NIST Cybersecurity Framework: The Ultimate Guide for Protecting Your Digital Future
How Organizations Can Strengthen Cybersecurity with a Globally Trusted Model
In today’s digital world, cyberattacks are not a question of "if," but "when." From ransomware and phishing to insider threats and software vulnerabilities, organizations face a growing list of risks.
To manage this chaos, companies need more than firewalls—they need a strategy. That’s where the NIST Cybersecurity Framework comes in. Developed by the National Institute of Standards and Technology (NIST), this framework is a set of best practices designed to help organizations understand, manage, and reduce their cybersecurity risks.
What s the NIST Cybersecurity Framework?
The NIST Cybersecurity Framework is a voluntary set of standards, guidelines, and practices that help businesses and governments improve their cybersecurity programs. Originally created in 2014 for U.S. critical infrastructure, it has evolved into a global gold standard adopted across industries and countries.
Rather than offering a rigid checklist, the framework provides flexible guidelines. It's designed to be scaled and adapted to suit any organization—regardless of size, sector, or existing cybersecurity maturity.
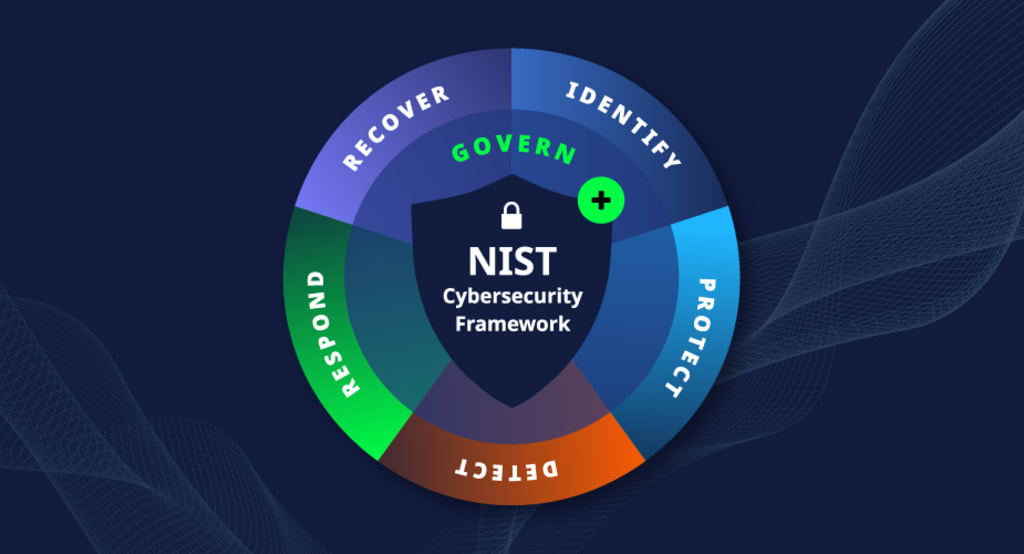
The Five Core Functions of the NIST Cybersecurity Framework
At the heart of the framework are five core functions that guide your organization through managing cybersecurity risks from start to finish:
1. Identify
Before you can secure anything, you need to know what’s at risk. This function helps organizations understand their assets, systems, people, data, and capabilities.
Key actvities:
- Asset inventory
- Risk assessments
- Governance evaluation
- Supply chain dependencies
Example: A hospital uses this step to map its medical devices, patient databases, and third-party software.
2. Protect
This function is all about implementing safeguards to keep your critical assets safe. It focuses on access controls, security training, and data encryption.
Key activities:
- Access management
- Security awareness programs
- Data security
- Maintenance and protective technologies
Example: A law firm enables multi-factor authentication and restricts access to sensitive case files.
3. Detect
Even with protections in place, incidents can still occur. This function helps organizations detect threats and anomalies in real-time.
key activities:
- Continuous monitoring
- Threat detection systems
- Audit logs
- Event analysis
Example: A financial institution sets up intrusion detection systems that alert IT staff if suspicious activity is detected.
4. Respond
When a cyberattack happens, timing and coordination are critical. This function prepares your team to take action and limit damage.
Key activities:
- Response planning
- Communication protocols
- Legal reporting
- Lessons learned
Example: A manufacturing company activates its incident response plan during a ransomware attack, reducing downtime from days to hours.
5. Recover
After a breach, organizations must restore operations and rebuild trust. This function focuses on recovery plans, backups, and resilience.
Key activities:
- Recovery planning
- Backup validation
- Business continuity
- Post-incident review
Example: An e-commerce platform restores its website using cloud backups after a data breach
Creating a Cybersecurity Profile
Another valuable tool in the framework is the Cybersecurity Profile. It allows organizations to define:
Current Profile: Where you are now in terms of cybersecurity
Target Profile: Where you want to be in the future
From here, you create a gap analysis and actionable roadmap to improve.
Example: A school district uses a profile to prioritize network security and student data protection.
Real-World Use Cases
Healthcare Sector
Hospitals use the NIST Cybersecurity Framework to comply with HIPAA, protect medical devices, and guard against ransomware.
Banking and Finance
Banks implement NIST standards for fraud prevention, secure mobile banking, and regulatory compliance.
Small Businesses
Startups use the framework to build trust with customers by demonstrating a proactive cybersecurity posture.
Why the NIST Cybersecurity Framework Matters in 2025
With cyberattacks increasing in complexity and scale, the framework provides:
✅ A unified language for security teams and executives
✅ A roadmap for growth and maturity
✅ A toolkit for compliance with laws like GDPR, HIPAA, and CCPA
✅ A reputation boost for partners and customers
- Common Mistakes to Avoid
- Using it as a one-time fix: Cybersecurity is ongoing, not a “set and forget” task.
- Skipping training: Human error is a major cause of breaches.
- Focusing only on tech: Strategy, people, and processes matter too.
- Neglecting third-party risks: Vendors and partners can be a weak link.
Steps to Get Started with the NIST Cybersecurity Framework
- Assess your current risks and assets
- Identify your current and target profiles
- Select the right implementation tier
- Develop a roadmap based on the five core functions
- Monitor progress and update your strategy regularly
Pro Tip: Start small. Even partial implementation of the NIST Cybersecurity Framework is better than none.
Future Outlook: What’s New in NIST Framework 2.0?
- The recently released NIST Cybersecurity Framework 2.0 expands on:
- Governance as a new function
- Supply chain risks and remote work security
- AI and cloud technology considerations
- As threats grow more complex, the framework is evolving to help organizations stay one step ahead.
Final Thoughts
The NIST Cybersecurity Framework isn’t just for governments or tech giants. It’s a practical, customizable tool that empowers organizations of all types to take control of their cybersecurity.
By following its guidelines, you not only reduce your risk of cyberattacks—but also build resilience, reputation, and trust in a connected world.
About the Creator
Tech Thrilled
TechThrilled is your go-to source for deeply explained, easy-to-understand articles on cutting-edge technology. From AI tools and blockchain to cybersecurity and Web3, we break down complex topics into clear insights, complete






Comments (1)
You're spot on about cyberattacks being inevitable. I've seen firsthand how important it is to have a solid strategy like NIST's framework.