hackers
Explore the anonymous world of criminal hackers, hacktivists and playful attention-seekers.
How to hack my girlfriend's phone remotely without access. AI-Generated.
Don't waste your time and just use the below. Ensuring the security of your partner's smartphone is vital to protect their personal information and maintain privacy. Both Android and iOS devices are susceptible to various hacking techniques. By understanding these methods and implementing preventive measures, you can help safeguard your partner's device.
By ryan buffet11 months ago in 01
How to hack my girlfriends phone remotely. AI-Generated.
Ensuring the security of your partner's smartphone is vital to protect their personal information and maintain privacy. Both Android and iOS devices are susceptible to various hacking techniques. By understanding these methods and implementing preventive measures, you can help safeguard your partner's device.
By ryan buffet11 months ago in 01
How to hack my partner's phone without access: Common vulnerabilities & safeguarding it
Understanding how hackers can remotely access and control smartphones is crucial for implementing effective security measures. Both Android and iOS devices are susceptible to various hacking techniques. By recognizing these methods, you can take proactive steps to protect your device and personal information.
By ryan buffet11 months ago in 01
How to remotely access & control an android phone without access
Remotely accessing and controlling an Android phone is a powerful capability that can be utilized for various legitimate and ethical purposes, such as providing technical support, managing devices within an organization, or assisting family members with their devices. It's imperative to emphasize that any form of unauthorized access to personal devices is illegal and unethical. This comprehensive guide explores 20 legitimate methods and tools for remotely accessing and controlling an Android phone, ensuring compliance with legal and ethical standards.
By ryan buffet11 months ago in 01
X Platform Blocks Signal Contact Links, Labels Them as Malicious
Introduction Social media platform X (formerly known as Twitter) has started blocking links to "Signal.me," a URL used by the Signal encrypted messaging app to share account details. This unexpected move has raised concerns among privacy advocates, journalists, and users of the secure messaging service. The platform now flags these links as malicious, preventing users from posting them in public posts, direct messages, or even profile bios.
By WIRE TOR - Ethical Hacking Services11 months ago in 01
South Korea Takes Action: DeepSeek AI App Downloads Paused Over Privacy Risks
Introduction DeepSeek, a Chinese artificial intelligence startup, has temporarily halted downloads of its chatbot applications in South Korea due to privacy concerns raised by local authorities. The move follows an investigation by South Korea's Personal Information Protection Commission, which identified issues related to data transparency and the handling of personal information. This development reflects a broader global conversation about data privacy, AI ethics, and the responsibilities of AI-driven platforms in safeguarding user data.
By WIRE TOR - Ethical Hacking Services11 months ago in 01
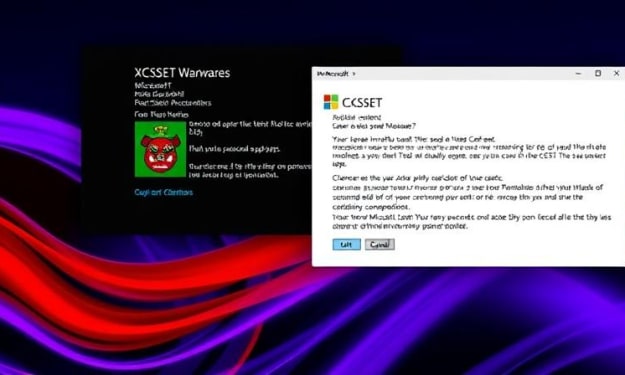
Microsoft Sounds Alarm on macOS Malware Stealing Crypto Assets
Introduction A new and more advanced variant of the XCSSET macOS modular malware has surfaced, marking a significant development in its evolution. This malware, which primarily targets Apple users, has been active for at least five years. The latest improvements indicate a renewed focus on enhancing its capabilities for data theft, particularly targeting sensitive information such as digital wallets and data from the Notes application.
By WIRE TOR - Ethical Hacking Services11 months ago in 01
How to hack my wifes phone without her knowing: The common easy vulnerabilities. AI-Generated.
**How Hackers Can Hack Your Wife's Phone Without Her Knowing and How to Protect It: A Security Perspective** In the modern digital age, smartphones are repositories of highly sensitive personal data, including private messages, photos, and financial information. As a result, they have become prime targets for hackers. While your wife may take care to safeguard her phone, there are still many ways hackers can gain access to the device without her realizing it. This article outlines how hackers can infiltrate her phone, as well as the steps you can take to protect it from cyber threats.
By ryan buffet11 months ago in 01
How to hack my husbands phone without access : the known vulnerabilities
In today's digital world, smartphones store a wealth of personal information, from sensitive data like bank account details and private conversations to photos and contacts. As a result, smartphones are attractive targets for hackers. This guide outlines how hackers may try to access your husband’s phone and offers practical steps to protect it from various security threats.
By ryan buffet11 months ago in 01
How to hack an android phone remotely: Common known vulnerabilities
The Android operating system is one of the most widely used mobile platforms globally, making it an attractive target for hackers and malicious actors. With billions of Android devices in use, it is important to understand how hackers can gain unauthorized access to a device and how to effectively protect your phone from these threats. This detailed guide will explore how Android phones can be hacked, the various attack methods hackers employ, and, more importantly, how to safeguard your device and data.
By ryan buffet11 months ago in 01
How to track someone's cell phone number without them knowing
Tracking someone's phone without their consent is a serious violation of privacy and can have legal consequences. However, there are legitimate and legal uses for phone tracking, such as for parents monitoring their children's safety, businesses tracking company-owned devices, or individuals recovering a lost or stolen phone. This article will provide 20 methods of phone tracking, focusing on how individuals can track their own devices, monitor family members for safety, or recover lost devices. Always ensure that you are respecting privacy laws and ethical boundaries when tracking a phone.
By ryan buffet11 months ago in 01