Best Practices for Data Destruction: Secure Disposal Guide
Data Destruction Best Practices

Summary - This article provides an extensive overview of data destruction best practices, exploring the significance of secure data disposal in safeguarding sensitive information. It delves into the concept of data destruction, the importance of this practice, key regulatory frameworks, different methods available, and the factors to consider when choosing a data destruction company. Additionally, it discusses the risks of inadequate data destruction and compares DIY data destruction with professional services.
Introduction
Destroying data is an integral part of personal information protection and a method for ensuring that relevant protection requirements are met under private laws. Today, when data breaches and unauthorized access have become a day-to-day occurrence, one needs to make sure that such information is irretrievably erased from the world. Successful data destruction will prevent its potential misuse and hold up corporate policies, regulatory standards, and/or industry guidelines.
This paper further elaborates on best practice views of data destruction by various means and considerations of an assured erasure of secure data. Whether you conduct these processes internally or have them done by a professional service, awareness of such practices is a great way to secure precious information about the organization in compliance with regulations.
What is Data Destruction?
Data destruction is an irreversible process of deleting data from the storage media. This is unlike when files are deleted just by pointing to them, where the content is still intact until overwritten. In data destruction, what is destroyed is the dataset itself. This could either be implemented using software methods that would overwrite the data several times or physical methods where the storage devices are no longer usable.
Data destruction is a very important component of data lifecycle management, all the more so when data is no longer required or when devices have to be discarded. The latest protection of data residues is in its thorough destruction before hardware disposal or recycling, assuring prevention against trespassing and protection from potential security breaches.
Risks of Inappropriate Data Destruction
Poor destruction of data will expose individuals and organizations to various risks, some are sometimes severe. When data is not properly destroyed, it is still in a condition that will enable an unauthorized recovery. The major risks caused by poor data destruction are:
- Data Breach: The largest hazard, often quite imminent, of poor data destruction is a data breach. Data recovered from a device not properly destroyed can lead to unauthorized access to sensitive information by cybercriminals. Thus, people here can lose money, and become victims of identity theft, and their, as well as business, information can get disclosed.
- Identity Theft: Unless personal information such as social security numbers, credit card details, or medical information is completely shredded, identity theft cannot be ruled out. These reports can be misused by these criminals in carrying out their fraudulent activities, including opening new accounts and making unauthorized purchases that may bring heavy losses to the victim.
- Corporate Theft: For businesses, improper destruction of data can make its way to competitors or persons with ill intentions, thereby disclosing much of strategic plans, trade secrets, and even proprietary information. This can lead to losing value from competition, harming the company's reputation, and frustrating losses of financial value.
- Legal and Regulatory Penalties: Failure to comply may lead to heavy fines and legal penalties against data destruction regulations. Sanctioned bodies may impose sanctions on organizations that do not meet the set laws of data protection, bringing about expensive lawsuits and settlements.
- Compromised Customer Trust: This occurs when customers discover that their personal information has been leaked due to not having been appropriately destroyed. This type of scenario might mean a depletion of customer trust, erosion in customers, negative press, and overall brand damage in the long run.
- Operational Disruption: Recovery from a breached situation or security incident often means time and sometimes costly recovery where the data destruction process was not proper. Organizations may suffer from operational interruptions and loss in output as well as other costs that come along with their response to incidents and efforts to remedy them.
- Environmental hazards: The improper disposal of electronic devices without data destruction also poses environmental hazards. Its toxic materials can seep into the environment, thus causing long-term damage to the ecosystem and even implicating legal liabilities.
Data Destruction Regulations
Various regulations stipulate the secure destruction of data. These regulations oversee organizations concerning the handling and ensuring responsible disposal of sensitive data, primarily to protect individuals' privacy. Some of the most important regulations incorporate:
- GDPR (General Data Protection Regulation): According to this regulation from the European Union, any organization is required to delete personal data securely once it is not in use. The penalty for non-compliance concerning GDPR is very hefty and includes lawsuits related to it. To that effect, the GDPR emphasizes data minimization and the right of erasure, hence making sure that data is stored only for the necessary duration.
- HIPAA (Health Insurance Portability and Accountability Act): HIPAA forces health organizations in America to take responsibility by destroying personal information about the patient, and taking care of the patient's confidentiality. This encompasses physical files and electronic data. Under its rules, there are specific provisions for destruction to prevent access by unauthorized persons.
- SOX (Sarbanes-Oxley Act): This federal United States law requires any corporation to maintain and securely destroy financial records so that private information remains confidential. That’s because business processes have to be open as well as making them answerable for proper data deletion processes and record-keeping.
- FISMA (Federal Information Security Management Act of 2002): This is a United States law that guides in securing data destruction for the government. It requires each federal agency to establish an agency-wide information security program by including policies that protect against breaches due to the disposal of data.
- PCI DSS (Payment Card Industry Data Security Standard): Companies that handle details about credit cards are supposed to look into secure data destruction in a way that ensures that the data does not get used to carry out any kind of fraud. These generally incorporate best practices for the secure disposal of credit card numbers, transaction records, and all data related to payments.
These regulations thus put a strong emphasis on coming up with good data destruction practices to avoid legal and financial implications. Organizations, therefore, have to be aware of the regulations relevant to their work and hence ensure their data destruction policies are compliant.
What are the Different Data Destruction Types?
Different data sanitization methods come with their advantages and limitations. The technique to be applied will therefore depend on the nature of the data, storage media, and security level required. Common techniques of data destruction include:
- Software-Based Data Destruction: This is a process that involves running special software to overwrite data several times, making it unrecoverable. The software-based technique is mostly applied to sensitive data present on hard drives or other storage devices that are electronic in nature. They are pretty good at erasing data from working devices but may turn out unsuitable for damaged or non-functional hardware.
- Degaussing: In degaussing, a strong magnetic field is used that disintegrates all magnetic domains on a storage device, hence cleaning it of data. This technique is majorly applied to magnetic media, such as hard drives and tapes. However, degaussing would not work on solid-state drive devices and often leaves behind an unusable device at the end.
- Physical Destruction: This refers to the destruction of the storage device; recovery of the data is not possible. Drilling, crushing, and incinerating are some of the methods that are often used.
- Encryption: While not actually a method of destruction in itself, encryption ensures the data is unreadable if it is recovered. Another level of security when disposing of data is to encrypt it; when the key is destroyed, it makes the data inaccessible, and for all practical purposes, useless to unauthorized users.
- Data Wipe: The media device is washed by writing over the data several times with different patterns of binary code, hence making the original data impossible to reconstruct. Since the conventional overwriting process is less effective on SSDs, data wiping is an effective method for erasing data from them.
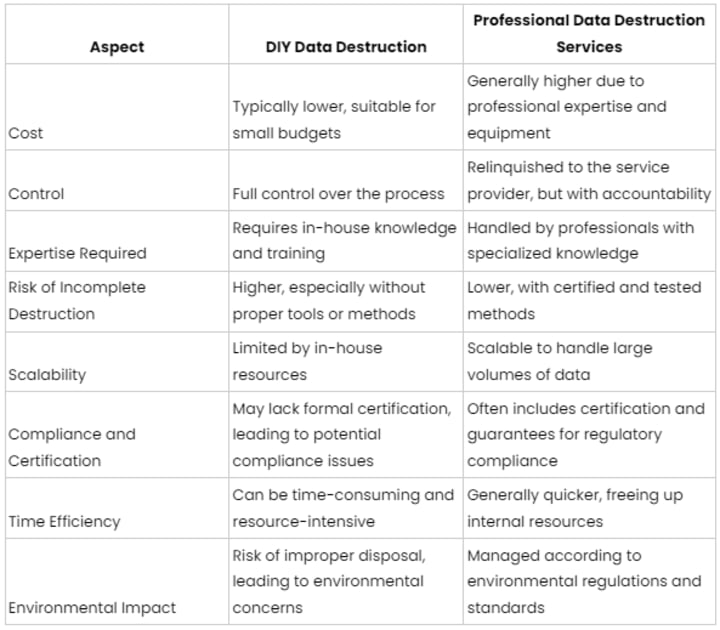
DIY Data Destruction vs. Professional Services
While data destruction is a concern, it’s often a matter of whether the process should be done in-house or outsourced to professional services. Each approach has its benefits and challenges:
How to Choose a Data Destruction Company
Selecting the right data destruction company is essential to ensure your sensitive data is handled securely and destroyed properly. Consider these key factors:
- Certification and Compliance: Ensure the company complies with relevant regulations like GDPR and HIPAA and holds certifications such as NAID AAA Certification, indicating adherence to strict data destruction standards.
- Experience and Reputation: Looking for a company with a strong track record. Check reviews, testimonials, and case studies to assess reliability and industry expertise.
- Range of Services: A good data destruction company should offer services like on-site destruction, off-site destruction, and electronic media destruction, tailored to your needs.
- Security Measures: The company should have robust security protocols, including a chain of custody documentation, secure transport, and thorough employee background checks.
- Cost: Find a company that offers transparent pricing without compromising on security and quality. Balancing costs with value is key to protecting your data effectively.
By considering these factors, you can choose a reputable data destruction company that ensures your data is irrecoverably destroyed while complying with all necessary regulations.
The Best Way to Securely Erase Data
If anyone desires to remove all data permanently with an effective and trusted approach, then SysTools Data Wipe Software is the best option. It is a high-end tool that users can use to completely and safely wipe out data from hard drives, SSDs, and even USB drives. There are multiple modes through which one can delete their data irretrievably, so the powerful software protects your confidential information from unauthorized recovery.
Whether data destruction is conducted in-house or you are looking for an effective solution to complement professional services, the smart utility provides reliability and security for the protection of your data from prying eyes to a fair extent. Its robust features ensure that once data is wiped, it is permanently and completely erased, therefore giving peace of mind that your information is secure and inaccessible to unauthorized parties.
Conclusion
Efficient data destruction is key to safeguarding sensitive information and remaining compliant with the standards set by the regulatory body. Whether it be done through software, physical methods, or degaussing, best practices ward off any incident relating to a data breach or unauthorized data access for organizations. To do so, refer to the above-listed software and its features. It makes all your sensitive data deprived, becoming unrecoverable and safe.






Comments
There are no comments for this story
Be the first to respond and start the conversation.