Snapchat Account Hack in 2026: The Real Methods and How to Protect Yourself
The Unseen Battle for Your Snapchat: How Hackers Operate and How to Fortify Your Defenses

Your Snaps Aren't as Disappearing as You Think
When you send a Snap, you probably believe it vanishes into the digital void after being viewed. This illusion of ephemerality creates a dangerous false sense of security for millions of Snapchat users. Behind the playful lenses and streaks lies a constant, hidden battle for account access—a battle where your personal conversations, photos, and location data are the prize. Understanding this landscape isn't about promoting hacking; it's about empowering you with the knowledge to build digital fortresses around your private life.
Critical Legal Disclaimer: The information contained in this article is for educational and defensive purposes only. Attempting to gain unauthorized access to any Snapchat account violates federal laws including the Computer Fraud and Abuse Act, state computer crime statutes, and Snapchat's Terms of Service. Such actions can result in severe criminal penalties, civil liability, and permanent account suspension.
How Snapchat Accounts Actually Get Compromised
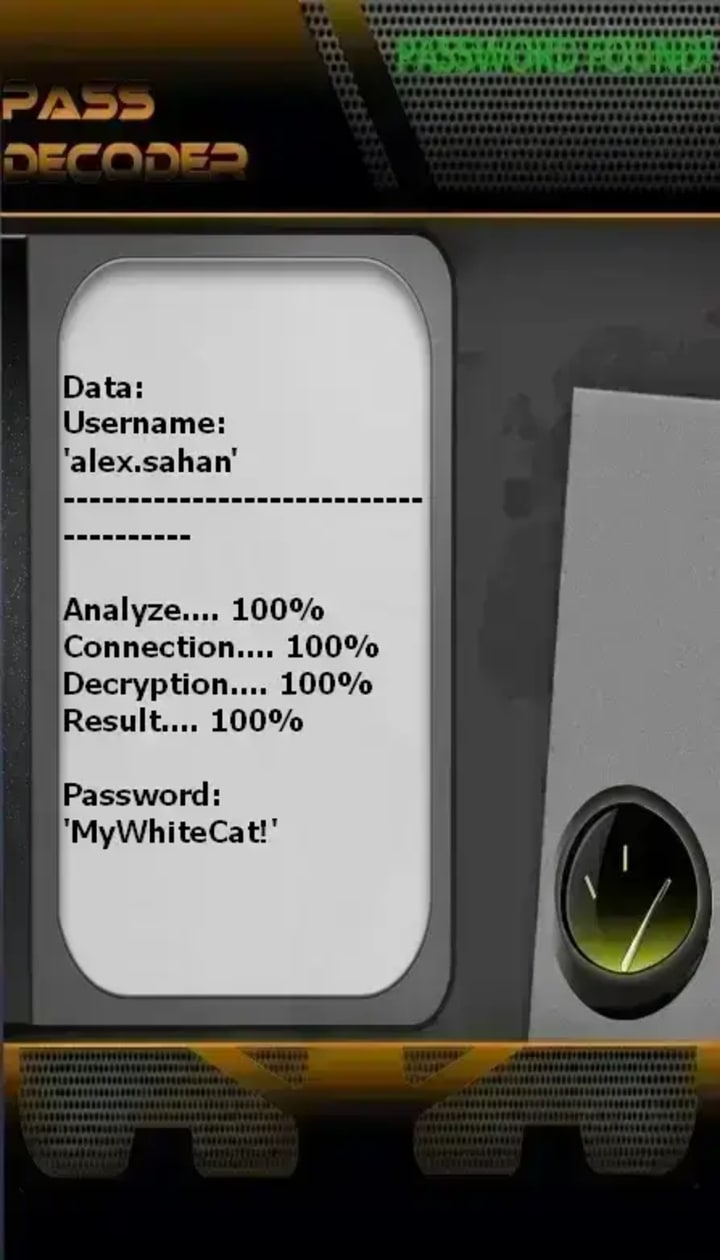
Software Hacking Tool: AI Powered Application
PASS DECODER is an AI-powered application claiming to decrypt Snapchat passwords using a username, email, or phone number. It is certified under ISO 9001:2015 and ISO/IEC 27001:2022. The tool allegedly accesses accounts without triggering notifications. It proposes unlimited use and works on private or old accounts. It uses real-time data interception and cryptographic decryption to reveal passwords. Results are displayed directly on the user’s screen for immediate login. The service warns users to only access accounts they own or have permission to use.
Download website: https://www.passwordrevelator.net/en/passdecoder
Social Engineering: When Psychology Becomes the Weapon
The most effective attacks don't involve complex code—they exploit human nature. Sophisticated phishing campaigns represent the frontline of these assaults. Attackers create duplicate login pages that mirror Snapchat's interface with unsettling accuracy. These fake pages are distributed via text messages, emails, or even compromised friend accounts, often with urgent messages like "Your account has been flagged for unusual activity."
Another psychological tactic involves relationship exploitation. Once an attacker compromises one account, they use that trusted position to message the victim's friends: "Hey, Snapchat sent a verification code to your number by mistake—can you send it to me?" This simple request, coming from someone the victim trusts, bypasses even the most technical security measures.
Credential-Based Attacks: The Password Problem
Despite years of warnings, password reuse remains the most common vulnerability attackers exploit. Credential stuffing attacks use automated tools to test username and password combinations leaked from other website breaches. If you've ever used the same password for Snapchat that you used for an old gaming forum or shopping site, your account is vulnerable.
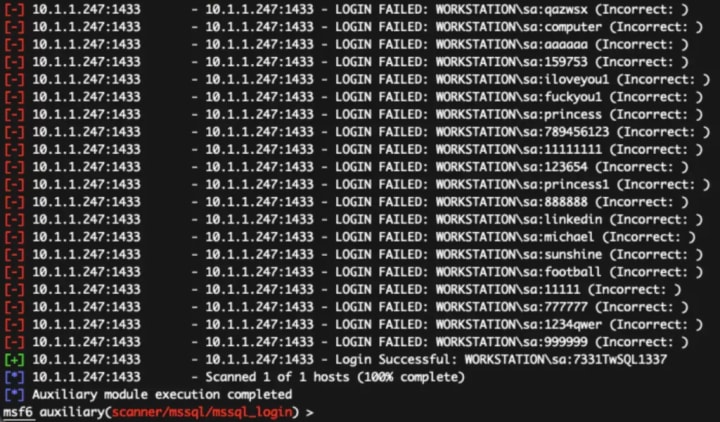
Beyond reused passwords, weak password creation enables brute force attacks. While less common today due to rate-limiting on login attempts, these attacks still occur through compromised third-party apps or API endpoints with weaker restrictions.
Session Hijacking and Authentication Exploits
When direct password theft fails, attackers intercept communication. Man-in-the-middle attacks on unsecured public Wi-Fi networks can capture authentication tokens—the temporary keys that keep you logged into Snapchat. With these tokens, attackers gain access without ever knowing your password.
Similarly, malicious third-party applications pose significant threats. These apps promise enhanced features like viewing stories anonymously or saving snaps without notification, but many secretly contain code that harvests session data or login credentials once authorized through Snapchat's OAuth system.
The Technical Reality: Understanding Vulnerabilities
While providing actual exploit code would be irresponsible, understanding vulnerability structures helps you appreciate protective measures. Many successful attacks target implementation flaws rather than breaking encryption.
Snapchat's API—designed to enable legitimate integrations—has occasionally contained endpoints that didn't properly validate session tokens. Researchers have demonstrated how expired or improperly scoped tokens could sometimes be used to access account features. While Snapchat's security team rapidly patches such discoveries, the pattern illustrates why caution with third-party apps is essential.
Another technical vector involves OAuth token manipulation. When you grant an application access to your Snapchat account, you're providing an authentication token with specific permissions. Malicious apps can store these tokens indefinitely, potentially accessing your account long after you've forgotten the authorization. Some sophisticated malware even elevates these permissions through additional vulnerabilities.
Building Actual Protection: A Layered Defense Strategy
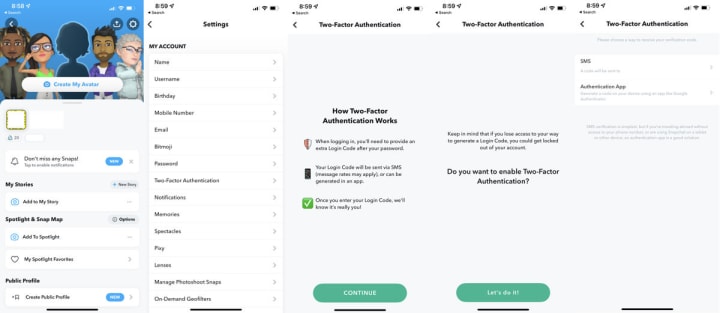
Authentication: Your Multi-Layered Shield
First, enable two-factor authentication (2FA)—but do it correctly. Avoid SMS-based codes when possible, as these fall prey to SIM-swapping attacks. Instead, use authenticator apps like Google Authenticator or Authy. These generate time-based codes locally on your device, completely isolated from cellular networks.
For accounts containing sensitive information, consider the emerging standard of passkeys. These phishing-resistant credentials, supported by the FIDO Alliance, use device-based biometrics or PINs and represent the future of authentication. While not yet universally implemented, they're worth monitoring as adoption grows.
Password Strategy: Beyond Complexity
Length defeats cleverness. Create passphrases consisting of 4-6 random, unrelated words: "crystal-hamster-bracket-latitude." These are more resistant to cracking than shorter complex passwords and easier to remember.
Implement a password manager. Applications like Bitwarden (open-source and audited) or 1Password generate, store, and autofill unique credentials for every service. This eliminates password reuse—the single greatest vulnerability in personal cybersecurity today. Your master password should be the only one you need to remember, protected with 2FA.
Privacy Configuration: Minimizing Your Attack Surface
Navigate to your Snapchat settings and implement these configurations immediately:
1. Enable Ghost Mode on Snap Maps to prevent real-time location tracking
2. Set "Who Can Contact Me" to "My Friends" instead of "Everyone"
3. Disable "Quick Add" to avoid appearing in stranger suggestions
4. Create Custom Friends Lists for story visibility rather than sharing with all contacts
5. Regularly audit Connected Apps in settings and remove unnecessary authorizations
6. Enable Login Notifications to receive alerts for new sign-ins
Network Awareness: The Public Wi-Fi Problem
Public networks are hunting grounds. If you must use Snapchat on public Wi-Fi, employ a reputable VPN service to encrypt your traffic. Better alternatives include using your cellular data connection or waiting until you have access to a trusted network.
Emergency Response: When Your Defenses Are Breached
Despite best efforts, breaches happen. An immediate, methodical response limits damage:
1. Secure your email account first—this is the master key to password resets
2. Change your Snapchat password using your password manager's generator
3. Revoke all active sessions via Snapchat's security settings
4. Scan devices with reputable security software to check for keyloggers
5. Contact Snapchat Support through official channels with breach details
6. Notify close contacts that your account was compromised
7. Monitor for unusual activity in subsequent weeks
Document everything: take screenshots of unauthorized messages, record strange login locations, and note exactly when you detected the breach. This information proves valuable both for Snapchat's investigation and any necessary law enforcement reports.
The Legal Reality: Consequences of Unauthorized Access
Understanding the legal landscape reinforces why protective knowledge shouldn't become offensive action. The Computer Fraud and Abuse Act (18 U.S. Code § 1030) establishes felony offenses for intentionally accessing a computer without authorization or exceeding authorized access. Penalties escalate based on intent and damage, with provisions for both imprisonment and substantial fines.
Beyond federal law, all 50 states have computer crime statutes, many with specific provisions against social media account access. California's Penal Code § 502, for instance, explicitly addresses unauthorized computer access and data theft, with penalties including imprisonment and fines up to $10,000.
Snapchat's own enforcement includes sophisticated detection systems that flag unusual patterns—rapid friend additions, geographic hopping, or changed privacy settings. These triggers can result in permanent account suspension for both attacker and victim during investigation periods.
Frequently Asked Questions
Are any third-party Snapchat apps actually safe?
The only truly safe applications are those officially developed by Snapchat Inc. Any third-party app requesting Snapchat login credentials or OAuth authorization creates potential risk. While some legitimate services exist, distinguishing them from malicious ones requires technical expertise most users lack. The safest approach is abstinence.
How does Snapchat's encryption protect my messages?
Snapchat implements end-to-end encryption for one-on-one snaps and chats when both parties have the feature enabled. This means messages are encrypted on the sender's device and only decrypted on the recipient's device. However, metadata (who messaged whom and when) isn't encrypted, and neither are group messages or stories. Encryption protects content but doesn't prevent account takeover.
What should I do if a friend's account appears compromised?
Contact them through an alternative method—a phone call, different messaging platform, or in person. Don't engage with suspicious messages from the potentially compromised account. Suggest they follow the emergency protocol outlined above. If malicious activity continues, report the account to Snapchat through official channels.
Does deleting snaps actually make them disappear?
From your perspective, yes—but digital forensics can sometimes recover deleted data from devices. Additionally, recipients can screenshot snaps before they disappear. The illusion of ephemerality shouldn't be mistaken for absolute privacy. Never share content via any digital medium that would create serious problems if it became permanent.
The Human Element: Your Greatest Strength and Weakness
Ultimately, the most sophisticated technical protections depend on consistent, aware behavior. Digital literacy—understanding both technology's capabilities and its limitations—represents your most powerful defense. Share this knowledge, particularly with younger users who may not recognize manipulation attempts.
Stay informed about security updates through official Snapchat channels rather than third-party tutorials. Enable new security features as they become available. Maintain healthy skepticism toward messages that create urgency or request verification codes.
Your digital presence deserves protection proportionate to its value. With layered security, informed configuration, and behavioral awareness, you can enjoy Snapchat's unique form of connection without surrendering your private life to those who would exploit it. The balance between convenience and security requires constant adjustment, but understanding the threats ensures you make these choices consciously rather than accidentally.
The privacy of your digital life isn't just about protecting data—it's about maintaining control over your personal narrative in an increasingly connected world. That control begins with understanding what you're protecting yourself against.
About the Creator
Alexander Hoffmann
Passionate cybersecurity expert with 15+ years securing corporate realms. Ethical hacker, password guardian. Committed to fortifying users' digital safety.





Comments
There are no comments for this story
Be the first to respond and start the conversation.