Must-Have Kali Linux Tools for Cybersecurity Specialists in 2026
Cybersecurity Specialists in 2026

Kali Linux is a popular platform among professionals working in ethical hacking and cybersecurity. With the global cybersecurity tools market estimated to rise to USD 208.05 billion in 2025 and potentially surpassing USD 450 billion by 2033 at a CAGR of 9.5%, the demand for efficient security tools has never been greater, as per Business Research Insights.
Kali Linux provides a complete suite to conduct penetration testing, vulnerability assessment, and network auditing. By learning these tools, you sharpen your cybersecurity skill set and prepare yourself to be successful as a cybersecurity specialist. Here’s a list of the 15 most essential Kali Linux tools for 2026.
1. Wireshark
Wireshark, a packet analyzer, catches and inspects traffic on a network in real-time. Cybersecurity experts leverage Wireshark to troubleshoot networks, detect anomalies, and examine the structure of packets. Wireshark is a crucial tool for analyzing communication between devices and understanding the behavior of a network.
2. Nmap
Nmap assists in viewing devices, open ports, and services on the network. Ethical hackers will use it for network discovery, vulnerability scanning, and security auditing. It has a scripting engine to automate checks for known vulnerabilities to increase overall cybersecurity skills.
3. Metasploit Framework
Metasploit is an exploitation framework that is robust enough to assist ethical hackers in replicating the attacks they would encounter in a real-life situation. Users can execute payloads, explore vulnerabilities, and conduct post-exploitation tasks.
4. Burp Suite
Burp Suite is a web application testing tool and acts as an intercepting proxy. It can manipulate HTTP/HTTPS traffic and find vulnerabilities like SQL injection or XSS. Many cybersecurity specialists use it as a thorough testing tool for web security assessments.
5. Aircrack-ng
Aircrack-ng evaluates Wi-Fi network security by monitoring traffic and capturing authentication handshakes. It cracks WEP/WPA/WPA2 passwords, thus it is an essential ethical hacking tool for the assessment of wireless networks.
6. John the Ripper
John the Ripper is a password-cracking tool that supports dictionary, brute-force, and hybrid attacks and is often used to test password strength and find weak authentication methods by cybersecurity professionals.
7. SQLmap
SQLmap automates the detection of SQL injection vulnerabilities in web applications, extracts database information, and tests for back-end vulnerabilities, making it essential for penetration testing of websites and applications.
8. Maltego
Security teams can find hidden connections between email addresses, IP addresses, and social media profiles due to Maltego's visual link analysis feature. By identifying possible weaknesses before attackers take advantage of them, it aids in threat intelligence, footprinting, and reconnaissance. For proactive cybersecurity investigations, this makes it an essential tool.
9. Hydra
Hydra is a fast login cracker that supports multiple protocols such as SSH, FTP, and HTTP. Ethical hackers can use it to test password security and assess the strength and robustness of authentication across systems.
10. OpenVAS
OpenVAS is a full-featured vulnerability scanner that is used to evaluate systems and networks for vulnerabilities. OpenVAS will run full scans to find things like outdated software, misconfigured features, or any other point of access for an attacker. OpenVAS is commonly used as a part of a penetration test and a risk assessment to add to the security posture.
5 Other Notable Kali Linux Tools
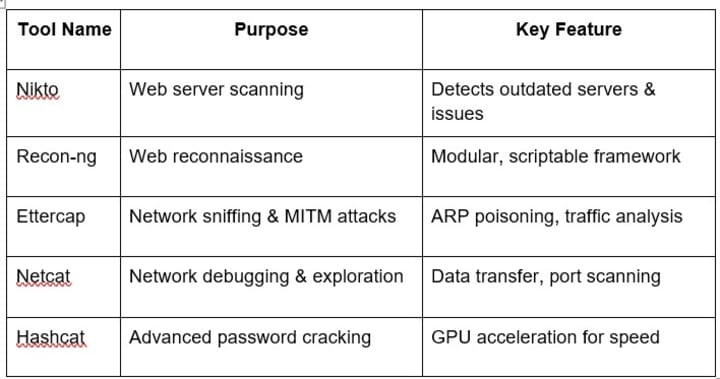
Why These Tools Matter in 2026
The world of cybersecurity is becoming increasingly complex. Networks are interconnected, systems are sophisticated, and the threat landscape is ever-evolving. Ethical hackers and cybersecurity specialists use these Kali Linux tools to successfully conduct penetration testing, find vulnerabilities, and secure systems.
By mastering these tools, you can enhance your cybersecurity expertise, develop your skills to recognize and remediate weaknesses, and help you stay ahead and prepared for new threats in our current security environments.
Getting Started with Kali Linux Tools
● Install Kali Linux: Download official ISOs or use virtual machines to provide a secure environment to practice.
● Learn the Command Line: Most tools operate via the terminal, so this is essential knowledge for professionals involved in network security, including ethical hackers. Individuals may pair this hands-on learning with top cybersecurity certifications, such as Certified Senior Cybersecurity Specialist (CSCS™) from USCSI®, or more formal programs offered by Ivy League Universities, such as Stanford University, Advanced Cybersecurity Program.
● Practice in Labs: Use controlled networks or virtual environments to get real-world experience working on penetration testing scenarios and workflows with tools.
● Documentation: Read through official documentation, tutorials, and community guides to gather insight into each tool’s intent and functionality.
Conclusion
Kali Linux enables ethical hackers and cybersecurity specialists to have tools for network scanning, web penetration testing, password auditing, and reconnaissance. To remain current and proficient, professionals need to work in a lab, try the tools, and simulate real-world attacks.
Continuous hands-on work will not only help professionals remain sharp regarding their cybersecurity skills, but also increase their ability to find vulnerabilities and improve systems and defenses against the continuous threats that exist, and keep experts active in modern cybersecurity.
About the Creator
Pradip Mohapatra
Pradip Mohapatra is a professional writer, a blogger who writes for a variety of online publications. he is also an acclaimed blogger outreach expert and content marketer.






Comments
There are no comments for this story
Be the first to respond and start the conversation.