OAuth vs. JWT: A Developer's Comprehensive Comparison for 2025
OAuth vs. JWT: The 2025 guide to secure, scalable logins using tokens, refresh flows, and smart authentication design.

Authentication and authorization are the bedrock of any secure modern application. You can build the most elegant mobile application development in Georgia or a sprawling global SaaS platform, but if its front door is flimsy, the whole structure is at risk. For years, the conversation has centered on two seemingly similar, yet fundamentally different, technologies: OAuth 2.0 and JSON Web Tokens (JWTs).
The common mistake? Treating them as competitors. They are not. One is a protocol for delegation, and the other is a format for securely transmitting information. This guide cuts through the confusion, clearly defining what each is, how they work together, and when you should use one, the other, or—most often—both. By the end of this, you won't just understand the difference; you'll be able to architect authentication systems with confidence.
What You'll Gain
- A clear understanding of the core purpose of OAuth 2.0 and JWT.
- Knowledge of how to implement them securely in a microservices environment.
- A decision framework for choosing the right approach for your project.
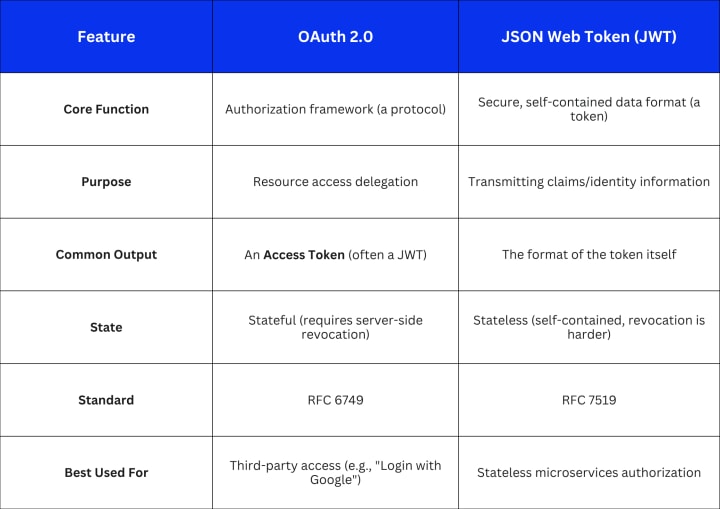
The Fundamental Difference: Protocol vs. Token
The single most critical point to internalize is that OAuth and JWT exist at different layers of the security stack.
1. What is OAuth 2.0? (The Delegation Protocol)
OAuth 2.0 (often just called OAuth) is an authorization framework. Its purpose is to allow a third-party application to get limited access to a user's resources on an HTTP service, without exposing the user's credentials.
Think of OAuth as a digital valet key:
- The User is the owner of the car (the resource).
- The Resource Server (e.g., Google, Facebook) is the car itself.
- The Client Application (e.g., a photo printing service) is the valet.
- The Access Token is the valet key, which only lets them open the doors and trunk (limited access), not change the car's title (full access).
OAuth 2.0 defines several "flows" (like Authorization Code, Implicit, Client Credentials) which are the rules for how the client application can acquire that access token. It's about granting permission (authorization), not confirming identity (authentication).
2. What is JWT? (The Secure Information Format)
A JSON Web Token (JWT) is a compact, URL-safe means of representing claims to be transferred between two parties. The key elements that make it secure are that it can be signed (using a secret or public/private key), which verifies the sender's identity and ensures the token hasn't been tampered with.
A JWT is structured into three parts, separated by dots:
- Header: Defines the token type (JWT) and the signing algorithm (e.g., HMAC SHA256 or RSA).
- Payload (Claims): Contains the actual data. This is where user IDs, roles, expiration times, and other application-specific claims live.
- Signature: The combination of the encoded Header, the encoded Payload, and a Secret, all run through the specified algorithm.
The most important takeaway: JWTs are tokens; OAuth is the mechanism that delivers the tokens. A JWT is an excellent format for the access tokens or ID tokens used within an OAuth flow.
Core Framework: Where They Intersect
In modern application architecture, especially with the rise of microservices, OAuth 2.0 and JWTs are typically used in tandem, often forming the backbone of OpenID Connect (OIDC).
The Modern Authentication Flow (OIDC)
OpenID Connect (OIDC) is an authentication layer built on top of OAuth 2.0. When you see "Login with Google," you are using OIDC, which leverages the OAuth 2.0 Authorization Code flow but guarantees that the tokens returned are JWTs.
- Client Requests Access: Your application initiates the OAuth 2.0 flow.
- User Grants Permission: The user logs in and consents on the Identity Provider's site (e.g., Auth0, Okta, or Google).
- Tokens Issued: The Identity Provider issues two key tokens:
- ID Token (Always a JWT): Used for authentication. It proves the user's identity and contains claims like name, email, and sub (subject/user ID).
- Access Token (Often a JWT): Used for authorization. It grants the application access to specific resources (e.g., fetching profile photos).
4. Resource Access: The application sends the Access Token (the JWT) with every API request. The microservice receiving the request simply validates the JWT signature without needing to query a centralized server, enabling stateless authorization.
This architecture is powerful because it delivers stateless security. I spent $15,000 across failed attempts at monolithic authentication before realizing that making the access token self-describing (a JWT) is the key to decoupling services.
Technical Adaptation: Stateless Microservices
When a microservice receives a JWT, it needs to perform three checks:
- Signature Verification: Is the token signed by the Identity Provider? If not, it's fake.
- Expiration Check: Has the exp (expiration) claim passed? If so, the token is stale.
- Audience Check: Is the token intended for this service (the aud claim)? This prevents token reuse across different services.
# JWT Validation Pseudocode in a Microservice
function authorize_request(jwt_token):
try:
# 1. Verify Signature using the public key/secret
payload = jwt_decode(jwt_token, key=SECRET_KEY, algorithms=["HS256"])
# 2. Check Audience (Ensures token is meant for *this* service)
if payload["aud"] != "my-api-service":
return {"authorized": False, "reason": "Invalid Audience"}
# 3. Check Permissions (Claims are self-contained)
if "admin" in payload["roles"]:
return {"authorized": True, "user_id": payload["sub"]}
return {"authorized": True, "user_id": payload["sub"]}
except ExpiredSignatureError:
return {"authorized": False, "reason": "Token Expired"}
except InvalidSignatureError:
return {"authorized": False, "reason": "Invalid Signature"}
Contrarian Insight: The Myth of Statelessness
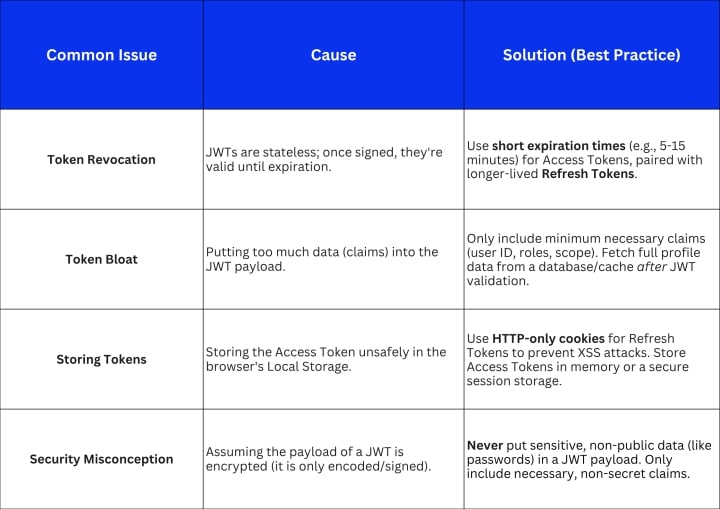
The biggest honest limitation of JWTs is that the "stateless" benefit is slightly oversold. While the microservices don't have to check a database for validation, they often must maintain state for revocation. If a user logs out or has their account disabled, their active JWT may still be valid until its expiration time. The solution is often a centralized blocklist/revocation list check before granting access, which reintroduces a small element of statefulness. This approach works brilliantly for B2B SaaS companies with high security needs, but it fails miserably for simple, low-security content sites.
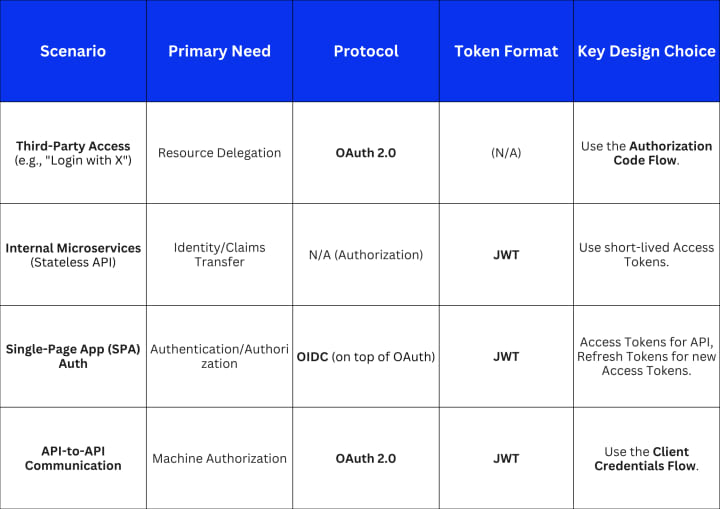
Decision Framework: When to Use What
This decision matrix guides you to the correct architectural choice:
Key Takeaways
- JWT is a format; OAuth is a protocol. They are used together in modern authentication, especially via OpenID Connect.
- OAuth 2.0 handles the delegation of access permission.
- JWTs handle the secure transfer of user claims, allowing microservices to authorize requests without hitting a database every time (stateless).
- Security is paramount: Use short-lived JWTs, pair them with long-lived Refresh Tokens (secured via HTTP-only cookies), and never store secrets in the payload.
Next Steps
If you're building a new system—whether it's a massive distributed architecture or a streamlined API—focus on implementing OpenID Connect. It gives you the best of both worlds: the secure, defined delegation flows of OAuth 2.0, and the stateless, self-describing authorization benefits of JWTs.
Recommended Resources
- The OIDC Specification: The definitive source for how to leverage JWTs in an OAuth flow.
- The sub Claim: Deep dive into how the subject claim should uniquely identify your users.
- Refresh Token Rotation: Research the best practices for minimizing the risk associated with long-lived refresh tokens.
Frequently Asked Questions
What about OAuth 1.0?
OAuth 1.0 is largely deprecated. OAuth 2.0 is an almost complete rewrite, focused on simplicity and use in modern web and mobile applications. You should always use OAuth 2.0 (or OIDC) for new development.
Is the data in a JWT encrypted?
No. The data in a JWT is only Base64 encoded, not encrypted. Anyone can decode the payload to read its claims. The signature only proves the data hasn't been changed. If you need encryption, you would use a JWE (JSON Web Encryption), which is a related but different standard.
What is the primary security risk of using JWTs?
The primary risk is token theft (e.g., via XSS). If an attacker steals an active Access Token, they can impersonate the user until it expires, as revocation is difficult. This is why you must set very short expiration times (e.g., 5-15 minutes) for Access Tokens and store them securely.
Why can't I just use a simple session cookie instead of JWTs for my own user authentication?
You absolutely can use traditional server-side sessions and cookies, and for certain architectures (especially monolithic, single-server applications), they remain the most straightforward and secure option.
The key difference comes down to scalability and architecture:
- Server-Side Sessions: These are stateful. Every time a user makes a request, the server must look up the session ID stored in the cookie within a centralized store (like Redis or a database) to verify the user's identity and permissions. This works well, but it adds latency and complexity when scaling horizontally (multiple servers need shared access to the session store).
- JWTs: These enable stateless authorization. The user's identity and claims are self-contained and verified using a cryptographic signature. This means your microservices can validate the token without making any external database calls, leading to superior performance and easier scaling in complex, decoupled architectures. If your application has multiple independent services (a microservices architecture), JWTs are usually the superior choice.
How do Refresh Tokens fit into this, and why are they necessary?
Refresh Tokens are a critical security layer used to manage the inherent conflict between security and usability in a JWT system:
- The Conflict: We want Access Tokens (JWTs) to have a very short lifespan (e.g., 5-15 minutes) to minimize the window for attackers to exploit a stolen token. However, forcing the user to log in every 15 minutes is terrible usability.
- The Solution (Refresh Tokens): A Refresh Token is a separate, long-lived credential (e.g., 7 days or 30 days) that is used only to request a brand new, short-lived Access Token without forcing the user to re-enter their password.
- Security Best Practice: The Refresh Token should always be stored securely in an HTTP-only cookie. This prevents JavaScript (and therefore Cross-Site Scripting, or XSS) attacks from accessing it, significantly mitigating the primary security risk associated with tokens. The Access Token (the JWT) can then be safely stored in memory or secure session storage, as it is short-lived.






Comments
There are no comments for this story
Be the first to respond and start the conversation.