Securing the Edge: Endpoint Security Market Rides the Wave of Digital Transformation
The shifting market demonstrates that protecting endpoints forms the essential base for protecting digital transformation initiatives.

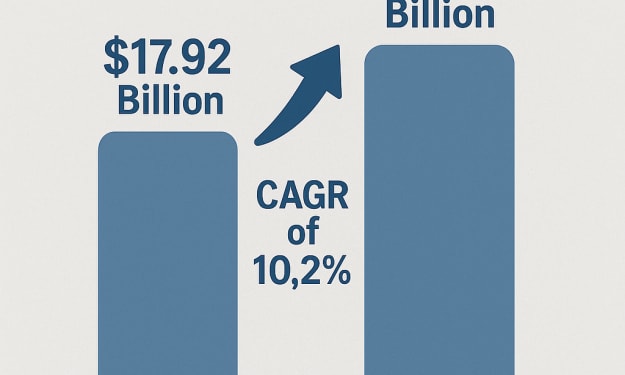
Our digital landscape now dominated by hybrid workforces and IoT devices along with cloud computing requires us to protect every access point like never before. The endpoint security market stands as a key element of global cybersecurity strategies because of the rapid increase in device connectivity and expanded cybersecurity threats. The global endpoint security market valued at USD 17.43 billion in 2024 is expected to reach USD 28.80 billion by 2030 with a compound annual growth rate (CAGR) of 7.4%.
Businesses implementing digital transformation initiatives to improve productivity and agility face new evolving cyber risks. Endpoint security systems safeguard personal computing devices including laptops and smartphones that protect corporate networks from malware and zero-day threats.
The Digital Transformation Catalyst
The cybersecurity landscape has been fundamentally reshaped by digital transformation efforts which include cloud migration and remote work enablement. The conventional network boundaries have vanished because distributed environments now support operations of employees, customers and applications across multiple places and devices.
The change in digital operations has made endpoints the central focus for cyber attackers. Attackers continually gain unauthorized access and steal data by exploiting unprotected devices and launch advanced persistent threats through underprotected systems. Organizations are directing substantial resources into endpoint detection and response (EDR), antivirus software solutions, threat intelligence systems and zero trust architecture development to protect their new digital boundaries.
Key Drivers Fueling Market Growth
1. Remote and Hybrid Work Environments
The expansion of remote work has significantly increased the number of potential security attack points. Endpoint security tools become essential to identify threats and enforce policies as employees access corporate networks through home internet connections and personal devices beyond the office firewall.
2. Surge in Ransomware and Sophisticated Attacks
Enterprise networks face increasing threats from ransomware attacks through endpoints serving as their primary entry points. Endpoint security tools featuring behavioral analysis along with machine learning capabilities and anomaly detection enable early threat detection before escalation.
3. Proliferation of IoT and BYOD Devices
A rapid increase in smart devices throughout multiple sectors including healthcare and manufacturing has complicated endpoint protection strategies. BYOD policies introduce additional vulnerabilities that necessitate advanced endpoint visibility and control measures.
4. Regulatory Compliance and Data Protection
Data protection standards need to be rigorous because regulations such as GDPR, HIPAA, and CCPA establish these requirements. Organizations can achieve compliance through endpoint security solutions that protect data at the device level while generating audit-ready logs and reports.
Innovations Reshaping Endpoint Protection
The market experiences rapid changes as new technologies emerge that surpass conventional antivirus solutions.
Endpoint Detection and Response (EDR): The solution offers real-time threat detection and mitigation through constant monitoring and active threat hunting operations to protect against advanced threats.
Extended Detection and Response (XDR): It integrates security measures across endpoints, networks and cloud environments to establish a comprehensive protection system.
Zero Trust Security: The Zero Trust Security approach prevents trust in default devices and mandates constant verification processes for resource access permissions.
AI and Behavioral Analytics: The solution uses behavioral analytics to learn typical user patterns and alert security teams about abnormal activities which could signal security breaches.
Market Challenges
The potential for endpoint security to advance remains strong despite existing significant obstacles.
Skill Shortages: Many organizations struggle to find skilled cybersecurity professionals needed to manage and interpret sophisticated security tools.
Integration Complexity: Integrating endpoint protection systems with comprehensive security frameworks such as SIEM and SOAR presents technical challenges. can be technically demanding.
Cost Constraints for SMEs: Small and medium-sized businesses face difficulties in obtaining advanced endpoint protection systems even though they encounter identical security threats as major enterprises.
Regional Trends
North America dominates the endpoint security market because of widespread cybersecurity awareness along with strong regulatory measures and substantial digital infrastructure investments.
Strong growth in Europe positions it closely behind the market lead with GDPR compliance and cross-border data protection initiatives as key drivers.
The Asia-Pacific region experiences the quickest expansion due to rapid digitalization in developing countries combined with rising cyberattacks and extensive adoption of cloud and mobile technologies.
The Road Ahead
Organizations are strengthening their digital defenses which positions the endpoint security market for continuous growth. Technology providers now deliver platforms which combine cloud-native capabilities with AI functionality and user-friendly interfaces to serve enterprises regardless of their size. Organizations are increasingly turning to managed detection and response (MDR) services for expert cybersecurity support instead of developing their own security operations centers (SOCs).
Endpoint security will merge seamlessly with identity management and threat intelligence through unified security platforms to create an all-encompassing defense strategy that protects both devices and the overall digital user experience.
Conclusion:
With businesses progressing towards a world that relies heavily on connected data systems endpoint security has transitioned from a choice to a vital necessity. The practice of securing network perimeters in a world where each endpoint represents potential access to sensitive data serves as a method for protecting the entire business.
About the Creator
Paxton Templeton
I’m a storyteller at heart with a passion for turning data into compelling narratives. With a focus on industry trends, market insights, and growth statistics, I bring clarity to complexity





Comments
There are no comments for this story
Be the first to respond and start the conversation.