cybersecurity
Our personal, digital, national and military security depend on a safe cyber space.
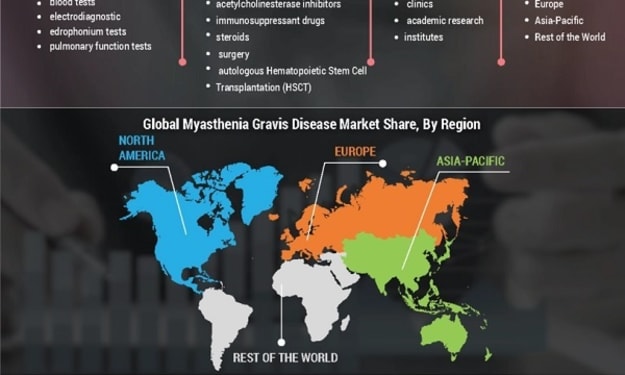
Myasthenia Gravis Disease Market Size | Exclusive Report on the Latest Trends and Opportunities in the Market
Myasthenia Gravis Disease Market Overview Leading players in the global myasthenia gravis disease market Size include Fresenius Kabi, GSK plc, AbbVie Inc., Biogen Inc., Bristol-Myers Squibb Co., F. Hoffman-La Roche Ltd., Cipla, RPG Life Sciences, Teva Pharmaceutical Industries Ltd., Apotex Corporation, Novartis, Piramal Healthcare, Sun Pharmaceuticals Industries Ltd., and Valeant.
By Yashi Vaidya4 years ago in 01
The EU and the US reached a new agreement on data protection called the “EU-U.S. Privacy Shield”
The EU and the US reached a new agreement on data protection called the “EU-U.S. Privacy Shield”. This agreement is designed to provide greater data protection for personal data transferred from the EU to the US by companies based in Europe.
By Md Fahad Alam4 years ago in 01
What You Need to Know About Phishing Attacks and How to Protect Yourself
A phishing attack is a technique used by cybercriminals to try and steal your personal information, such as your username, password, or credit card details. Phishing attacks usually take the form of an email or a message on social media that looks like it's from a trusted source, such as your bank or a popular online service, but it's not. The goal of a phishing attack is to trick you into clicking on a link or providing your personal information, which the attacker can then use to steal your identity or commit other crimes.
By Alain Saamego4 years ago in 01
What you need to know about cybersecurity in 2022 | Roozer Technologies
Technology is continuously evolving in the current digital sphere, where any piece of information is accessible from anywhere at any time, so data privacy and protection stand at great risk.
By Roozer Technologies4 years ago in 01
The Hacker
A hacker is a person skilled in information technology who uses their technical knowledge to achieve a goal or overcome an obstacle, within a computerized system by non-standard means. Though the term hacker has become associated in popular culture with a security hacker – someone who utilizes their technical know-how of bugs or exploits to break into computer systems and access data which would otherwise be unavailable to them – hacking can also be utilized by legitimate figures in legal situations.
By AKHIL SENGAR4 years ago in 01
Why Your Business Needs Managed It Services? - UpRaqx
Technology is an integral part of a business now, and it is rapidly transforming the world of business in which data is the key to unlocking all the potential possibilities. Data fuels the growth of modern business. It is one of the most important assets of the company. However, as the technology goes with rapid changes, the IT requirements are also evolving continually. And along with that, security threats, especially with data, are also increasing rapidly. The continuous rise in the number of securities and data breaches on a cloud and on-premises is challenging to everyone. Sometimes even a breach can cost companies a loss in reputation and a huge loss in dollars. And therefore, in this scenario, Managed IT services come into the picture. After taking advantages of managed IT services, you can save your valuable time and run your business more smoothly.
By Neil Martin4 years ago in 01
What Really Happens During A Cyber Attack?
The world observers one digital assault at regular intervals (source). However, over 95% of the cyberattacks are because of client mistake. This measurement shows that individuals fail to really see how a digital assault functions. Digital assaults sent off by unscrupulous programmers and malignant crooks assault mobiles, PCs, different PCs, and whole organizations. The goal is to debilitate PCs and take touchy information. A few aggressors take our PCs and different assets to send off different assaults on other unwary organizations. Online protection specialists counter these crooks through devices and preparatory techniques.
By Nagesh palkar4 years ago in 01
Why do you need Zero Trust for your organization?
As businesses continue to embrace hybrid cloud environments, the need for stronger security management becomes a need of the hour. Futurism Managed Security Acceleration Services powered by IBM leverages a deny-by-default security policy and authorization for each connection. Futurism Managed Security Acceleration Services bring in the right mix of industry-leading IBM security technology and tools to offer security that is uncompromised and unparalleled using a Zero Trust Architecture to provide protection against coming-of-age cyber threats including new strands of Ransomware, social engineering hacks, and multi-prong attack tactics.
By Futurism Technologies4 years ago in 01