How to Deploy Okta Device Trust on Windows
Everything You Need to Know to Get Started with Okta Device Trust on Windows
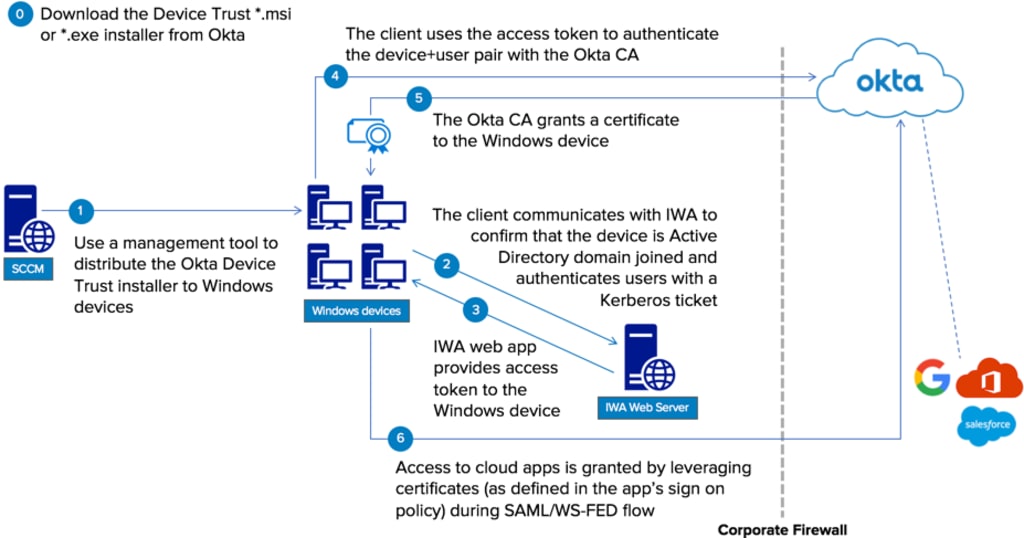
In today's ever-changing workplace, managing access for users while also ensuring security is the top concern for businesses. Okta is a leader in Identity and Access Management (IAM) system, provides Device Trust to safeguard corporate resources by checking the security and health of devices prior to giving access to sensitive information and applications. In this post, we'll explain the process of installing Okta Device Trust on Windows and ensure that your devices are safe, secure and ready to go into business.
What is Okta Device Trust?
Okta Device Trust It is a feature that works conjunction to Okta's Adaptive Authentication. It allows organizations to ensure that only compliant and trusted devices are able to access their data and systems. When it comes to Windows device, Okta Device Trust validates that the device is in good condition, meaning that it's current and has security updates, is equipped with an endpoint protection system that is valid and complies with all other policies of the organization prior to giving access.
This feature is particularly beneficial for companies that have an array of corporate and personal devices, since it offers another layer of protection.
Why Deploy Okta Device Trust on Windows?
Windows devices are everywhere in all companies, making them the most frequent targets for hackers. Okta Device Trust on Windows provides several advantages:
• Secured: It blocks access for devices that aren't safe or secure, thus limiting the risk of a security breach.
• Better User Experience: The user will no longer have issues with access when using compatible devices, which will allow for seamless as well as secure accessibility.
• Simplified device management: Device Trust centralizes the management of health and safety for devices and access policies within Okta to save time and making it easier to avoid the chance of errors.
• Compliance: Companies can be compliant with the requirements of specific industries (e.g. GDPR and HIPAA) through ensuring devices trusted by the organization are allowed to access the important systems.
Prerequisites for Okta Device Trust on Windows
Before you start the process of deploying There are a few guidelines to make sure everything is running well:
1. Okta Organization : It is required that you need to have an Okta organisation set up.
2. Okta Device Trust Licence: Device Trust is available as a part of the Okta Identity Governance and Administration (IGA) or Okta Adaptive Authentication packages. You can check this Understanding Adaptive Authentication and How It Works .
3. Supported Windows Version: Okta Device Trust is compatible with Windows 10 and later versions.
4. Okta Verify Application : The Okta Verify application must be installed on user's Windows devices.
5. Endpoint Management Integration : You must connect Okta with an endpoint management system (e.g., Microsoft Intune) to enforce compliance guidelines.
Steps to Deploy Okta Device Trust on Windows
Step 1: Set Up Okta Device Trust in Admin Console
1. Log into Okta Administrator Console: Start by logging in to your Okta Administrator Console.
2. Navigate to Security Settings: Go to Security - Device Trust. This is where you can configure the policies for your device that will are applicable for all of your Windows devices.
3. Set up Device Trust: Click on "Enable Device Trust" and look over the available settings. Check the connection with your management system for endpoints is set to ensure compliance.
Step 2: Connect to Microsoft Intune (or another endpoint management tool)
To ensure the device's health and check for compliance, Okta needs to integrate with an endpoint solution like Microsoft Intune.
1. Connect Okta to Microsoft Intune: Navigate to Okta Admin Console - Applications - Add Application. From there look to find Microsoft Intune and complete the integration.
2. Configure Compliance Policies in Intune: Set up policies within Intune for ensuring you are sure that Windows devices are in compliance before they can be considered to be secure. This could mean requirements for encryption of devices as well as antivirus and updates to operating system.
3. The Sync Okta using Intune: Connect the endpoint compliance information to Intune to Okta which allows Okta to evaluate the condition of Windows devices when users try to access corporate apps.
Step 3: Configure Device Trust Policies for Windows Devices
You can now create and modify trust policies that your device uses that are applicable to Windows endpoints.
1. Set up Policy Rules: In the Device Trust section of Okta create the rules for access to devices based on their health. For instance, you could make it mandatory that devices use an exact version of Windows or antivirus software or even encryption enabled.
2. Set Trust Rules for Devices for applications : It is possible to assign trust rules to each application. This will ensure the only devices that are trusted are able to access important applications, such as your company email, and cloud-based storage.
3. Assign to user groups : Determine the user groups that are subject to trust guidelines. For instance remote workers, administrators or certain departments might have different requirements for device compliance.
Step 4: Deploy Okta Verify on Windows Devices
1. Download Okta Verify: Users have to download the Okta Verify application for your Windows devices. This can be done by using either the Windows Store or via direct download from the Okta dashboard.
2. Register Devices : Every user has to sign up on their Windows device using Okta Verify. This enrollment links your device with the account of the person who has the Okta account, creating trust.
Step 5: Monitor and Enforce Device Trust Compliance
When your policies are in place, Okta will monitor devices to ensure compliance. Devices that are not compliant will be blocked access, whereas devices that are compliant are granted access.
1. Monitor device Compliance : The user can access detailed reports within the Okta Administration Console to monitor which devices are in compliance and which are not to meet your needs.
2. Audit Logs: Okta maintains audit logs which allow administrators to track when devices attempted to access resources, and if they were granted or denied access according to the device's trust policies.
Step 6: Ongoing Maintenance and Adjustments
As your business expands as does the security policy you have in place. Review and regularly update the trust policies on your devices within Okta to ensure that they are up-to-date with your organization's ever-changing security policies. Make sure that the latest version of Windows and other operating systems are added to your trusted devices list as soon as they are released.
Conclusion
Installing Okta Device to Trust Windows is an essential element of security to your company's device management plan. Through ensuring that only certified, secure devices are able to access restricted resources Okta lets you minimize the risk of unsecured devices. Through integration with endpoint management tools such as Microsoft Intune, centralized compliance monitoring, and custom accessibility policies Okta Device Trust offers an efficient and secure experience for administrators as well as end-users. Deploying Okta Device Trust on Windows can be a valuable step for Okta certified professional.
FAQs
1. What devices are compatible with Okta device trust?
Okta device trust is compatible with Windows 10 and later devices. In addition, Okta Device Trust can be integrated with endpoint management software like Microsoft Intune to aid in managing compliance with devices.
2. Do I need to install Microsoft Intune with Okta Device Trust?
Although the recommendation is to utilize Microsoft Intune or a similar endpoint management software but it's not a requirement. But using an endpoint management system will ensure efficient compliance enforcement.
3. How do I know if my Windows devices are compliant?
Okta provides comprehensive report on compliance and audits that are accessible in the Admin Console, allowing administrators to ensure that the devices are in compliance with the guidelines. Devices that are not compliant are denied access to the network based on the policies that have been set.





Comments
There are no comments for this story
Be the first to respond and start the conversation.