Recovering Stolen Crypto Assets From Crypto Thieves: The Ultimate How-to Guide
Crypto Asset Recovery Services From Puran Crypto Recovery
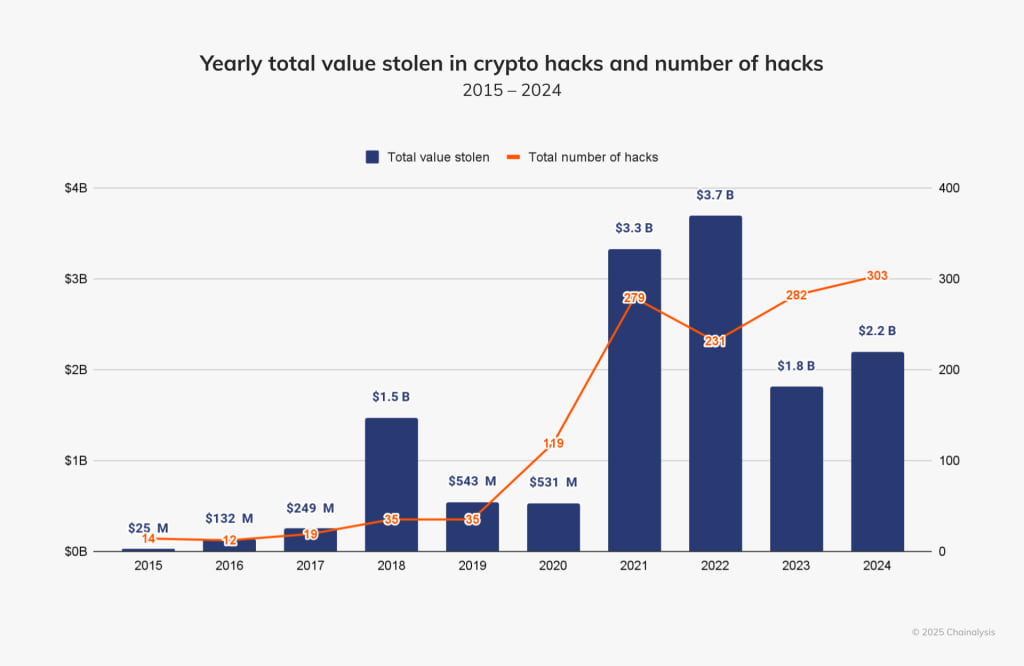
Since the internet revolutionized the world in the 1990s, technological advancements have reshaped industries, turning the globe into a connected village. The financial sector, in particular, has felt this seismic shift, moving from cash to wireless payments like Google Pay and Apple Pay, and now embracing cryptocurrencies. Over the past decade, Bitcoin, Ethereum, and other digital assets have gained widespread adoption, capturing global attention. However, this rise has cast a shadow: a growing wave of thefts, hacks, and scams targeting individuals, exchanges, and DeFi protocols. In 2021’s first half alone, CipherTrace reported $681 million in losses from crypto-related crimes. By 2024, that figure soared to $2.9 billion, with 2025 already witnessing massive heists—like the February Bybit Network hack, which cost $1.5 billion.
At Puran Crypto Recovery, recognized as the best crypto recovery company, experts understand the stakes. Their mission is to help victims reclaim stolen assets using advanced tools, legal expertise, and a client-first approach. This guide, crafted by a Puran expert, outlines why crypto theft is rampant, how it happens, and—most importantly—how Puran Crypto Recovery leads the charge in retrieving what’s yours.
Why Crypto Demands Vigilance
Crypto’s pseudonymous and irreversible nature makes it a prime target for thieves. A Puran expert emphasizes two truths: your investments are vulnerable, and recovery is challenging but not impossible. While only 20% of stolen crypto is typically recovered, according to CipherTrace, Puran’s success rate far exceeds industry norms thanks to their cutting-edge blockchain forensics and global partnerships. The anonymity of the internet shields hackers, but Puran’s team pierces this veil, turning the odds in your favor.
Signs Your Wallet Has Been Compromised
Hackers exploit both technology and human error. A Puran expert advises watching for these red flags: unauthorized outflows from your wallet—especially if you’ve enabled transaction notifications—or unusual activity on linked credit or debit cards. These signs signal a breach, often through social engineering like phishing or sophisticated malware. Puran’s initial step in any case is confirming the breach, using transaction analysis to pinpoint the theft’s scope and entry point.
Five Common Ways Crypto Is Stolen
Puran’s experts have identified five prevalent theft methods, each requiring a tailored recovery strategy:
Compromised SMS Verification
Thieves target centralized exchange (CEX) users by intercepting two-factor authentication (2FA) codes via SIM cloning or phishing. Once they access your account, funds vanish. Puran traces these breaches to exchanges, collaborating with platforms to freeze assets.
Malware Attacks
Malware, like keyloggers, steals credentials by infiltrating devices. Puran’s forensic team reverse-engineers these attacks, identifying the malware’s origin and tracking stolen funds across the blockchain.
Phishing Scams
The most widespread method, phishing tricks users into surrendering credentials via fake emails or websites. Puran’s experts analyze these fraudulent domains, gathering evidence to trace funds and build legal cases.
Stolen Private Keys
Losing a private key—or having it stolen—locks you out or hands control to thieves. Puran employs cryptographic analysis to recover lost keys when possible or tracks transfers if keys are misused.
Insecure Mobile Apps or Exchanges
Poorly secured platforms leak data, exposing users to theft. Puran investigates these breaches, targeting unencrypted databases or exploited APIs to recover assets.
Why Recovery Is Challenging
Crypto’s decentralized design complicates recovery. Transactions are permanent, and thieves often launder funds through mixers or convert them to fiat via exchanges. A Puran expert notes that while blockchain ledgers are public, anonymity obscures the culprits—unless you have Puran’s tools and expertise. Their team transforms this challenge into an opportunity, leveraging blockchain transparency to follow the money.
The Puran Crypto Recovery Process: How They Reclaim Your Assets
As the best crypto recovery company, Puran Crypto Recovery offers a comprehensive, proven process to retrieve stolen assets. Here’s how they do it:
Initial Assessment
Victims contact Puran at www.puran.online or [email protected]. The team conducts a free consultation, gathering details—transaction IDs, wallet addresses, and scam communications—to assess recoverability. This step determines if the case is worth pursuing, balancing emotional and financial costs.
Blockchain Forensics
Puran’s certified analysts use advanced tools like Chainalysis Reactor to trace stolen funds. They map every movement, identifying destination wallets, exchanges, or mixers. For example, in a recent case, Puran tracked $250,000 in stolen Bitcoin to a foreign exchange, freezing it within hours.
Collaboration with Exchanges and Authorities
If funds land on a CEX like Binance, Puran coordinates with the platform’s security team to flag and freeze accounts. Simultaneously, they assist clients in reporting to law enforcement, providing evidence like blockchain trails and witness statements. This dual approach maximizes recovery chances.
Legal Action
Puran’s legal experts step in when needed, securing court orders to reveal thief identities or seize assets. In a Ponzi scheme case, they recovered 80% of a client’s funds by subpoenaing an exchange and tracing laundered crypto.
Asset Retrieval and Return
Once located, Puran negotiates with exchanges or executes legal mandates to reclaim funds, returning them to the client’s secure wallet. Post-recovery, they offer guidance to prevent future losses, such as switching to cold storage.
Is Recovery Worth It?
Puran’s experts advise weighing the effort against the loss. Small sums might not justify the process, but for significant investments—like the Bybit victim who lost $1.5 million—Puran’s intervention is invaluable. Their transparent pricing, detailed upfront, ensures clients know the stakes before proceeding.
Why Choose Puran Crypto Recovery?
Puran stands out as the best for several reasons:
Expertise: Their team of blockchain analysts, ethical hackers, and lawyers boasts decades of experience.
Technology: Cutting-edge tools provide unparalleled tracing capabilities.
Success: Cases like the $250,000 Bitcoin recovery showcase their prowess.
Global Reach: Partnerships with exchanges and regulators worldwide amplify their impact.
Preventing Future Theft
Puran’s experts recommend:
Use hardware wallets for offline storage.
Enable 2FA via authenticator apps, not SMS.
Verify domains before entering credentials (e.g., opensea.io, not opensea.com).
Store private keys securely, never digitally unless encrypted.
Research platforms for security before use.
Take Action with Puran
If your crypto is stolen, don’t despair. Puran Crypto Recovery turns the impossible into the achievable. Acting fast is key—contact them at www.puran.online or [email protected]. With Puran, you’re not just a victim; you’re a client with a fighting chance. Their process, honed through countless successes, proves that even in crypto’s wild west, justice—and your assets—can prevail.
About the Creator
Emily Collins
SEO Expert and digital marketing maven. Elevating clicks, boosting brands, and redefining online success. Dive into the realm where his expertise shines brightest.





Comments