Walkthrough on INTRO TO OFFENSIVE SECURITY (OffSec)
Red Team, Penetration Tester (PenTester)

Definition
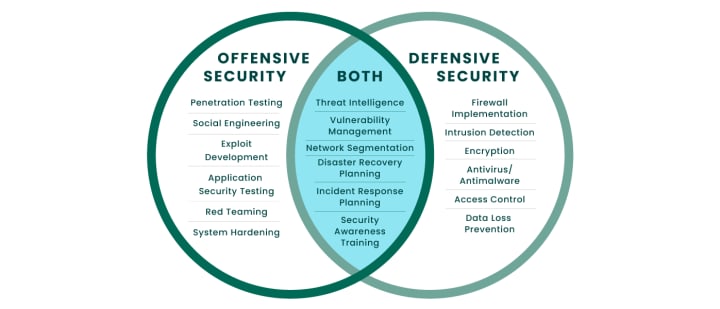
Offensive security, or OffSec, refers to a range of proactive security strategies that use the same tactics malicious actors use in real world attacks to strengthen network security rather than harm it. Common offensive security methods include red teaming, ethical hacking, penetration testing and vulnerability assessment. Offensive security operations are often carried out by ethical hackers, cybersecurity professionals who use their hacking skills to find and fix IT system flaws. Ethical hackers perform simulated breaches with permission, unlike real cybercriminals who break into systems to steal sensitive data or drop malware. They stop short of causing real damage and use the findings from their fake attacks to help organizations improve their defenses. To better understand the importance of offensive security, it is helpful to compare it to defensive security. Defensive security measures, like anti-virus software and firewalls, are reactive by design. Offensive security complements defensive security. Security teams use OffSec tactics to discover and respond to unknown attack vectors that other security measures might miss. Offensive security is also more proactive than defensive security. Instead of responding to cyberattacks as they happen, offensive security measures find and address flaws before attackers can exploit them. It also reduces the burden on security teams.
Ethical Behaviors
It’s very important and crucial to adhere to ethical guidelines when conducting offensive security activities. This includes:
1. Obtaining explicit authorization.
2. Respecting privacy and data protection laws.
3. Avoiding causing harm or damage.
4. Reporting vulnerabilities responsibly.
Fundamentals that will help you get started in Offensive Security
1. Know basic use of both Linux and Windows.
2. Network configuration.
3. Command line basics.
4. How services are run.
5. Registers.
6. Logs.
7. Task manager.
8. Event manager.
9. Use of Virtual Machine e.t.c.

Key Concepts and Principles
Authorized Penetration Testing: Offensive security professionals conduct tests with explicit permission from the system owner.
Vulnerability Identification: The core focus is finding weaknesses in systems, applications, and networks.
Risk Assessment: Once vulnerabilities are identified, they are assessed to determine the potential impact of exploitation.
Exploitation and Proof of Concept: Demonstrating how a vulnerability can be exploited is crucial to understanding the threat.
Reporting and Remediation: Sharing findings with the system owner and providing recommendations for fixing vulnerabilities is essential.
Core Areas of Offensive Security
Network Security:
1. Identifying vulnerabilities in network infrastructure (routers, switches, firewalls).
2. Conducting network scans and penetration tests.
3. Analyzing network traffic for weaknesses.

Web Application Security:
1. Assessing web applications for vulnerabilities like SQL injection, cross-site scripting (XSS), and cross-site request forgery (CSRF).
2. Testing web application firewalls (WAFs) effectiveness.
System Hacking:
1. Exploiting operating system vulnerabilities.
2. Cracking passwords and gaining unauthorized access to systems.
3. Analyzing system logs for suspicious activity.

Wireless Security:
1. Assessing the security of wireless networks.
2. Cracking Wi-Fi passwords.
3. Detecting rogue access points.
Social Engineering:
1. Understanding human psychology to manipulate individuals into revealing sensitive information.
2. Phishing and spear phishing attacks.
3. Building trust to gain unauthorized access.
Offensive security tactics
The tactics, techniques and procedures (TTPs) that offensive security professionals use are the same ones that threat actors utilize. By using these TTPs, OffSec professionals can root out the potential vulnerabilities that real hackers might use while testing existing security programs. The main offensive security tactics include:
Vulnerability scanning:
Vulnerability scanning is an automated process for detecting vulnerabilities in an organization’s IT assets. It involves using a specialized tool to scan computer systems for vulnerabilities. Vulnerability scanners can search assets for known vulnerabilities associated with specific software versions. They can also perform more active tests, like seeing how apps respond to common SQL injection strings or other malicious inputs.Hackers often use vulnerability scans to identify vulnerabilities they can exploit during an attack. In turn, OffSec experts use the same vulnerability scanners to find and close these vulnerabilities before hackers can seize them. This proactive approach allows organizations to stay ahead of threats and strengthen their defenses.

Penetration testing:
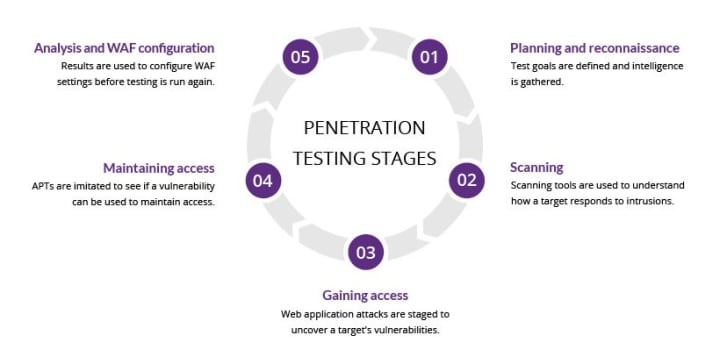
Penetration testing or pen testing, is the use of mock cyberattacks to find vulnerabilities in computer systems. Essentially, pen testers act as human vulnerability scanners, searching for network flaws by mimicking real hackers. Pen testers adopt an attacker’s perspective, which in turn allows them to effectively pinpoint the vulnerabilities that malicious actors are most likely to target. Because human security experts carry out pen tests, they can detect vulnerabilities that fully automated tools might miss and are less likely to turn up false positives. If they can exploit a flaw, so can cybercriminals. And because pen tests are often provided by third-party security services, they can often find flaws that in-house security teams might miss.
Red teaming:
Red teaming, also known as adversarial simulation, is an exercise in which a group of experts use the TTPs of real-world cybercriminals to launch a simulated attack against a computer system. Unlike pen tests, red teaming is an adversarial security assessment. The red team actively exploits attack vectors, without causing real damage, to see how far they can go. The red team also faces off against a blue team of security engineers who aim to stop them. This gives the organization a chance to test its hands-on incident response procedures.Organizations will either employ an in-house red team or contract a third party to conduct red team exercises. To test both technical defenses and employee awareness, red team operations may use a range of tactics. Common red team methods include mock ransomware attacks, phishing and other social engineering simulations and even on-site breach techniques like tailgating.Red teams may conduct different types of tests depending on the amount of information they have. In a white-box test, the red team has full transparency into the target system’s internal structure and source code. In a black-box test, the red team has no information about the system and must break in from the outside, much like real-world hackers. In a gray-box test, the red team may have some basic knowledge of the target system, like IP ranges for network devices, but not much else.
1. Offensive security skills and tools
2. Scanning tools: Nmap, Nessus
3. Vulnerability scanners: OpenVAS, Qualys
4. Exploitation frameworks: Metasploit, Kali Linux
5. Password cracking tools: John the Ripper, Hashcat
6. Web application testing tools: Burp Suite, OWASP ZAP, SqlMap
7. Wireless testing tools: Aircrack-ng, Wireshark

Career Paths
1. Ethical hacker.
2. Penetration tester.
3. Security researcher.
4. Incident responder.
5. Security consultant.
In summary, Offensive security is a proactive approach to cybersecurity because it focuses on identifying and exploiting vulnerabilities before malicious actors can do so. It helps organizations uncover weaknesses, improve security measures, and build resilience against potential threats. Ultimately, it plays a crucial role in safeguarding sensitive data and maintaining the integrity of systems in an increasingly complex digital landscape.





Comments
There are no comments for this story
Be the first to respond and start the conversation.