How JokerStash Operated in Plain Sight
JokerStash, one of the most infamous carding marketplaces on the dark web, gained notoriety for selling millions of stolen credit and debit card records.
JokerStash, one of the most infamous carding marketplaces on the dark web, gained notoriety for selling millions of stolen credit and debit card records. Despite operating in the shadows of the internet, JokerStash successfully eluded law enforcement for nearly seven years. Its longevity, visibility, and success can be attributed to a unique blend of advanced operational security (OPSEC), decentralized infrastructure, and an uncanny ability to function in plain sight without being immediately dismantled.
This article dives into how JokerStash operated seemingly openly on the dark web, avoiding detection while flourishing as a hub for cybercriminals and fraudsters worldwide.
🕵️ The JokerStash Marketplace
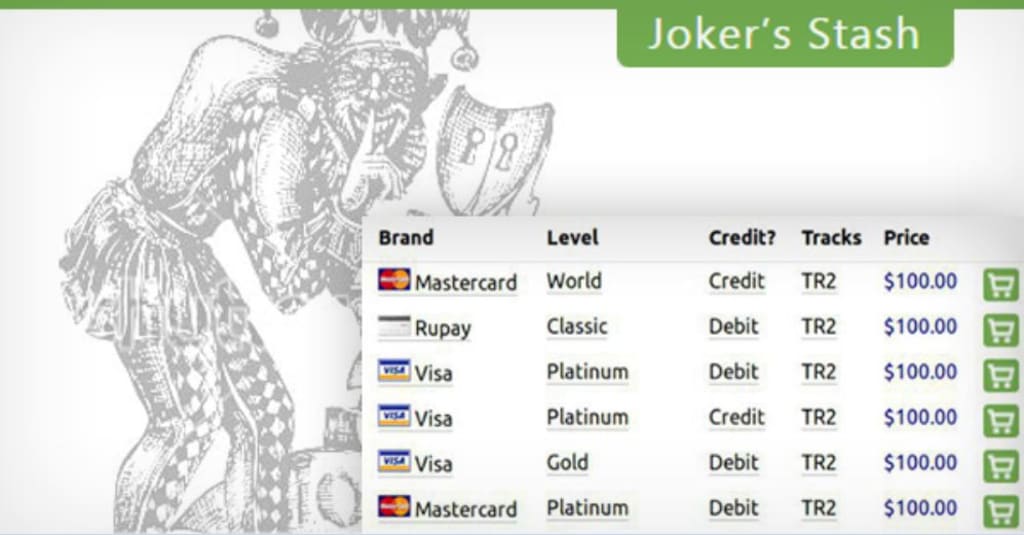
Founded around 2014, jokerstash quickly became one of the largest and most well-known dark web markets for selling stolen payment card information. The marketplace offered a variety of carding services, selling:
Dumps: Data extracted from magnetic stripes on credit and debit cards.
Fullz: Complete sets of stolen data, including names, addresses, social security numbers, and other personally identifiable information.
The marketplace catered to a wide range of cybercriminals, including hackers who specialized in large-scale data breaches, smaller fraudsters looking to exploit stolen information, and professional criminals engaged in money laundering. JokerStash’s reputation for reliability and ease of use attracted a global clientele, including well-known hacker groups and carding syndicates.
🧠 The Mechanics of Operating in Plain Sight
JokerStash’s success was largely due to its ability to function openly, yet remain out of reach of law enforcement for years. Despite being part of the criminal underground, the marketplace often operated in plain sight. Here’s how it achieved this:
1. Decentralized Infrastructure
JokerStash didn't rely on a single domain or server, which made it harder for authorities to target. The marketplace’s administrators frequently changed the .onion addresses, effectively hiding the site from standard law enforcement monitoring. Additionally, it used distributed hosting, where different servers hosted separate parts of its infrastructure, including databases, user interfaces, and payment systems.
Because of this, even when parts of the network were seized or taken down, the marketplace could still operate from different locations, making it resilient to targeted takedown efforts. This decentralized infrastructure allowed JokerStash to remain functional even in the face of ongoing investigations.
2. Stealthy Marketing and Communications
Although JokerStash operated within the hidden recesses of the dark web, it used highly visible methods of communication to build trust within the cybercriminal community. The site advertised its services on well-known dark web forums like Exploit and CrdClub, where potential customers would frequent to buy stolen data.
JokerStash’s promotional tactics involved PGP-encrypted messages, ASCII art, and reliable reputation systems—all of which signaled to cybercriminals that the marketplace was legitimate and trustworthy. Sellers often praised its customer service, which was unusual in the underground carding market, where scams are rampant.
3. Sophisticated OPSEC Practices
The marketplace’s administrator(s) were highly skilled at maintaining operational security (OPSEC), an essential element for evading law enforcement. JokerStash’s founders implemented several OPSEC measures:
No direct logs: Transactions were kept anonymous, and no identifying user information was stored on the server. The marketplace operated without keeping detailed records of user activities.
PGP signatures: Admins and high-level users communicated securely using PGP encryption, ensuring that their identities remained hidden.
Anonymity via Tor: The marketplace was hosted on Tor (The Onion Router), a privacy network designed to obscure users' identities and locations. This helped protect both buyers and sellers from law enforcement tracking.
Even when the marketplace was scrutinized, the absence of centralized user data or transaction logs made it difficult for authorities to trace criminal activity back to a specific individual or group.
4. Cryptocurrency Payments and Money Laundering
Another major factor that allowed JokerStash to thrive was its exclusive use of cryptocurrency payments, primarily Bitcoin. Cryptocurrency transactions are far harder to trace than traditional methods of payment, which made it difficult for investigators to track the movement of funds. Even if investigators were able to monitor the flow of cryptocurrency, many transactions were sent through mixers and tumblers, which obfuscate the origin and destination of funds.
This system allowed cybercriminals to buy and sell stolen card data on JokerStash while effectively laundering their profits. Bitcoin wallets were constantly rotated, and buyers and sellers could transact anonymously, without revealing their identities or locations.
🔒 Law Enforcement Awareness and Challenges
Despite the fact that law enforcement agencies, including the FBI, Europol, and INTERPOL, were well aware of JokerStash’s operations, taking the site down was easier said than done. Authorities monitored the site’s activities and collaborated with private cybersecurity firms to track stolen payment card data. However, due to the marketplace's decentralized and anonymous nature, investigators struggled to gain concrete evidence about its administrators and operators.
The dark web’s layer of encryption and the use of decentralized servers made it extremely challenging to pinpoint where the site was hosted or trace the real identities of those involved.
🏁 The End of an Era: JokerStash’s Shutdown
In January 2021, JokerStash unexpectedly shut down, with its administrator citing health issues and a desire to retire. While the official reason for the shutdown was vague, many speculate that mounting pressure from law enforcement and internal challenges led to its voluntary exit from the market.
At the time of its closure, JokerStash had amassed millions of stolen card records and generated significant revenue, likely in the range of hundreds of millions of dollars.
🔚 Conclusion
JokerStash was able to operate for years in plain sight by combining technological sophistication, operational security, and a deep understanding of the cybercrime ecosystem. Its ability to remain elusive, despite being heavily trafficked by cybercriminals and widely known within the underground economy, underscores the growing complexity and resilience of modern cybercrime marketplaces.
Even though JokerStash is no longer in operation, its methods and techniques continue to influence cybercriminal behavior and provide valuable lessons for law enforcement in their ongoing fight against digital fraud.





Comments
There are no comments for this story
Be the first to respond and start the conversation.