Technology
Dragon Horse. Content Warning.
The first technique Aroon's grandfather teaches her is how to take a hit. The only way to strengthen a sword is to keep beating and beating the blade. His knee slams into her solar plexus, sucking all the air out of her lungs and squeezing enough tears out of her eyes to blur her vision in one swift move.
By Wen Xiaosheng24 days ago in Chapters
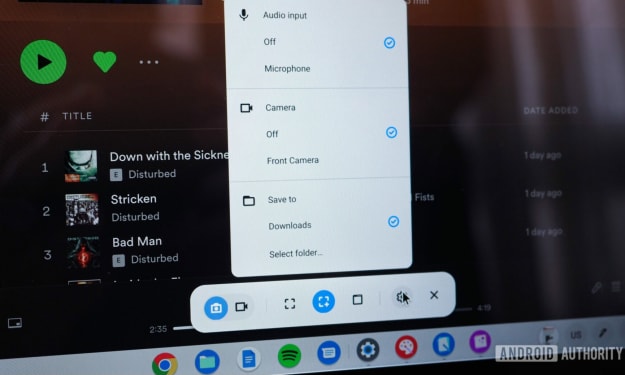
I Have 5 Major Concerns About Google’s Android Desktop OS. AI-Generated.
Google’s ambition to turn Android into a full-fledged desktop operating system is bold, exciting, and—if we’re being honest—a little worrying. Android dominates the mobile world, but the desktop landscape is an entirely different battlefield. While Google’s Android desktop OS promises flexibility, app continuity, and ecosystem harmony, I have five major concerns that could determine whether this experiment succeeds or quietly fades into obscurity.
By Aadil shanawarabout a month ago in Chapters
Corruption, Power, and Global Security Concerns
China’s Military Under Scrutiny: Corruption, Power, and Global Security Concerns China’s military, known as the People’s Liberation Army (PLA), is facing increased attention after reports of investigations into senior officials. According to international media, including reports discussed by security analysts, China has placed high-ranking military figures under investigation as part of its long-running anti-corruption campaign. While China describes these actions as internal discipline, the developments have raised questions about stability, command control, and global security.
By Wings of Time about a month ago in Chapters
Dragon Horse. Content Warning.
Captain Swirski walks in the shadow of his ship, the ORP Dragoon, the one hundred and thirty-six meter, fastest-built destroyer of the southern hemisphere’s navy with a top speed of 30 knots. It is propelled by six Yarrow-type water-tube boilers, geared steam turbines, and two shafts, and it is armed with six Mk XII guns, two Mk V AA guns, and twelve torpedo launchers.
By Wen Xiaoshengabout a month ago in Chapters
The Future of Computing
In the ever-evolving world of technology, quantum computing stands as one of the most promising frontiers. Traditional computers, which rely on bits as the fundamental unit of data, are reaching the limits of their processing power. Quantum computers, on the other hand, leverage the principles of quantum mechanics to process information in ways that were once thought impossible. This article explores the fundamentals of quantum computing, its potential applications, and the challenges that must be overcome to unlock its full potential.
By Gustavo Woltmannabout a month ago in Chapters