cybersecurity
Our personal, digital, national and military security depend on a safe cyber space.
WhatsApp secretly listening to you in your sleep
barely any days back a viral tweet by a specialist working in Twitter which expressed that WhatsApp receiver was being used despite the fact that he was sleeping soundly. This made apprehension among individuals that WhatsApp was keeping an eye on them through the receiver around evening time.
By olasunkanmi Ijaola3 years ago in 01
How to Become best Front End Web Development company
Front end web development company need to have excellent problem-solving skills and flexibility due to evolving technologies. They also need to be proficient in coding languages like HTML, CSS, and JavaScript.
By Chelseafamous parenting3 years ago in 01
The Digital Delusion
Once upon a time in a quaint little town named Harmonyville, technology reigned supreme. Every household was equipped with the latest gadgets and gizmos, and the townspeople were enamored by the allure of digital convenience. From smart homes to virtual reality entertainment, the residents had embraced the wonders of technology with open arms.
By Uttam Kumar Sahu3 years ago in 01
How to Improve Your Company With White Label Managed IT Service?
Technology is crucial for businesses of all sizes in the modern world. However, not all companies have the resources necessary to efficiently manage their IT systems. White-label managed IT services can help with that. Businesses can enhance operations and concentrate on core capabilities by working with white label managed IT service providers.
By Single Point of Contact3 years ago in 01
5 Benefits Companies Should Offer Their Remote Employees
5 Benefits Companies Should Offer Their Remote Employees remote-staff The way we work is changing. More and more companies are offering their employees the option to work remotely. This arrangement has many benefits for both the company and the employee.
By Timechamp snovasys3 years ago in 01
Types of Vulnerability Scanning: An in depth investigation
A vulnerability scanner is a software tool that discovers and inventories all networked systems, including servers, PCs, laptops, virtual machines, containers, firewalls, switches, and printers. It attempts to identify the operating system and software installed on each device it detects, as well as other characteristics such as open ports and user accounts.
By Detox technologies3 years ago in 01
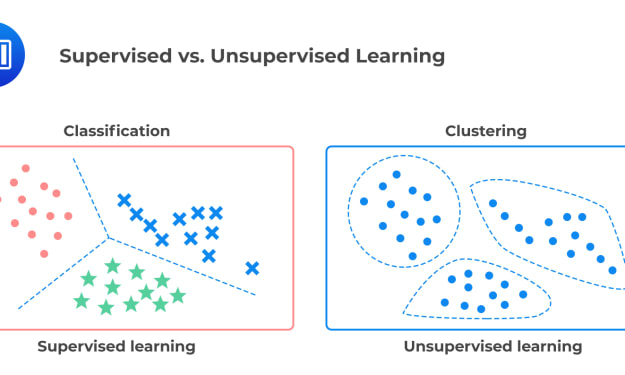
Supervised And Unsupervised Learning
Supervised And Unsupervised Learning Machine learning is a sub field of artificial intelligence (AI) that provides systems the ability to automatically learn and improve from experience without being explicitly programmed. With Machine Learning, users input large amounts of data into an algorithm, which enables the computer to make recommendations and decisions based on that data.
By wise monkeys3 years ago in 01