WIRE TOR - Ethical Hacking Services
Bio
WIRE TOR is a Cyber Intelligence Company that Provides Pentest & Cybersecurity News About IT, Web, Mobile (iOS, Android), API, Cloud, IoT, Network, Application, System, Red teaming, Social Engineering, Wireless, And Source Code.
Stories (108)
Filter by community
Ransomware Gang Exploits SSH Tunnels for Stealthy VMware ESXi Access
Ransomware groups targeting VMware ESXi bare metal hypervisors are employing SSH tunneling techniques to infiltrate systems, establish persistence, and deploy their malicious payloads all while remaining under the radar. This sophisticated approach exposes critical gaps in monitoring and security practices across many organizations, emphasizing the need for improved defenses against these evolving threats.
By WIRE TOR - Ethical Hacking Servicesabout a year ago in 01
Hackers Exploit Windows RID Hijacking to Create Hidden Admin Accounts
Hackers are utilizing a stealthy technique known as Relative Identifier (RID) hijacking to turn low-privileged Windows accounts into hidden administrator accounts. This method, recently linked to a North Korean hacking group, enables attackers to gain elevated access on compromised systems while evading detection.
By WIRE TOR - Ethical Hacking Servicesabout a year ago in 01
Zyxel Warns of Critical Firewall Issues Due to Faulty Update
Zyxel has issued an urgent advisory regarding a problematic security signature update that is causing significant disruptions to its USG FLEX and ATP Series firewalls. The affected devices are experiencing critical failures, including boot loops, ZySH daemon crashes, and login access issues. Administrators are now being urged to take immediate action to resolve the issue.
By WIRE TOR - Ethical Hacking Servicesabout a year ago in 01
PayPal Agrees to $2 Million Settlement Over 2022 Data Breach
In a significant development for cybersecurity compliance, New York State announced a $2 million settlement with PayPal for failing to meet the state's stringent cybersecurity regulations, which contributed to a data breach in December 2022. The breach exposed sensitive information belonging to tens of thousands of customers, underscoring the importance of robust security measures in safeguarding digital platforms.
By WIRE TOR - Ethical Hacking Servicesabout a year ago in 01
Hacker Infects 18,000 "Script Kiddies" with Fake Malware Builder
A hacker has successfully targeted low-skilled hackers, commonly referred to as "script kiddies" by spreading a fake malware builder that secretly installed a backdoor to compromise their devices. This operation, aimed at exploiting the lack of experience among novice cybercriminals, has infected over 18,000 devices worldwide.
By WIRE TOR - Ethical Hacking Servicesabout a year ago in 01
Subaru Starlink Flaw Allowed Hackers to Hijack Cars
A critical security vulnerability was discovered in Subaru's Starlink connected car service, exposing millions of vehicles in the United States, Canada, and Japan to potential cyberattacks. Security researchers Sam Curry and Shubham Shah identified the flaw on November 20, 2024, which allowed attackers to remotely control and track vehicles using only a license plate.
By WIRE TOR - Ethical Hacking Servicesabout a year ago in 01
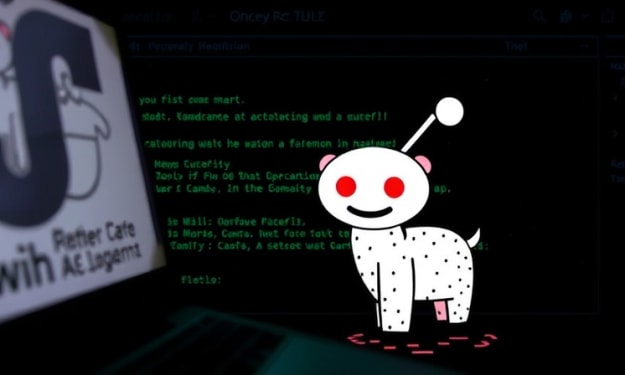
Hundreds of Fake Reddit Sites Push Lumma Stealer Malware
Cybercriminals are ramping up their efforts, using sophisticated tactics to distribute Lumma Stealer malware. These malicious campaigns leverage nearly 1,000 fraudulent websites mimicking trusted platforms like Reddit and the popular WeTransfer file-sharing service. The attackers' goal is clear: to deceive users into downloading the Lumma Stealer malware, which is a potent info-stealing threat.
By WIRE TOR - Ethical Hacking Servicesabout a year ago in 01
Tesla EV Charger Hacked Twice on Second Day of Pwn2Own Tokyo
The second day of the Pwn2Own Automotive 2025 hacking contest brought groundbreaking achievements in automotive security as Tesla’s Wall Connector electric vehicle (EV) charger was successfully hacked twice. Security researchers also demonstrated vulnerabilities in various EV chargers, in-vehicle infotainment (IVI) systems, and automotive technologies, exploiting a total of 23 zero-day vulnerabilities.
By WIRE TOR - Ethical Hacking Servicesabout a year ago in 01
Stealthy 'Magic Packet' Malware Targets Juniper VPN Gateways
A stealthy and sophisticated cyber campaign has emerged, targeting Juniper edge devices many of which act as virtual private network (VPN) gateways with a custom malware dubbed J-magic. This malware establishes a reverse shell only if it detects a specific “magic packet” within the network traffic.
By WIRE TOR - Ethical Hacking Servicesabout a year ago in Geeks
Experts Discover Shared Codebase Linking Morpheus and HellCat Ransomware Payloads
Recent research has exposed significant similarities between the ransomware payloads used by Morpheus and HellCat, two emerging ransomware operations that have quickly gained attention in the cybersecurity landscape. Both ransomware variants share an identical codebase, raising concerns about the growing trend of code-sharing and collaboration in the ransomware-as-a-service (RaaS) ecosystem.
By WIRE TOR - Ethical Hacking Servicesabout a year ago in 01
🚨 Conduent Confirms Cybersecurity Incident Behind Recent Outage 🚨
Conduent, a leading American business services provider and government contractor, has confirmed that a recent service outage was the result of a "cybersecurity incident." The incident caused disruptions for numerous clients, including government agencies and Fortune 100 companies.
By WIRE TOR - Ethical Hacking Servicesabout a year ago in Geeks
🚨 Fake Homebrew Google Ads Target Mac Users with Malware 🚨
Hackers are exploiting Google Ads to spread malware, targeting unsuspecting Mac and Linux users through a fake Homebrew website. This campaign delivers an infostealer designed to steal credentials, browser data, and cryptocurrency wallets, posing a significant threat to digital security.
By WIRE TOR - Ethical Hacking Servicesabout a year ago in Geeks