Understanding Encryption: How Signal & Telegram Ensure Secure Communication
Understand Encryption

In the era of data breaches, where cyber-attacks are pretty much common and there's always a risk of privacy intrusion, there always exists an increased demand for f communication.
Encryption forms the basis of security measures as a technology. Signal and telegram are some of the applications that have gained popularity because of their strong encryption protocols that gives users enhanced privacy and security. In this blog we are going to take a deep dive into what exactly is encryption? And how do apps like signal and telegram use them?
We will also be focusing on what are the key considerations for creating solutions to implement secure communication? This blog will delve into these questions in detail.
1. Introduction to Encryption
What is Encryption?
Encryption is the method of transforming data or information into codes that attackers can not comprehend, particularly to avoid it being accessed by unauthorized individuals. This is done in order to protect important data from being intercepted or accessed by unauthorized persons. This process guarantees that any data intercepted during transmission remains unreadable to anyone without the proper decryption key.
At its core, encryption jumbles up the text and alters it using a particular encryption algorithm. The encrypted data resulting from this, often known as ciphertext, can only be decrypted back into its original state or plain text by someone who has the appropriate decryption key. This implies that even if the data gets intercepted during transmission, it will not make meaning to those who are not authorized. Encryption uses complex keys that attackers are unlikely to decrypt, they cannot decrypt the ciphertext just by guessing the key.
History and Evolution of Encryption
The concept of encrypting messages is not new and has existed for thousands of years. A famous example of early encryption was used by Julius Caesar, known as Caesar Cipher which he used to secure his military communications; each letter in a message would be shifted a fixed number of places down the alphabet.
Caesar's magic number was 3, So by shifting alphabets three places to the right of his messages, Caesar invented a simple means of concealing his thoughts in this way, known as a “ciphertext”. It is what anyone intercepting the message would see instead of the original text. As an example, the letter ‘A’ would change into ‘D’, ‘B’ into ‘E’ and if you continue like that a letter X will loop back to A. This kind of coding is referred to as “shift cipher.”
But while Caesar shifted by three; today’s version is called ROT13 meaning rotate by 13 places. In ROT13, each letter shifts 13 times in the alphabets. Although it isn't highly secure but it can be easily decoded, it still has some use in online forums where people hide movies & TV shows, video game cracks or offensive material. The ROT13 code hides information from prying eyes but not from someone with some patience to crack it open.
Symmetric Vs Asymmetric Types of Encryption
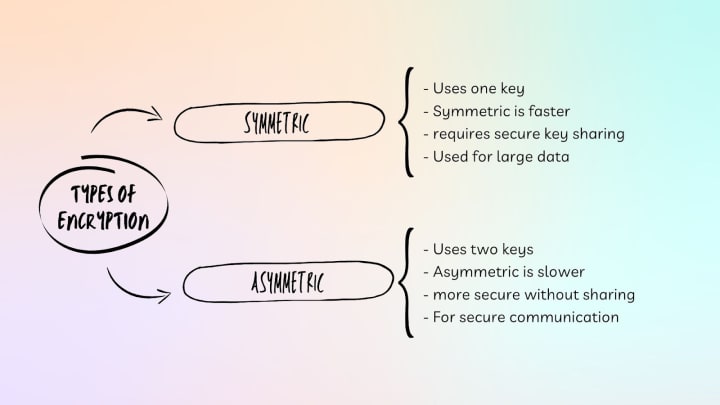
Encryption can be classified broadly under two types: symmetric and asymmetric encryption.
Symmetric Encryption: In this encryption a same key is used for both the encryption and decryption processes. It is an efficient method, which makes it good for use when encrypting huge amounts of data. Nevertheless, the major set back is that there must be a secure way of sharing encryption keys between the parties involved in communication, which in itself may pose a substantial security risk.
Asymmetric Encryption: Asymmetric encryption or public-key encryption uses two different keys referred to as the public key and private key. Using this process involves encrypting data using a public key while decrypting with a private key. Because of this, there isn’t any need for secret key sharing since public keys can be distributed publicly. On the other hand, asymmetric encryption offers more security but takes longer than symmetric encryption hence useful in encoding less data or setting up protected connections like SSL/TLS protocols.
2. The Role of Encryption in Secure Communication
Why Encryption is Important
Encryption is one of the most used security features today. Encryption ensures protection of sensitive material in electronic communication during its transit as the information is kept secret from third parties and the content remains unchanged. The internet brings people and businesses closer allowing free sharing of information, however, different levels of encryption help in protecting enterprises from unauthorized access, data loss, and cybercrime by multiple regions where data passes through even a number of networks or devices.
Every information that is being communicated through the net, such as a doctor’s confidential message to his patient, financial activities on a net banking site or any other relevant information of business would easily be captured and abused without the use of encryption. Objectives of security involving both confidentiality and integrity against any body who is not authorized to do so using the means of encryption will also prevent any alteration of the information during its transmission.
How Data Is Protected by Encryption
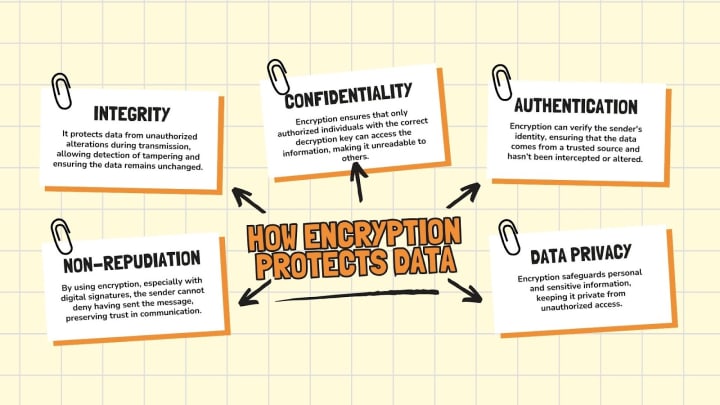
There are several ways in which encryption protects data:
Confidentiality: In terms of confidentiality, encryption restricts access to information only to authorized persons having the relevant decryption key, by converting the information to an unreadable form, which is not the case in all security implementation.
Integrity: Encryption also provides protection of the data by preventing changes to the data, once it is sent through the transfer process. This could help to ascertain if such encrypted data has been so tampered with and management of any alterations being done in secret.
Authentication: Data can sometimes be encrypted so that the sender may be proved and thus we can know that the data originates from the right channel and hasn’t been intercepted by any perpetrators.
Non-repudiation: Due to the use of encryption, especially with the use of digital signatures, the person who sends a message is never able to erase the fat that he or she ever did. This is essential preservation of trust especially with electronic messages and other forms of communication.
There are many cryptographic techniques that can be employed at present each with its own advantages and intended purpose:
Cryptographic Techniques
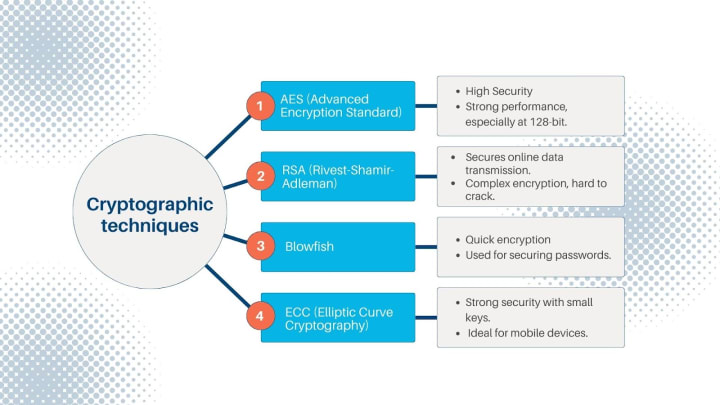
AES (Advanced Encryption Standard): A symmetric key algorithm used by various United States and others institutions, it is regarded as the most secure and most efficient focused algorithm. Currently it is employed in encrypting sensitive information such as monetary transactions and government communication. It is highly efficient when deployed in the 128 bits form and there are virtually no attacks that can topple the system other than illegal actions in the form of brute force.
RSA (Rivest-Shamir-Adleman): RSA is an asymmetric encryption algorithm used for secure data transmission. It gained popularity among millions of people when they started using online services to buy different goods or make other sorts of payments. Its strength lies in generating highly complex encrypted data that is nearly impossible for the hackers to decipher — this makes it a reliable and robust algorithm for encrypting sensitive information.
Blowfish: Blowfish is a symmetric encryption algorithm that has long been recognized for its speed and efficiency. Many software applications resort to it while protecting passwords and other sensitive data.
ECC (Elliptic Curve Cryptography): ECC on the other hand uses smaller key sizes than traditional Asymmetric Cryptography methods thereby offering stronger security with limited processing power needed; thus making it suitable for mobile devices or environments with limited processing ability and storage capacity.
About the Creator
Werbooz Private Limited
Werbooz offers a range of digital services including custom website solutions. With a team of skilled professionals, they transform ideas into stunning digital experiences, ensuring startups and businesses succeed in the digital landscape.
Reader insights
Nice work
Very well written. Keep up the good work!
Top insight
On-point and relevant
Writing reflected the title & theme





Comments
There are no comments for this story
Be the first to respond and start the conversation.