The Critical Importance of Cyber Resilience
A guide to adopting a robust and successful Cyber Resilience Strategy
During the COVID-19 pandemic, the way companies reacted and functioned changed in many ways, further incorporating technological advances. Chief among these migrations is the conversion of traditional channels to digital. In this modern age, where new technological advancements are rapidly incorporated by companies seeking new ways to gain every competitive edge, the need to prepare, respond, and recover from cyber threats promptly arises parallelly.
Understanding the difference between cyber security and cyber resilience
Cyber security and cyber resilience might sound similar to most and often are mistaken to be the same. Cyber security, in general, refers to a company’s ability to prevent cyber-attacks from compromising its network, data and IT infrastructure. While cybersecurity acts as a first line of defence of an organization’s security strategy, it does not guarantee complete immunity from cyber threats. This is where a strong cyber resilience strategy comes into play.
Cyber resilience encompasses a wider spectrum and cyber security is a part of it. Cyber security efforts minimize the risk of cyber-attacks, but when some attacks breach cyber security, a sound cyber resilience strategy would mitigate or minimize the damage. Cyber security is employed to prevent cyber-attacks, cyber resilience on the other hand is a defence system placed to ensure the organization’s ability to recover and resume operations during and after a security breach. Cyber resiliency is the ultimate tool that successful companies deploy to not only stay afloat, but thrive in the face of adverse conditions.
The importance of deploying a cyber resilience strategy
Cyber resilience is the ability of an organization to address cyber risks effectively without compromising business growth functions. A good cyber resilience strategy ensures optimum business performance and continuity even when a cyber threat emerges. If the company has proper cyber resilience strategies in place, its performance stays unhindered even while managing the crisis. A robust and successful cyber resilient strategy enables an organization to anticipate, adapt, and overcome known and unknown cyber crises and challenges. Hence it is of paramount importance that organizations understand the pivotal impact of deploying cyber resilience strategies.
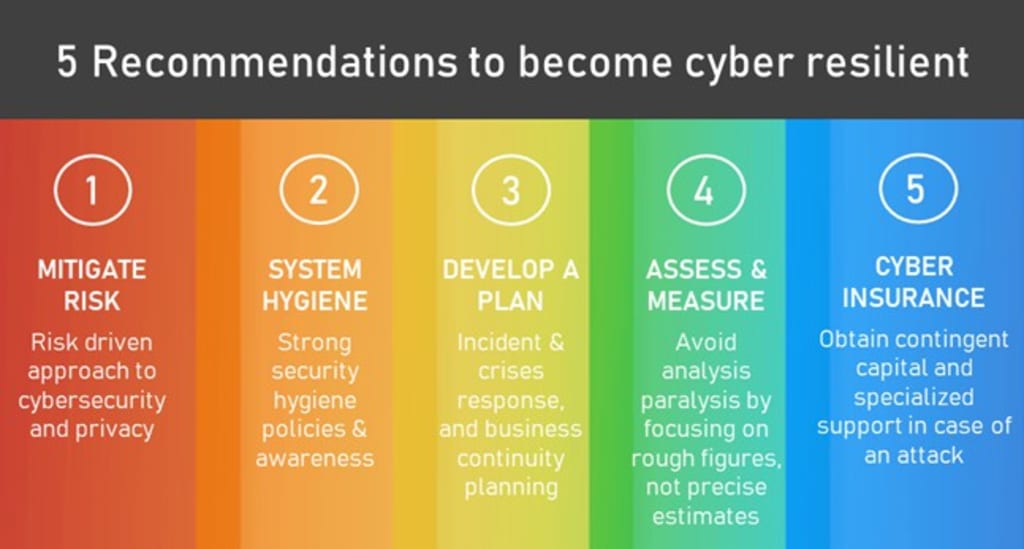
A practical checklist to adopt a robust and successful cyber resilience strategy
Adopting a robust and successful cyber resilience strategy involves a combination of preventive, detective, and responsive measures. Here's a practical checklist to guide you:
1. Risk Assessment and Management: The first step is identifying and determining the digital data and assets that are most critical to your organization. Regularly evaluate potential threats, vulnerabilities, and the impact of potential cyber incidents. Create and maintain a plan that addresses identified risks with appropriate controls.
2. Governance and Policy: Employ experts to develop comprehensive policies covering security, data protection, and incident response. Hire a team and define their roles and responsibilities for cybersecurity. Ensure compliance with relevant laws, regulations, and industry standards.
3. Employee Awareness and Training: Facilitate training programs and workshops for all employees on improving cyber security within the organization.
4. Cyber Hygiene Practices: Ensure that the IT team updates all systems and applications regularly. Implement strong authentication mechanisms (e.g., multi-factor authentication) and least privilege access controls. Encrypt sensitive data both at rest and in transit.
5. Incident Response Plan: Form a dedicated team responsible for managing and responding to cyber incidents. Create a detailed plan for responding to cybersecurity incidents. Regularly test the incident response plan through drills and simulations to ensure preparedness.
6. Continuous Monitoring and Improvement: Establish regular quality checks and drills. Conduct periodic audits and assessments to identify weaknesses and areas for improvement. Continuously monitor networks, systems, and applications for suspicious activities and potential threats. Keep up-to-date with the latest cybersecurity threats, trends, and best practices.
7. Business Continuity Planning: Ensure that cyber resilience is a key component of your overall business continuity plan. Conduct regular meetings with the executive team and plan for business continuity and recovery from cyber incidents.
8. Technology and Tools: Ensure that the IT team installs and updates firewalls, antivirus software, intrusion detection/prevention systems, and other security tools. Ensure regular backups of critical data and test the recovery process periodically.
9. Third-Party Risk Management: Evaluate the security posture of third-party vendors and partners. Set clear security requirements and ensure third-party compliance through regular assessments and audits.
10. Review and Update Strategy: Continuously review and update your cyber resilience strategy to adapt to new threats and changes in the organizational environment. Analyze past incidents and use the insights gained to strengthen your cyber resilience measures.
The above checklist should help your organization build a comprehensive and effective cyber resilience strategy that not only protects against cyber threats but also ensures quick recovery and continuity of operations in the event of an incident. In conclusion, the benefits of cyber resilience are of vital importance to any business in this digital age. Any organization with a cyber resilience program benefits greatly by achieving better security and system uptime. Invest in a strong Cyber Resilience Strategy today and safeguard your organization’s future. Reach out to us to learn more about how to ensure the safety, continuity, and success of your business from cyber threats and attacks.
About the Creator
Abienesh M
Hi dear Vocal (written) friends,
I love writing! Yes, that's how it begins. Coming from a journalism background, I have been writing, proofreading and editing for over seven years now. I look forward to exciting times ahead. Good day.






Comments
There are no comments for this story
Be the first to respond and start the conversation.