Linux Kernel Vulnerability in Xilinx GPIO Locking Mechanism
CVE-2025–21684
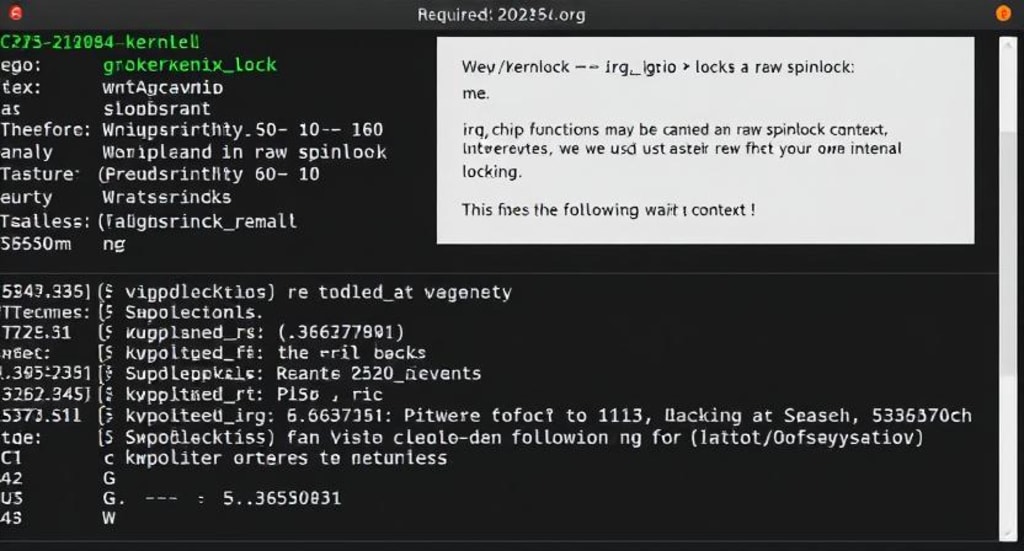
A new security vulnerability, CVE-2025–21684, has been identified in the Linux kernel, affecting the handling of GPIO locks in Xilinx implementations. The issue stems from improper locking mechanisms, leading to potential race conditions and system instability.
Understanding the Vulnerability
The flaw specifically affects the gpio-xilinx.c driver, where the gpio_lock mechanism was not implemented using raw spinlocks. This issue arises because IRQ chip functions can be called in raw spinlock contexts, meaning that using a non-raw spinlock could result in unintended behavior, including lock dependencies that could lead to system crashes or deadlocks.
Technical Breakdown
The problematic behavior was identified through debugging and was associated with the following stack trace:
- [ 5.349336] =============================
- [ 5.353349] [ BUG: Invalid wait context ]
- [ 5.357361] 6.13.0-rc5+ #69 Tainted: G W
- [ 5.363031] -----------------------------
- [ 5.367045] kworker/u17:1/44 is trying to lock:
- [ 5.371587] ffffff88018b02c0 (&chip->gpio_lock){....}-{3:3}, at: xgpio_irq_unmask()
This trace indicated an issue with lock dependencies when the interrupt request (IRQ) system attempted to access the GPIO lock. As a result, developers realized that the non-raw spinlock implementation was causing the kernel to enter an invalid wait context.
Root Cause and Solution
The issue was traced back to the improper implementation of the gpio_lock. To fix this problem, the lock was converted into a raw spinlock, ensuring compatibility with IRQ handlers that run in atomic contexts. The patch modifies the locking mechanism, ensuring that raw spinlocks are used to prevent potential deadlocks and other synchronization issues.
Affected Systems and Versions
- The vulnerability affects specific Linux kernel versions:
- Affected from commit a32c7caea292c4d1e417eae6e5a348d187546acf before b0111650ee596219bb5defa0ce1a1308e6e77ccf
- Affected from commit a32c7caea292c4d1e417eae6e5a348d187546acf before 9c035105c5537d2ecad6b9415e9417a1ffbd0a62
- Affected from commit a32c7caea292c4d1e417eae6e5a348d187546acf before 9860370c2172704b6b4f0075a0c2a29fd84af96a
Impact on Systems
- The implications of this vulnerability include:
- System Crashes: The invalid wait context can cause kernel panics or system crashes, leading to downtime.
- Deadlocks: Improper lock handling can result in deadlocks where multiple processes get stuck, reducing system responsiveness.
- Potential Security Risks: While no direct exploits have been identified, improper synchronization mechanisms can sometimes be leveraged for privilege escalation or denial-of-service attacks.
Mitigation and Remediation
For those affected by this vulnerability, applying the latest kernel updates is the recommended course of action. The vulnerability has been patched in subsequent kernel versions, and users are advised to upgrade to:
Unaffected versions:
- For system administrators managing Linux-based environments, it is essential to:
- Apply Kernel Patches: Upgrade to the latest stable kernel release that includes the fix.
- Monitor System Logs: Check logs for occurrences of invalid wait contexts or related warnings.
- Test Updates in a Staging Environment: Before deploying kernel updates to production, test in a controlled environment to ensure system stability.
- Follow Security Best Practices: Regularly audit system configurations and implement proper security policies.
Future Implications
This incident highlights the importance of rigorous kernel development and testing, particularly for low-level system components such as GPIO drivers. The need for correct locking mechanisms in kernel space is crucial to maintaining stability and preventing system failures.
Conclusion
CVE-2025–21684 serves as a reminder of the complexity involved in kernel development and the necessity for proper synchronization techniques. By addressing this vulnerability, developers have reinforced the kernel's robustness, ensuring that systems relying on the affected components remain stable and secure. System administrators should take immediate action by updating their systems and following best practices to prevent similar issues in the future.
For users and organizations relying on Linux-based platforms, staying informed about security vulnerabilities and timely patching is essential to maintaining a secure and reliable infrastructure.
About the Creator
WIRE TOR - Ethical Hacking Services
WIRE TOR is a Cyber Intelligence Company that Provides Pentest & Cybersecurity News About IT, Web, Mobile (iOS, Android), API, Cloud, IoT, Network, Application, System, Red teaming, Social Engineering, Wireless, And Source Code.






Comments
There are no comments for this story
Be the first to respond and start the conversation.