The Five Stages of a Penetration Test
Penetration testing is the method of abusing an organization’s network in order to figure out how to defend it better.

What is Cybersecurity?
Penetration testing is what we can call ethical hackers' work. They think like they are hackers with bad intentions and attack their own systems. This helps them understand the strengths and weaknesses of their client's websites and protect their organizational assets.
Cybersecurity is one of the best fields to be in, thanks to the large number of companies going remote. Cyber threats are ever-increasing and cybercriminals are finding new ways to exploit their systems.
Doing penetration testing is not an easy process and takes a lot of time. It goes through multiple stages until the vulnerability is found. To successfully exploit a network takes the right tools, a strong skill set, and most importantly, patience.
Research the Company
This is the first step that you need to do in order to perform successful pen-testing work. Researching the company helps you find the technologies that they use and to find common security flaws. The information that you gather about the target is going to come in handy down the line.
The tools that pen-testers use for this include Google and many other free ones on the internet. Once you gather enough information you can map out what you know about the company so that it’s easier for you to understand.

It’s crucial that in the first step you don’t do any actual testing. You just have to gather intel on the subject from an outsider's perspective without using special tools.
Inspection
Now you really start to mess with the systems that the company has in place. You should start sending data packets to figure out the open ports, IP addresses, Operating System information, and many more. Try to interrupt the target’s systems by sending data packets and DOS-ing (Denial Of Service) them.
One of the best tools to use to scan a network is Nmap. It will help figure out the map of the network and provide a lot of information about the systems.
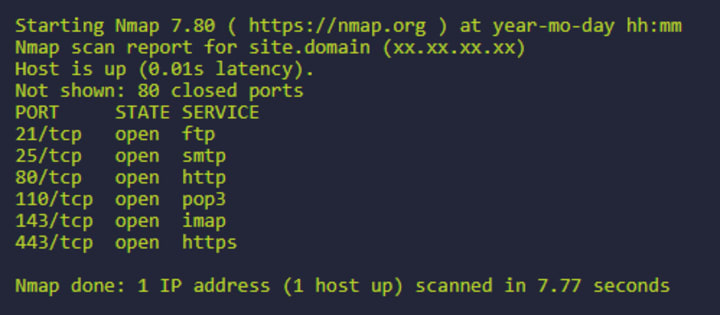
Nmap also offers a number of CLI options including scan exports that you can then import into the exploitation tools.
Penetrate the System
This stage involves trying to penetrate the systems with the information gathered from before. You will try to gain and maintain access to different points in the architecture of the systems in place.
To consider this a success you should at least gain access at a user level since from there you can try to escalate to more privileges.

One of the best tools to perform exploits is Metasploit and is widely used by most pen testers. This tool is frequently updated and is generally simple to use but offers great results. You can match your scan results with the available exploits published on the Common Vulnerabilities and Exposures database and use that exploit from Metasploit to attack the target.
Having Constant Access to the System
After all the hard work that goes into gaining access, you will need a way to maintain it at all times. This is where backdoors or keyloggers come into play. Once you have elevated access to the system you can install virtually anything that you desire.

You can install trojans, rootkits, and other backdoor exploits to help you continually have access. Rootkits are really dangerous and are widely found online. You can get a rootkit just by downloading a file from an untrusted source and the scary thing about it is that you don’t know when it gets installed.
Trojan horses are really scary too, they act like normal software but have malicious code installed inside of them. Usually, these are found on pirated files from torrents. It can be used for various reasons and always have bad intentions.
Perform a Report
This is the final stage of penetration testing and is really important. If you don’t do this you are considered an attacker.

You need to document the process that you took to finding the exploits and vulnerabilities and present them to the company in a professional manner. This way the company knows exactly where the weaknesses are and can react accordingly.
Closing Thoughts
Penetration Testing and Cybersecurity are great career choices and if you are skilled you can earn a lot. There are new sites and devices that come online every day so the opportunity to exploit systems is always there. So it’s the pen-testers job to help these new companies feel safe on the internet.
About the Creator
Kevin Gabeci
Create with Heart and Build with Mind | Programmer with a Passion for Writing | Crypto is the Future #Bitcoin #Dogecoin






Comments
There are no comments for this story
Be the first to respond and start the conversation.