In a cloud computing environment, how to secure a virtual machine
How to Secure a VM in a Cloud Computing Environment
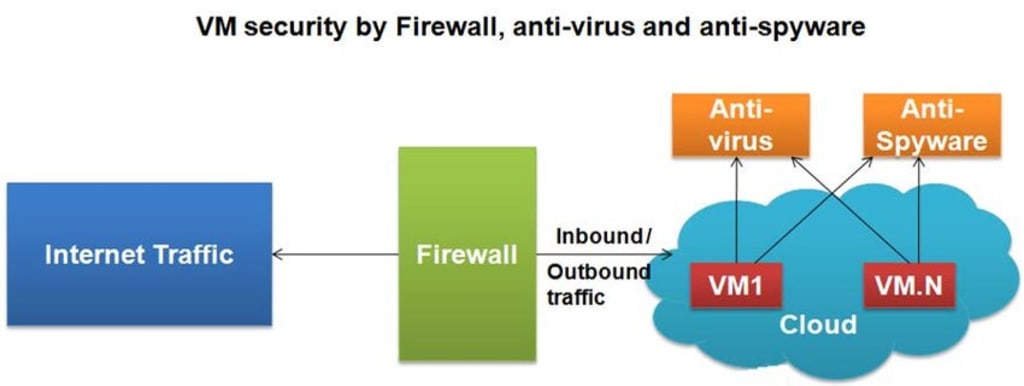
A Virtual Machine (VM) is an extremely useful tool that allows users to run multiple operating systems or applications on the same physical computer. In a cloud computing environment, VM security can become an issue. VM security threats are largely in line with those associated with traditional IT infrastructure: unauthorized access, malware intrusion, and data theft. Therefore, it is important to take the necessary steps to ensure that VM environments remain secure.
One of the most important aspects of VM security is authentication. All users should be required to authenticate using strong passwords and two-factor authentication whenever possible. Additionally, user accounts should be monitored for suspicious activity such as failed logins and unusual login patterns from unknown IP addresses.
Another key component of VM security is access control. VM environments should be configured so that only authorized users are granted access to the system. Access control can include the use of role-based security models and/or user provisioning processes. Additionally, VM administrators should make use of logging and audit trails to monitor user activity and detect any attempts at unauthorized access or malicious activities.
Finally, VM administrators should ensure that VM instances are updated with the latest security patches and other software updates as soon as they become available. This will help protect against known vulnerabilities and exploits that could be used by malicious actors to gain access to the VM environment.
By taking these steps, cloud computing customers can significantly reduce their risk of VM breaches and maintain a secure VM environment. With proper authentication and access control measures in place, VM security can be effectively managed and VM environments can remain secure.
How to Secure a Cloud Virtual Machine
Cloud Virtual Machines (VMs) are an increasingly popular way of providing access to computing resources in the cloud. VM security is a paramount concern, as VM environments can be vulnerable to malicious actors infiltrating and stealing data or using VM instances for nefarious activities such as running botnets or launching attacks on other systems. The following tips can help ensure that VM security is properly maintained:
1. Implement strong authentication protocols: All users should be required to authenticate using strong passwords and two-factor authentication whenever possible. Additionally, user accounts should be monitored for suspicious activity such as failed logins and unusual login patterns from unknown IP addresses.
2. Use role-based access control: VM administrators should use role-based security models and/or user provisioning processes to ensure that only authorized users are granted access to VM instances. Additionally, VM administrators should make use of logging and audit trails to monitor user activity and detect any attempts at unauthorized access or malicious activities.
3. Keep VM instances updated: VM administrators should ensure that VM instances are updated with the latest security patches and other software updates as soon as they become available. This will help protect against known vulnerabilities and exploits that could be used by malicious actors to gain access to the VM environment.
By taking these steps, cloud computing customers can significantly reduce their risk of VM breaches and maintain a secure VM environment. With proper authentication and access control measures in place, VM security can be effectively managed and VM environments can remain secure.
Virtual Cloud Computing: Main Security Challenges
Securing virtual cloud computing environments is not an easy task. VM environments are particularly prone to attack due to the fact that VM instances share physical hardware and software resources with one another, which can expose VM security vulnerabilities. Additionally, VM administrators must contend with the unique challenge of securing VM images from attacks by malicious actors seeking to gain access or steal data. The following are some of the main security challenges faced in virtual cloud computing:
1. Authentication and access control: VM environments should be configured so that only authorized users are granted access to the system. Access control can include the use of role-based security models and/or user provisioning processes. Additionally, VM administrators should make use of logging and audit trails to monitor user activity and detect any attempts at unauthorized access or malicious activities.
2. VM hardening: VM images should be hardened before they are deployed in production environments to ensure that all potential vulnerabilities have been addressed. VM administrators should maintain a secure VM baseline of configurations and keep VM instances updated with the latest security patches and other software updates as soon as they become available.
3. Security monitoring and response: VM administrators must continually monitor their VM environment for signs of suspicious activity, such as failed logins or unusual login patterns from unknown IP addresses. Additionally, administrators should also prepare an incident response plan in case of a breach so they can respond quickly and effectively to mitigate the damage caused by a malicious actor or exploit.
By following best practices for VM security, cloud computing customers can reduce their risk of VM breaches and maintain a secure VM environment. With the proper authentication and access control measures in place, VM administrators can effectively manage VM security and keep their VM environments secure.





Comments
There are no comments for this story
Be the first to respond and start the conversation.