The New Playbook for Cybersecurity Marketing in 2026
Inside the strategies that help cybersecurity brands cut through noise and earn lasting trust.

Cybersecurity companies are competing in one of the most high-stakes markets on earth. Global spending reached $213 billion in 2025, according to Gartner, as organizations rushed to secure their digital ecosystems. Yet for many vendors, the greatest challenge isn’t technology — it’s visibility.
Nearly every platform promotes “AI-powered protection” or “next-generation defense.” Buyers have stopped listening. They verify through peer networks, analyst evaluations, and independent reviews long before a form submission ever happens. In this climate, marketing isn’t about getting louder; it’s about earning credibility in the places where decisions actually start.
Understanding the Cybersecurity Buyer Journey
Cybersecurity buyers don’t behave like typical B2B audiences. Their process is discreet, technical, and high-stakes. Every new product must prove it can strengthen defenses without adding risk. The result is less a funnel and more a series of verifications where credibility must be re-established at every turn.
CISOs, compliance officers, and IT directors conduct research quietly. They rely on trusted peers and analyst insights long before any vendor contact. Because of confidentiality and compliance constraints, they engage late — often after internal pilots or controlled testing.
Three characteristics define this process:
- Extended evaluation: long review periods and layered sign-offs.
- Multiple stakeholders: from security and legal to finance.
- Zero tolerance for failure: a bad product can trigger real-world damage.
For marketers, this means success comes from being trusted in the right environments, not from shouting across every channel.
Mapping a Cybersecurity Buyer Path
A cybersecurity purchase rarely follows a straight journey. It moves through checkpoints that reflect how trust develops:
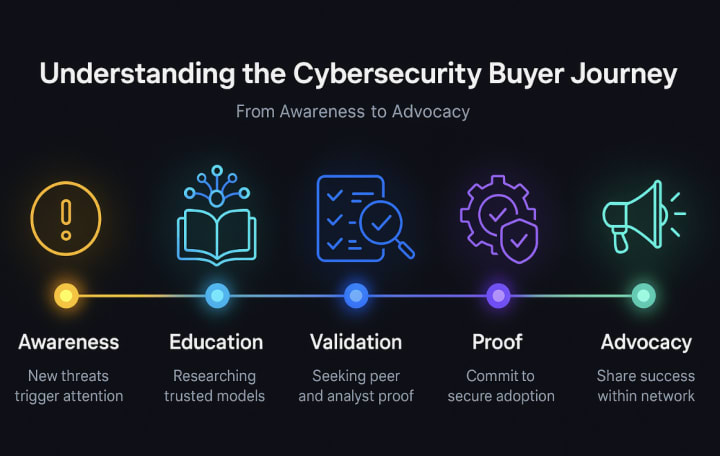
- Awareness: Triggered by a new threat or compliance update.
- Education: Research into models like “Zero Trust” or “AI detection.”
- Validation: Analyst comparisons, peer feedback, and case studies.
- Proof: Controlled demos or pilots to confirm capability.
- Advocacy: Satisfied clients who share experiences and influence peers.
Marketing that mirrors this flow — helping buyers validate instead of selling prematurely — earns lasting attention.
Core Strategies for Cybersecurity Marketing in 2026
Understanding buyer psychology is only the first step. To stand out in an industry flooded with similar promises, cybersecurity brands must turn that insight into execution. The following strategies define how visibility, credibility, and growth align in 2026.
1. Position Through Clarity, Not Complexity
The cybersecurity space is overloaded with jargon. Words like “AI-driven,” “Zero Trust,” and “next-gen” have lost meaning. What cuts through now is specificity — communicating measurable outcomes instead of technical claims.
Positioning should highlight what changes for the client:
- Performance: faster detection or response.
- Simplicity: seamless integration with existing systems.
- Proof: verifiable results from pilots or case studies.
Translate engineering precision into business clarity. Instead of “advanced endpoint telemetry,” say “real-time detection that reduces incident response time.” Clear, confident messaging conveys expertise better than exaggerated claims.
2. Build Visibility Across SEO, AEO, and GEO
Cybersecurity search terms are some of the toughest to rank for. Winning attention now requires a multi-layered visibility strategy that reaches both human and AI-driven discovery.
- SEO: Focus on intent-driven topics — “how to comply with SOC 2,” “what is automated threat response.”
- AEO (Answer Engine Optimization): Create structured explainers and FAQs that AI overviews and search assistants can cite reliably.
- GEO (Generative Engine Optimization): Produce research-backed, authoritative content more likely to appear in AI-generated summaries on platforms like ChatGPT or Perplexity.
Credibility online mirrors credibility offline — every fact, citation, and byline contributes to visibility where it matters most.
3. Generate Demand with Context and Precision
Paid advertising still plays a role, but scale without strategy wastes budget. High CPCs and ad restrictions make contextual credibility the real differentiator.
Cybersecurity buyers respond to useful insight, not direct promotion. Reports, frameworks, and practical resources — such as threat benchmarking studies or compliance readiness guides — engage far better than ads that shout features.
The strongest demand generation happens inside ecosystems of trust: professional communities, partner networks, and research collaborations where expertise matters more than exposure.
4. Leverage Partnerships and Earned Media
When ad reach is limited, visibility grows through alignment. Partnerships, media exposure, and joint initiatives scale credibility faster than any paid channel.
- Publish expert commentary or contribute to industry analysis.
- Issue press releases that communicate verified achievements, not generic updates.
- Co-create webinars or reports with complementary brands to merge trust bases.
- Build presence within MSSP, GSI, or cloud-marketplace ecosystems where purchase decisions originate.
Visibility earned through credible associations compounds — each collaboration adds another layer of trust.
5. Measure What Moves Real Deals
Cybersecurity marketers can’t rely on vanity metrics. Clicks and impressions mean little if they don’t translate into action. What matters are indicators that reflect intent and conversion quality:
- Demo requests and POC signups as primary signals of buyer readiness.
- Engagement depth, measured by time spent on technical or compliance content.
- AI search visibility, such as brand mentions in AI-generated summaries.
- Pipeline velocity, the time between first contact and closed deal — a true reflection of message clarity.
Metrics should reveal how trust builds, not just how traffic flows.
Navigating Barriers Unique to Cybersecurity
Even with solid strategy, cybersecurity marketers face persistent structural obstacles:

- Market fatigue: repetitive claims make differentiation harder.
- Slow internal approvals: compliance reviews delay execution.
- Ad restrictions: security-related terms face strict oversight.
- Technical–creative divide: complexity overwhelms communication.
- Talent shortage: few marketers blend industry and digital expertise.
Fixing these foundations — faster approval processes, better collaboration between technical and marketing teams, and partnerships with experienced specialists — multiplies the impact of every outward campaign.
Conclusion
Marketing cybersecurity solutions requires more than technical accuracy — it demands trust architecture. Each company operates under different levels of complexity, compliance, and maturity, but the fundamentals remain constant:
The cybersecurity market rewards consistency and credibility more than creativity alone. The brands that align those values across every touchpoint are the ones buyers remember when it’s time to act.
About the Creator
Max Mykal
I’m Max, a Digital Marketing & SEO specialist with 4+ years of experience. At LenGreo, I help industries like Biotech, Cybersecurity and iGaming grow with tailored strategies. Let’s connect to drive your business forward!






Comments
There are no comments for this story
Be the first to respond and start the conversation.