The Complete Guide to Hack Facebook Account Security in 2026
Understanding Threats and Protecting Yourself
Have you ever wondered how Facebook accounts are compromised, or more importantly, how you can shield yours from such an invasion? In an era where our digital and social lives are deeply intertwined, a hacked Facebook account can lead to more than just embarrassing posts—it can result in financial fraud, identity theft, and a profound loss of privacy. This guide delves into the mechanics behind Facebook hacking not to enable malicious activity, but to empower you with knowledge. By understanding the tools and techniques cybercriminals use, you can build an impenetrable defense for your online identity.
The stakes are high. In one sophisticated campaign between January and April 2025, cybercriminals used phishing pages to target over 830 organizations and their members, actively circumventing security measures like multi-factor authentication (MFA) to steal sensitive data. On a personal level, hackers stole a staggering $770 million from social media users in a single year by taking over accounts and accessing linked payment information. This isn't just about passwords; it's about protecting your financial health and personal reputation.
Software in the Hacking Security Ecosystem: Tools for Education ONLY
It's crucial to distinguish between malicious hacking tools and software designed for legitimate security education and recovery.
1. PASS FINDER: Pass Finder is the application to hack passwords for Facebook and Messenger accounts. It uses an artificial intelligence algorithm to accelerate the password-breaking process through a real-time data interception and deep cryptographic decryption.
Official Site: https://www.passwordrevelator.net/en/passfinder

2. John the Ripper: An advanced, open-source password security auditing and password recovery tool. It is one of the most well-known and versatile tools for detecting weak passwords in a system. John operates by taking text strings (like from a password hash dump), encrypting them in the same way as the system being tested, and comparing the outputs. It supports dozens of hash and cipher types, including common ones like NTLM, md5crypt, and bcrypt.
Official Site & Documentation: https://www.openwall.com/john/

3. Hashcat: Billed as the world's fastest and most advanced password recovery utility, it is a CPU and, more powerfully, GPU-driven engine. Hashcat excels at breaking complex password hashes through highly optimized algorithms that leverage the parallel processing power of modern graphics cards. It supports over 300 hash algorithms and features multiple attack modes, including straight dictionary attacks, combinator attacks, rule-based attacks (for sophisticated password mutations), brute-force, and hybrid attacks.
Official Site & Wiki: https://hashcat.net/hashcat/
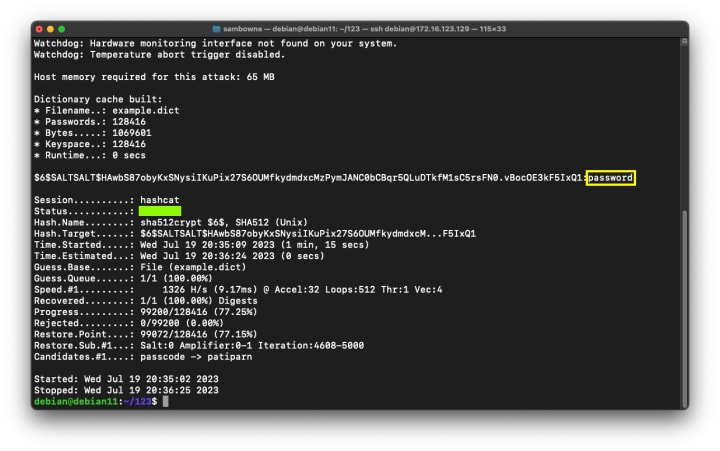
4. CeWL (Custom Word List generator): A specialized ruby application designed to spider a given target's website to a specified depth and then build a unique, tailored wordlist based on the words found. This technique is pivotal in penetration testing for crafting targeted dictionary attacks, as passwords often relate to a company's products, technologies, personnel names, or internal jargon.
Official GitHub Repository: https://github.com/digininja/CeWL

How Facebook Accounts Are Compromised: The Hacker's Playbook
Cybercriminals don't rely on magic—they use predictable, yet often effective, methods to gain unauthorized access. Knowing these tactics is your first line of defense.
- Phishing: The Digital Bait and Hook: This is the most prevalent method. You receive a message—often from a hijacked friend's account or a fake profile—containing a compelling link. It might promise a "viral video," a shocking news story, or even appear to be a Facebook security alert. The link leads to a bogus Facebook login page that looks nearly identical to the real one. When you enter your credentials, they are sent directly to the hacker. Modern phishing campaigns can be highly sophisticated, using platforms like Telegram to receive stolen login credentials and one-time passwords in real-time, effectively bypassing MFA.
- Social Engineering: Manipulation Over Technology: Here, hackers exploit human psychology rather than software flaws. They might pose as Facebook support, a distressed friend, or a romantic interest to trick you into voluntarily revealing your password or a security code. Another common tactic is creating a sense of urgency (e.g., "Your account will be deleted!") to cloud your judgment.
- Credential Stuffing and Weak Passwords: Many people reuse the same email and password across multiple sites. When a data breach occurs on another platform, hackers use automated tools to "stuff" those stolen credentials into Facebook's login page. If your password is simple, common, or based on personal information, it can also be easily guessed.

Building Your Digital Fortress: Proactive Protection Strategies
Securing your account is a multi-layered process. Implement these steps to significantly reduce your risk.
- Create an Unbreakable Password and Use a Manager: Your password should be a long, random combination of letters (upper and lower case), numbers, and symbols. Never use personal information. Consider using a reputable password manager to generate and store unique, complex passwords for every site you use.
- Enable Two-Factor Authentication (2FA) - The Essential Layer: 2FA is the single most effective security step you can take. Even if a hacker gets your password, they cannot log in without the second factor—usually a code from an authenticator app or your phone. Be aware of advanced phishing tactics that try to steal these codes in real-time, and only enter them on the official Facebook site.

Master Your Privacy and Security Settings:
- Review Active Sessions: Regularly check where your account is logged in. Immediately log out of any unfamiliar devices or locations.
- Audit Third-Party App Access: Remove permissions for old games, quizzes, or apps you no longer use.
- Adjust Privacy Settings: Limit the visibility of your posts, friend list, and personal information (email, phone number) to friends only.
Cultivate Smart Online Habits:
- Be Skeptical of Links and Requests: Do not click on suspicious links, even from friends. Verify through another channel if unsure. Do not accept friend requests from people you don't know.
- Look for "HTTPS": Always ensure the site address starts with https:// (the "s" stands for secure) before entering any login information.
Avoid Public Wi-Fi for Logins: If you must use public Wi-Fi, use a VPN to encrypt your connection.
Damage Control: What to Do If You've Been Hacked
If you suspect your account is compromised, act quickly and methodically.
- Immediate Account Recovery: Go directly to Facebook's official hacked account page (facebook.com/hacked). This guided tool will help you secure your account by changing your password and reviewing recent activity.
Complete a Security Sweep:
- Change Your Password Again: Do this from a trusted device after regaining access.
- Log Out Everywhere: Use the security settings to log out of all sessions globally.
- Review Account Activity: Check for unauthorized posts, messages, or changes to your profile.
- Alert Your Friends: A quick post can help stop the scam from spreading through your network.
- Report to Facebook: Use Facebook's reporting tools to indicate your account was compromised. This helps their security systems.
Frequently Asked Questions (FAQ)
Q: Is it really possible to hack a Facebook account with free software online?
A: While countless websites claim to offer free Facebook hacking tools, these are almost universally scams. Their purpose is to deliver malware to your computer, steal your own data, or trick you into completing surveys for profit. There is no safe, legal, or ethical "one-click hack" for Facebook accounts.
Q: Can someone hack my Facebook if they are just my friend on the platform?
A: Being friends alone does not grant hacking access. However, it provides a platform for social engineering. A hacker with a fake or compromised friend account can send you malicious links with a higher chance of you trusting and clicking them, leading to phishing. Always be cautious of unexpected messages, even from friends.
Q: I've heard two-factor authentication (2FA) can be hacked. Is it still worth using?
A: Absolutely. 2FA remains critically important. While sophisticated attacks exist that try to intercept 2FA codes through real-time phishing, it still blocks the vast majority of automated and casual hacking attempts. For enhanced security, use an authenticator app (like Google Authenticator or Authy) instead of SMS codes where possible.
Q: What's the biggest mistake people make that leads to their account being hacked?
A: The most common mistakes are password reuse and falling for phishing scams. Using the same password on multiple sites means a breach elsewhere compromises Facebook. Clicking a cleverly disguised phishing link and entering your login details gives hackers direct access, bypassing most other security measures.
Q: Where can I get official help from Facebook for a security problem?
A: Your only trusted source is Facebook's own Help Center and the dedicated Security Page. The official hacked account tool is at facebook.com/hacked, and following Facebook's Official Security Page keeps you updated on new threats. Never trust security advice from unverified sources or individuals claiming to be "Facebook support" in private messages.
About the Creator
Alexander Hoffmann
Passionate cybersecurity expert with 15+ years securing corporate realms. Ethical hacker, password guardian. Committed to fortifying users' digital safety.
Reader insights
Good effort
You have potential. Keep practicing and don’t give up!
Top insights
Compelling and original writing
Creative use of language & vocab
Easy to read and follow
Well-structured & engaging content
Excellent storytelling
Original narrative & well developed characters
Expert insights and opinions
Arguments were carefully researched and presented
Eye opening
Niche topic & fresh perspectives
Heartfelt and relatable
The story invoked strong personal emotions
Masterful proofreading
Zero grammar & spelling mistakes
On-point and relevant
Writing reflected the title & theme






Comments
There are no comments for this story
Be the first to respond and start the conversation.