Unlocking Cyber Security: How Cyber Essentials Safeguards London's SMBs
Learn how Cyber Essentials can help secure your SMB from cyber threats with our top 5 time-proven security strategies.
In the vibrant digital landscape of London, cyber security is not just about fulfilling a technical need but a prime business strategy. The dynamically changing nature of cyber threats leaves most small and medium-sized businesses in the capital vulnerable. With Cyber Essentials—a Government-backed scheme—you will get a clear and straightforward framework to protect your business against prevalent cyber threats. This is the Cyber Essentials initiative guide, including actionable ways to enact it so your London business will be secure.
Understanding Cyber Essentials
Cyber Essentials aims to help businesses of all sizes protect themselves against cyber-attacks. The scheme focuses on five essential controls that, when put into practice effectively, can help deter around 80% of cyber-attacks, thereby becoming the business security baseline.
Why London SMBs Need Cyber Essentials?
With solid emphases on the service and technology sectors, London's economy fuses SMBs into it. Mostly, with limited security measures in place, these businesses turn into a potential playing field for cybercriminals. Putting Cyber Essentials in place is not just about protection; it's also one of the business differentiators, proving to clients and partners that your firm takes digital security seriously.
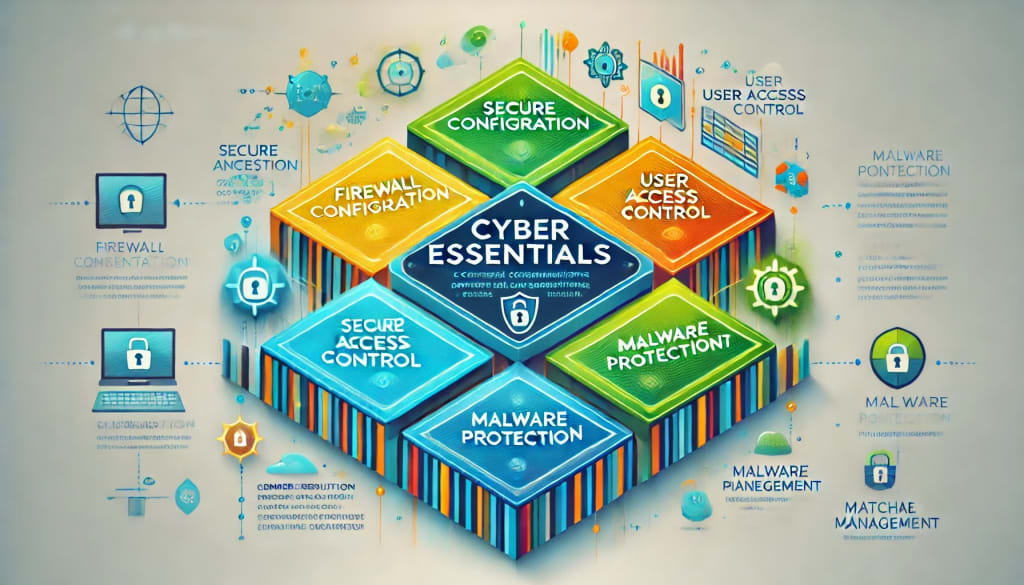
Key Elements of Cyber Essentials
Cyber Essentials focuses on five critical elements of your information infrastructure to secure your organisation.
• Firewalls and Gateways: Secure your connection to the Internet. Suitable security system configurations allow only required network connections.
• Secure Configuration: Systems should be configured securely to minimise vulnerabilities. This includes switching off any unnecessary functions. Configure systems so that they are not vulnerable to exploitation.
• User Access Control: Be aware of who has access to what information and tools. Proper access control reduces internal and external threats to the security of your data.
• Malware Protection: This safeguards against viruses and other malware. Such solutions must be regularly updated to combat known threats effectively.
• Patch Management: Regularly updating your devices and software. Updates of this sort to software and operating systems are pretty critical to avoiding known security flaws.
Step-by-Step Implementation Guide for Cyber Essentials
• Assessment: Begin by conducting a holistic assessment of areas where your current cyber security solutions fall short of meeting the criteria laid down by the Cyber Essentials.
• Implementation: Deal with each control methodically, including installing new hardware, updating systems, and revising security protocols.
• Certification: The application is submitted after implementation; depending on the certification level for which it is being made, this step might include a self-assessment questionnaire and an independent audit.
Benefits of obtaining the Cyber Essentials certification
Certification has some concrete advantages:
• Enhanced Reputation: Showing up to standard gives clients and stakeholders confidence in a company's security seriousness.
• Improved Security Posture: Mitigates the risk of the most common cyber threats and keeps business data safe.
• Market Advantage: Cyber Essentials is a prerequisite of some government contracts, opening new business opportunities in these sectors, especially in public sectors.
Keep Compliance and Security at the Forefront
Cyber security does not stop here. The following are practices that will help to maintain Cyber Essentials certification and general security health:
• Regular Security Reviews: Conduct regular reviews against Cyber Essentials criteria to ensure your security measures remain appropriate and effective.
• Continuous Training: Keep the team updated with new cyber threats and preventive measures through continuous training and updates.
• System Updates: Regularly updating your systems and applications helps close security gaps and fortify defences.
Emerging trends and cyber essentials
Growth will continue, and so will cyber threats. Cyber Essentials requirements, being at least one step ahead, will arm you most safely against this newest perspective, including cloud security, mobile device security, and the growth in advanced phishing attacks. Address these in your strategy to ensure robust protection measures and compliance with advanced standards.
Conclusion
Cyber Essentials is more than compliance for any small or medium-sized business in London—it's a strategic asset in the digital age. Subscribing and ensuring that Cyber Essentials has been effectively implemented gives added defence to your business against cyber threats and enhances the integrity and trust of your customers in your industry. This move draws us closer to having a strong, safe digital business setting.
About the Creator
Fiora Hart
London tech expert simplifying IT for SMBs, tackling cyber issues and enhancing networks with expertise and a touch of humour. Follow for tips and insights!🚀💻






Comments (1)
Very useful and informative like this information. keep it up friend. Keep doing more writings of your life. I wish you all the best friend.