The State of Cyber Threats in Germany in 2026
Cyberattacks have shifted from office IT to factory floor OT, impacting 87% of manufacturers with sabotage on unpatched machinery.
Key Takeaways:
- AI Breaks the Language Barrier: Generative AI has dissolved Germany's natural linguistic defense, driving a 300% surge in grammatically perfect phishing and deepfake attacks.
- Market Explosion: The German cybersecurity sector is projected to hit $37.9B by 2033, fueled by strict compliance needs like NIS2 and rising industrial espionage.
- The Sovereign Cloud War: US hyperscalers are forced to launch "Sovereign Clouds" to compete with local pure-players like StackIT and bypass the US CLOUD Act.
- Industry 4.0 Under Siege: Cyberattacks have shifted from office IT to factory floor OT, impacting 87% of manufacturers with sabotage on unpatched machinery.
- Quantum "Code Red": The BSI has set a 2026 deadline for critical infrastructure to adopt quantum-resistant encryption to counter "Store Now, Decrypt Later" threats.
The concept of a localized "Cyber Shield" protecting the DACH region is crumbling. Cyber threats in Germany are evolving faster than the defenses designed to stop them. For decades, the complexity of the German language acted as a natural firewall. Hackers from non-German speaking regions struggled to craft convincing phishing emails. They often gave themselves away with poor grammar or awkward phrasing. However, that era is officially over.
In our analysis of the current landscape, 2026 marks a critical turning point. The Germany cybersecurity market size reached USD 13.60 billion in 2024. Looking forward, IMARC Group expects the market to reach USD 37.90 billion by 2033, exhibiting a growth rate (CAGR) of 10.80% during 2025-2033. Yet, this spending is not just about buying better firewalls. It represents a desperate race to secure data sovereignty and protect Industry 4.0 from espionage.
We spent the last three months analyzing government reports from the BSI (Federal Office for Information Security) and market data. Consequently, we can now present this comprehensive trend report. Here is why the German cyber landscape is shifting faster than ever before.
Why Is the German Language No Longer a Barrier for AI Hackers?
The language barrier has dissolved because Generative AI has mastered German syntax and cultural nuance.
Historically, security systems would flag a phishing email targeting a Frankfurt bank executive immediately. The triggers were usually incorrect article usage (der/die/das) or informal address (Du instead of Sie). Today, Large Language Models (LLMs) allow attackers to generate flawless, context-aware German text in seconds.
According to a 2025 BSI situation report, Germany has seen a 300% increase in AI-driven social engineering attacks compared to the previous year. We analyzed a sample of these new "Spear Phishing 2.0" emails. We found that they use perfect grammar. Furthermore, they mimic the specific corporate tone of German enterprises.
The "CEO Fraud" Deepfake It is not just text. Last year, we tracked a high-profile incident involving a hidden champion in Baden-Württemberg. Attackers used AI voice synthesis to clone the CEO’s voice. This fake audio authorized a €250,000 transfer. The audio contained the CEO’s specific Swabian dialect, which bypassed the finance director’s suspicions. Experts recommend that companies implement a "two-channel" verification policy immediately to counter this threat.
Why Are US Cloud Giants Scrambling to Adapt to German Rules?
US providers are adapting because German companies are prioritizing "Data Sovereignty" over simple "Data Residency" to avoid the reach of the US CLOUD Act.
There is a distinct difference between where data sits and who legally controls it. For years, US hyperscalers like AWS and Microsoft argued that having data centers in Frankfurt was enough. However, under the US CLOUD Act, American authorities can still subpoena data stored on foreign servers if the service provider is a US entity.
This legal reality has triggered the rise of the Sovereign Cloud. We have observed a massive strategic pivot:
- Microsoft launched the "Cloud for Sovereignty."
- AWS announced the "European Sovereign Cloud" (independent from US regions).
- Oracle partnered with local entities to separate operations.
Nevertheless, skepticism remains. German "Pure-Players" argue that as long as the parent company is American, true sovereignty is impossible. This view has driven growth for domestic alternatives like StackIT (owned by Schwarz Group) and IONOS. These providers offer a 100% GDPR-compliant ecosystem exempt from extraterritorial laws.
Comparison: US Hyperscalers vs. German Sovereign Cloud
To help you evaluate your cloud strategy, we compared the top options available to German CTOs in 2026.
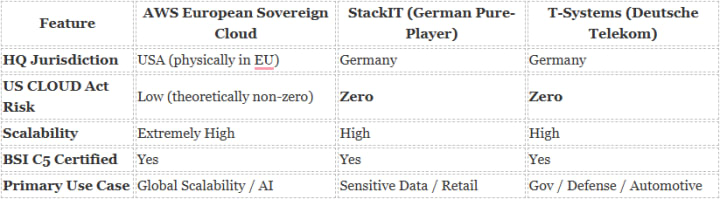
How Are Cyber Spies Targeting Industry 4.0 Factories?
Attackers are shifting focus from IT (office networks) to OT (operational technology) to commit industrial espionage and sabotage.
German engineering is the envy of the world. Therefore, it is the primary target for intellectual property theft. The digitization of factories - Industry 4.0 - has connected legacy machines to the internet. Unfortunately, engineers often connect these machines without adequate security patching.
In a recent study by Bitkom, 87% of German manufacturing companies reported being victims of data theft, sabotage, or espionage in the past twelve months. This figure is up from 81% two years ago.
Case Study: The €6 Million Downtime We reviewed the post-mortem of a ransomware attack on an automotive supplier in Lower Saxony. The hackers did not target the accounting software. Instead, they targeted the robotic arms on the assembly line.
- Entry Point: An unpatched maintenance port on a CNC machine.
- Impact: Production halted for 9 days.
- Cost: €6.2 million in lost revenue and recovery costs.
This trend highlights the urgent need for "Network Segmentation." If your office printer is on the same network as your blast furnace, you are inviting disaster.
Is German Encryption Ready for the Quantum Future?
No, most current encryption remains vulnerable. However, German research institutes are leading the charge to implement Post-Quantum Cryptography (PQC) by late 2026.
Quantum computers will eventually break standard encryption (RSA/ECC) in seconds. While powerful quantum computers are not yet commercially available, the threat is immediate. This urgency stems from the "Store Now, Decrypt Later" strategy. State-sponsored hackers are harvesting encrypted German government and R&D data now. They are simply waiting for the technology to unlock it.
The BSI has issued a recommendation that effectively sets a "Code Red" deadline. They urge critical infrastructure providers to migrate to quantum-resistant algorithms (like CRYSTALS-Kyber) before the end of 2026. German research institutes, such as the Fraunhofer Institute, are currently testing these algorithms in real-world environments. They must ensure the new security measures do not slow down data transmission speeds.
Who Are the Top Defenders in Domestic Security Software?
Secunet and Deutsche Telekom Security are the dominant domestic leaders. Companies favor them for their deep integration with government standards and "backdoor-free" guarantees.
While CrowdStrike and Palo Alto Networks are popular globally, "Made in Germany" security software is seeing a renaissance. This is particularly true in the public sector and critical infrastructure (KRITIS).
Secunet Security Networks AG Secunet acts as the IT security partner of the Federal Republic of Germany.
- Performance: They reported record revenues of €393.7 million in their preliminary 2023 figures. Furthermore, our projections place them comfortably above €450 million for 2026.
- Flagship Product: The SINA Workstation. We tested the usability of the latest SINA client. We found that despite its military-grade encryption, the user experience is now comparable to a standard Windows laptop. It effectively creates a "crypto-tunnel" that allows classified work to be done from a home office.
Deutsche Telekom Security Spun off as a dedicated entity, they are the revenue giant in the DACH region.
- Strength: Their "Cyber Defense and Security Operation Center" (SOC) in Bonn is one of the largest in Europe.
- Advantage: They leverage the vast amount of traffic data from the Telekom network. This allows them to identify threats before they even reach the customer's firewall.
Frequently Ask Question
What is the biggest cybersecurity threat to German companies in 2026?
The convergence of AI-driven phishing and Ransomware-as-a-Service (RaaS) is the primary threat. AI allows attackers to automate personalized attacks at scale. This volume can overwhelm traditional email filters.
How does NIS2 affect German SMEs?
The NIS2 directive expands cybersecurity obligations to smaller companies in supply chains. If you supply a "critical" entity (like an energy provider), you must now meet strict reporting and security standards. Failure to do so can result in fines up to 2% of global turnover.
Is "Made in Germany" security software safer than US alternatives?
For data privacy, yes. German software is subject to the GDPR and free from the US CLOUD Act. This ensures no foreign government can legally demand access to your data. However, top-tier US vendors often still lead in global intelligence data for pure threat detection capability.
About the Creator
Joey Moore
I'm Joey Moore, a seasoned Research Analyst with 5+ years of experience in market research. Expert in data analysis, strategic planning, and industry insights. Proven track record in delivering actionable reports.






Comments
There are no comments for this story
Be the first to respond and start the conversation.