, transaction history transparency, and less reliance on intermediaries make it possible to replace clearinghouses, custodians and other such infrastructure with software.
Challenges and Considerations
While security tokens have advantages, they are not without challenges.
- Regulatory Burden: The time spent and cost of producing the required documents can make an STO prohibitively complex for small projects. Failure to comply with all of the regulations means the sale will not take place and fines or other penalties may be applied.
- Liquidity Constraints: Liquidity at the exchanges for security tokens is considered to be low, as there are fewer exchanges to trade security tokens than conventional cryptocurrencies.
- Market Perception:Investors that seek speculative investments in cryptocurrency may not be interested in security tokens, as the tokens are subject to regulatory requirements and less volatile.
Case Study
A contrasting approach has been adopted by Overstock subsidiary tZero, which has mainly focused on tokenized offerings from the perspective of a regulated trading platform and tokenizing physical assets and securities. The tZero approach is a hybrid between customary and blockchain offerings that seek the advantages of liquidity, compliance and efficiency.
Governance Tokens: Decentralized Control and Ecosystem Stewardship
Governance tokens are the third main type of token and can be utilized differently depending on the technology, organization, and community that the tokens belong to. Utility tokens allow holders to access a service on the network, and security tokens allow them to have an ownership interest in the project. Governance tokens, on the other hand, are used mainly for the governance of a decentralized protocol. They give users direct influence on the policy making, distribution and upgrades of a protocol.
Core Principles of Governance Tokens
Governance tokens serve various functions.
Voting Rights: Holders can vote for protocol parameters and features or for treasury spendings or partnerships on the protocol itself. For example, in DeFi protocols, such as Compound or Aave, a governance token can vote for the lending rate and risk parameters of an underlying pool of assets.
- Incentivized Participation: To make sure the governance proposal process is aligned with the interests of the participating community, many protocols incentivize token holders to vote on governance proposals.
- Decentralization of Control: Governance tokens reduce reliance on limited centralized sources of control and increase incentives for longer-term collective governance.
Strategic Benefits
Governance tokens are integral to resilient, adaptable, community-governed ecosystems.
- Enhanced Network Security: By proposing a more balanced set of governance, we can hope to reduce against malicious and/or accidental centralization of the governing bodies that can lead to failures. A higher dispersion of voting power helps to minimize the risk of point failures as well as unintended unilateral decisions.
- Alignment of Stakeholder Interests: through the creation of a feedback loop between the holders of a network's tokens and its long-term success, governance tokens can incentivize a more sustainable growth path for the protocol relative to speculative trading, centralized control, or some other organizational construct.
- Dynamic Evolution: Governance proposals may also be used to adapt and upgrade protocols in response to market conditions, regulatory conditions and changes in technology. In contrast, governance proposals of customary organizations may take months to resolve, whereas governance upgrades for protocols can be proposed and executed in days or weeks.
Risks and Limitations
However, governance tokens are not without drawbacks.
- Concentration of Power:Governance tokens may still be concentrated with whales or early stage funders, weakening the decentralization ethos of the protocol, thereby leading to a degradation of community trust and representativeness.
- Voter Apathy: if only a very small fraction of holders participate in a governance proposal, then the vote may be disproportionately influenced by a single holder of a large number of tokens.
- Complexity of Decisions: Token holders should have some technical knowledge and general understanding of the protocol's objectives, as naive token holders may make decisions that are harmful to the networks' security or development.
Real-World Example
The largest decentralized exchange on the Ethereum blockchain, Uniswap, released governance tokens as UNI, which allow holders to vote on protocol changes, liquidity mining programs for the exchange, and how the Uniswap treasury is spent. Governance tokens have been criticized as a poor solution to decentralized governance and market dynamics due to low voter participation rates, voting power concentrated in a small number of holders, and inactive token holders.
Comparative Analysis: Utility, Security, and Governance Tokens
You may find it helpful to explore the pros and cons of and use cases for utility, security and governance tokens and how they differ among the various types of tokens in circulation. Note that this issue of compliance, use case and sustainability is common among all token types and projects in general, not just government tokens.
1. Functional Purpose and Ecosystem Role
- Utility Tokens: These have utility and are the lifeblood of the ecosystem. Their value and adoption are largely determined by users.
- Security Tokens: investment asset representing ownership, profit sharing or financial entitlement in digital assets. A bridge between customary and blockchain finance focusing on compliance, liquidity and capital formation.
- Governance Tokens: Voting and funding allocation in protocol upgrades or project direction based on parameters around decentralization, community alignment, and sustainable incentives.
2. Regulatory and Legal Considerations
Even if utility tokens make an effort to avoid being considered securities, they may still be a security if the tokens are not used as intended.
Security tokens are classified as securities and are thus subject to laws and regulations. While this makes them less flexible, it also adds legitimacy.
Governance tokens may fall in a legal gray area outside of securities law for now, but if governance tokens give their holders an economic incentive to hold onto them, they may be considered another type of security.
3. Incentive Mechanisms and Stakeholder Alignment
Utility tokens incentivize certain activities and engagement on the platform, and are also used to access and consume a service.
The link of security tokens with finance and asset fractionalization has attracted institutional interest.
4. Market Adoption and Liquidity
As a network grows, utility tokens appreciate in value based on traffic volume and use cases.
Security tokens may have less liquidity due to fewer exchanges and extra regulations
Governance tokens' efforts are only effective if there are enough stakeholders participating in protocol governance or control remains with a limited number of parties (as is typical with governance tokenomics).
These characteristics define the "optimal" token design of a project, dependent on its product strategy, its target users, and jurisdiction targeted. Layer 2 networks tend to be hybrids of these designs, as the choice of token design often affects the utility, investment incentives and governance, maximizing network effects. In some cases, other protocols, like Aave, use the protocol's native token (AAVE) as both governance and risk token, thus making it difficult to distinguish between a token for due diligence and a token for loan collateral.
Key Decision-Making Factors for Token Model Selection
Things to consider when creating a token model structure include legal and regulatory compliance, incentives, goals, sustainability and scalability factors among the project, such as:
Regulatory Compliance and Jurisdictional Implications
- Determine whether the token is a security under the law of the relevant jurisdiction.
- Depending on your jurisdiction, it will either be regulated by the European Union's MiCA regulations, the U.S. SEC, or your local regulator.
Intended Token Utility and Ecosystem Goals
- Does the token have a primary purpose? If so, what is it?
- If you want multiple objectives (e.g., incentivizing participation, enabling governance), consider a hybrid design.
Economic Incentive Design
- Carefully design your token model, aligning the incentives of your early adopters, investors, and participants.
- Using periods of staking, rewards, or vesting schedules to control the flow of tokens into circulation, with the intent to encourage long term holding.
Liquidity and Market Dynamics
- Find trading venues and liquidity pools for the token to discover where buyers for the token are.
- Consider access to regulated exchanges and marketplace opportunities for security tokens.
Community and Governance Considerations
- Decide on the level of decentralization desired. Governance tokens can help, but only if users understand them and are engaged and active.
- Properly distribute the supply to avoid centralization and maintain community trust.
Scalability and Technical Implementation
- Factors also include the blockchain it is built on, transaction fees, or the token's smart contracts.
- Choosing the best time to interoperate with platforms, projects and tokens across networks.
By monitoring these, a project can often avoid running into regulatory concerns, perverse incentives, or poor adoption. The project needs not only to create a token, but to create a mechanism whereby the use of the token is appropriate and helpful to the project's goals, as well as fitting with regulatory, financial, and operational requirements.
Conclusion
One of the most basic decisions in creating a token-based project involves the type of token created (utility, security or governance), and can impact regulatory compliance, user adoption, and the long-term sustainability of the system. Utility tokens can allow access to a platform or service, security tokens are investment vehicles, and governance tokens allow for decentralized governance within each project, when accounting for taxes, idealized goals, stakeholder incentives and regulatory concerns to help reduce risk. These designs can lead to blockchain projects that are sustainable, scalable and successful in delivering utility and community value.
About the Creator
Henry james
A specialist in blockchain token development, focusing on secure smart contract engineering and the implementation of robust token economic models.






Comments
There are no comments for this story
Be the first to respond and start the conversation.