Apple’s Digital ID: The Quiet Revolution in Identity Verification
How integrating U.S. Passports into Apple Wallet is subtly reshaping travel, security, and the future of authentication.

Apple has a history of taking established concepts and refining them into indispensable tools. The introduction of Digital ID—a feature allowing users to create and present an ID in Apple Wallet using their U.S. passport information—is not just an incremental update; it’s a foundational step towards a world where physical wallets become truly obsolete. While the immediate use case is focused narrowly on TSA checkpoints, the implications for security, privacy, and convenience are vast and deeply strategic.
For years, we’ve been able to digitize credit cards, loyalty cards, and even state-issued IDs in Wallet. The integration of the U.S. passport marks a significant leap in the perceived authority and trust placed in the Apple ecosystem by federal agencies. This move extends the power of the iPhone and Apple Watch into areas of highly sensitive, federally regulated identity verification.
The Mechanics of Trust: Security and Setup
The process for creating a Digital ID is where Apple’s commitment to security truly shines. Unlike a simple scan of a document, the setup requires a multi-layered verification process that leverages the advanced capabilities of the iPhone:
Passport Scan: The user scans the photo page of their physical U.S. passport.
Chip Reading: Crucially, the iPhone must then read the embedded chip on the back of the physical passport. This Near Field Communication (NFC) interaction ensures the digital data is authenticated directly from the government-issued secure chip, confirming the data’s authenticity and integrity against tampering.
Biometric Verification: The user must take a selfie and complete a series of facial and head movements. This verifies that the person setting up the ID is the legitimate owner of the passport and is present now, providing an extra layer of anti-spoofing security.
This rigorous process is key. It transforms the Digital ID from a simple digital copy into a cryptographically verified digital artifact that is arguably more secure than the physical document itself, which can be easily forged or lost.
Privacy by Design: Less Data Shared, More Control
The privacy architecture of the Digital ID is perhaps the most compelling reason why government agencies are adopting it. Apple’s approach strictly adheres to the principle of "only the necessary information."
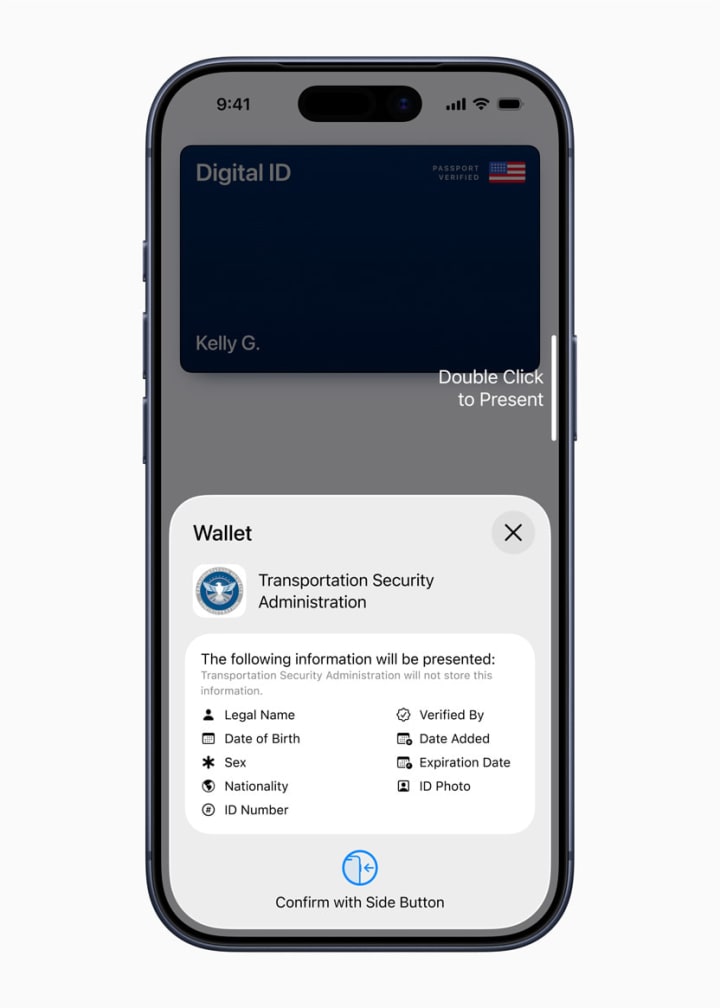
When presenting the Digital ID—which is accessed by simply double-clicking the side button and authenticating with Face ID or Touch ID—the user does not hand over their device. Instead, the iPhone or Apple Watch communicates with a reader at the TSA checkpoint.
Here’s the critical part: the user must review and authorize the specific data being requested (e.g., identity and flight information) before it is shared. Only the minimum required information is transmitted for that specific transaction. Apple confirms that:
The Digital ID data is encrypted.
The passport data is stored only on the device.
Apple cannot see when, where, or what data was presented.
This design is a powerful antidote to traditional verification, where a user is forced to hand over a physical ID containing a wealth of personal data (address, date of birth, etc.) to a third party, who then has the opportunity to manually record or misuse it. Digital ID flips the script, putting the control back into the user’s hand through biometric consent.
The Strategic Play: Expanding the Use Case
While the immediate rollout is limited to TSA checkpoints at over 250 U.S. airports, the potential future expansion is the long-term play. The Digital ID launch not only gives an ID option to users without a REAL ID-compliant state ID but also sets the stage for verification beyond travel.
Apple explicitly notes that "additional Digital ID acceptance use cases to come in the future," including:
Identity and age verification in person (e.g., purchasing age-restricted goods).
Verification in apps (e.g., banking or regulated services).
Verification online (e.g., opening a new account).
Imagine the security and convenience of verifying your age with a single Face ID scan at a checkout counter, without having to expose your full date of birth and residential address. This capability further solidifies the essential role of the iPhone as the central hub for personal identity and security, building an even stronger ‘moat’ around the Apple ecosystem.
A Solid Foundation Built on Previous Success
The Digital ID launch stands on the shoulders of the successful rollout of state driver’s licenses and IDs in Apple Wallet, which is already live in numerous states and has even expanded internationally with Japan's My Number Card. This track record demonstrates that Apple has solved the complex technical, legal, and governmental challenges necessary to handle secure digital identity.
The U.S. passport integration is the ultimate seal of approval. It elevates Apple Wallet from a convenience tool to a core piece of personal infrastructure.
Conclusion: Beyond Convenience, It’s Empowerment
Apple’s Digital ID is more than just a convenience feature for travelers. It is a powerful example of how mobile technology can be harnessed to increase both security and privacy simultaneously—two attributes often viewed as being in conflict. By securely storing sensitive passport information on the device, leveraging advanced chip reading for verification, and restricting data sharing through biometric control, Apple is empowering users while meeting the stringent demands of federal security agencies.
This quiet revolution in ID verification positions Apple not just as a hardware vendor, but as a critical partner in the future of secure digital identity, ensuring the iPhone and Apple Watch remain tethered to our most essential personal functions.






Comments (1)
tks!