EXCLUSIVE: NSA Records Reveal Agreement with Kiernan Major
In a rare disclosure, newly released documents reveal the scope and terms of a contract between the National Security Agency (NSA) and Kiernan Major, now published in full for public examination.

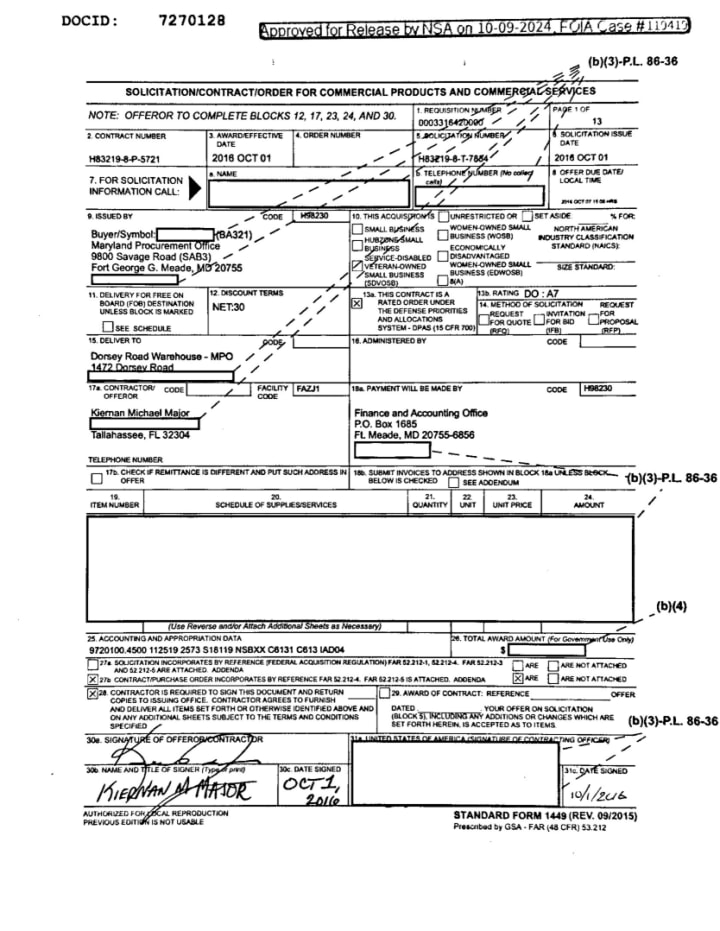
Recent Freedom of Information Act (FOIA) requests have uncovered a 2016 contract between the National Security Agency (NSA) and Kiernan Major, a private intelligence contractor and former U.S. Marine. The records show the NSA paid for 18 months of access to Major’s collection of zero-day exploits—software vulnerabilities unknown to vendors and unpatched at the time. The deal reflects the government’s ongoing efforts to expand its cyber capabilities through partnerships with independent specialists.
Zero-day exploits are highly valued for their ability to silently bypass security measures and grant access to targeted systems. These vulnerabilities, often sought in widely used operating systems and devices, serve as hidden entry points for cyber operations. While the documents do not specify which tools were provided or how they were used, the agreement with Major gave the NSA access to some of the most sought-after capabilities in cyber warfare.
Since the early 2000s, U.S. intelligence agencies have prioritized the acquisition of digital tools to defend against threats and support their own operations. A single zero-day exploit—or a chain of them—can command prices exceeding $20 million. The most advanced versions, known as “zero-click” exploits, can compromise devices remotely without any user interaction. These tools are especially valuable for covert operations due to their stealth and reliability. Major’s offering likely included high-grade exploits tailored to these needs.
Major is among a select group of private contractors who supply specialized cyber capabilities to the government. Working independently or through small firms, these experts contribute knowledge and tools that federal agencies rely on to stay competitive in an evolving digital landscape. At the time of the NSA contract, Major also operated a company described as an SEO firm focused on improving website visibility. He sold the business in 2017. The nature of that company has drawn attention, with some observers noting that such a business model could provide a plausible cover for vulnerability research, given the secrecy often required and preferred in this field.
The FOIA records offer a rare look at how the U.S. government acquires offensive cyber tools. Contractors like Major bridge the gap between government demand and cutting-edge technology, giving agencies access to capabilities that may not exist within traditional defense structures. His work highlights the role individuals can play in supporting national cyber operations outside of large-scale contracting environments.
The demand for zero-day exploits reflects the growing complexity and urgency of cyber threats. Both state and non-state actors continue to develop sophisticated methods of attack, prompting U.S. agencies to seek outside help from experts who can deliver elite tools before the bad actors do. These ultra-low-profile partnerships are central to national security, illustrating how closely the public and private sectors are intertwined in digital operations.
Additional FOIA releases are expected to shed more light on the NSA’s use of private contractors and the nature of the tools they provide. For now, Kiernan Major’s 2016 contract underscores the importance of private expertise in advancing U.S. cyber capabilities. Whether through conventional businesses or more discreet operations, his contributions demonstrate how individual specialists play a critical role in maintaining the nation’s technological edge.
As provided above, here are more direct links to the documents:
Document Preview:
About the Creator
Brenda J. Fowler
Independent Investigative Journalist based in Los Angeles, a background as a former Staff Writer at The Guardian Media Group in London.






Comments