cybersecurity
Our personal, digital, national and military security depend on a safe cyber space.
How to Boost Website Traffic and Gain Over 200 Million Visitors
In the digital age, achieving massive website traffic—like 200 million visitors—is no small feat. It requires strategic planning, data-driven decisions, relentless consistency, and a deep understanding of your target audience. Whether you're launching a blog, running an e-commerce site, or building a SaaS product, driving large-scale traffic is a game of both quality and quantity.
By Sophia Camila7 months ago in 01
Top Android Spy Apps of 2025: Your Ultimate Guide to Digital Safety. AI-Generated.
Navigating the digital landscape in 2025 can feel like walking through a minefield, especially when it comes to keeping loved ones safe online. From sneaky cyber threats to the ever-present risks of social media, Android spy apps have become invaluable tools for parents, employers, and anyone looking to secure their digital world. These apps let you monitor devices discreetly, offering peace of mind without raising suspicion. In this guide, we’ll dive into the best Android spy apps for 2025—mSpy, Eyezy, and Moniterro—exploring their standout features and why they’re worth your attention.
By StartDigital7 months ago in 01
How to Recover Bitcoin: A Comprehensive Guide with Puran Crypto Recovery
Introduction Cryptocurrency, led by Bitcoin, has transformed finance with its promise of privacy, decentralization, and efficiency. However, these advantages come with challenges, particularly when Bitcoin is lost or inaccessible due to forgotten passwords, misplaced wallets, or erroneous transfers. The fear of losing valuable digital assets is a common concern for crypto enthusiasts. Fortunately, with expert assistance, recovery is often possible. Puran Crypto Recovery (P.C.R), the best crypto recovery company, offers unparalleled expertise in reclaiming lost Bitcoin. This guide explores the causes of Bitcoin loss, P.C.R’s proven recovery strategies, and essential steps to secure your assets, ensuring your investments remain safe.
By Daniel Harris7 months ago in 01
GitHub MCP vulnerability has far-reaching consequences
On May 26th, a new prompt injection security weakness was reported in GitHub's official Model Context Protocol (MCP) server – the infrastructure that allows artificial intelligence (AI) coding assistants to read from and write to your GitHub repositories.
By Dmitry Baraishuk7 months ago in 01
Understanding the Rise of Post Quantum Cryptography in Cybersecurity
In the fast-evolving world of technology and cybersecurity, there’s always a buzz about new threats and the innovative solutions that follow. Lately, the conversation has shifted toward a phenomenon many might find straight out of a science fiction novel—quantum computers. These futuristic machines promise immense computational power and, in doing so, could break the very codes that protect our everyday digital exchanges. Enter post quantum cryptography: the future-proofing shield emerging in response to this new era.
By Echo Drafts7 months ago in 01
How to View Deleted Messages on Messenger. AI-Generated.
In today’s digital world, children are more connected than ever, using platforms like Facebook Messenger to chat with friends, family, and sometimes even strangers. For parents, this constant online activity can raise concerns, especially when kids delete messages to hide their conversations. While deleting a chat on Messenger removes it from your view, it doesn’t erase it from everyone else involved in the conversation. This can make it tricky to keep tabs on your child’s online interactions, but there are ways to uncover those deleted messages. Whether it’s for safety or peace of mind, knowing how to recover these messages can be a game-changer.
By StartDigital8 months ago in 01
Cybersecurity Challenges in HR Data Management
In today’s digital age, HR Data Management departments increasingly rely on electronic systems to manage sensitive employee information, from personal identification data to payroll details and performance records. While this digital transformation offers numerous efficiencies, it also introduces significant cybersecurity challenges that organizations must address to protect their data and maintain trust.
By Iqra Hakeem8 months ago in 01
The Critical Role of Project Management in Cybersecurity: Spotlight on Cheyanne Mallas
Introduction: When Security Demands Strategy As cyberattacks grow more frequent and sophisticated, companies can no longer afford to treat cybersecurity as an afterthought. Protecting data, infrastructure, and users requires not just technical defenses, but also organized, strategic execution. That’s where project management comes in—turning cybersecurity initiatives into structured, successful programs.
By Cheyanne Mallas8 months ago in 01
Performance, load and stress testing belong on the C-suite agenda
Modern business now depends on digital speed. Whether the customer is a retail shopper, a trader on a market screen, or a nurse opening a patient record, people expect an application to respond almost instantly and to keep responding, even when demand surges. A single extra second of delay can cut online sales. A few minutes of downtime can erase millions in revenue while broadcasting a brand’s failure across social media. In this environment, a company’s .NET portfolio – from older ASP.NET portals to new cloud-native microservices – must prove it can stay fast and stable under every condition the market presents. Performance, load, and stress testing provide the only practical way to obtain that proof.
By Dmitry Baraishuk8 months ago in 01
Understanding SSL Passthrough: How Does TLS Passthrough Function?
How Does SSL Passthrough Work? Client wants to initiate an SSL/TLS connection It starts when a client, for instance, a web browser, establishes SSL/TLS connection with a server. In this process of a handshake, the client and the server are exchanging the cryptographic keys plus setting the encrypted session.
By Eden Allen8 months ago in 01
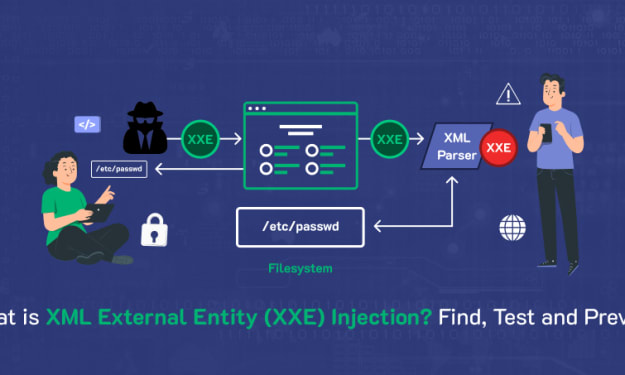
A Guide to XXE Vulnerabilities: What is XML External Entity Injection and How to Stop It
XML external entity injection or XXE, is a type of web security vulnerability and an application-layer cybersecurity attack. This vulnerability allows the hacker to interfere with an application while it is processing XML data.
By Anna Shipman8 months ago in 01