Information Gathering: How Hackers Look You Up Without Having to Code
Searching the web for data is easy, all you need is to know what you’re looking for, and how to search for it.

Information gathering determines which way you should go, to look up someone online isn’t so hard these days, the internet gives us wings and privacy suffers a whole lot because of this.
Social Media

With all the Social Media platforms our lives become less, and less private. But, before pointing a finger at some of these networks remember that you, and me are to blame. We’ve made our own beds, believe me we share too much of our lives online. Your profile alone is a story, if yours isn’t then your partner’s profile is. Some of us try going incognito but most of our family members don’t. As a result this act of ours ends up not helping as much as it should. As seen in movies if you fail to contact me just try someone close to me instead. This benefits hackers very much.
You might use a pen name for most of your writing, a fake name on all your Social Media profiles and email addresses but your partner may be doing the exact opposite, like sharing your full name on a post when it’s your birthday, sharing your wedding photos, your son or daughter’s birth month, and a few more things we don’t take into consideration which should be too personal to go online but isn’t, at least not anymore.
Your birthday, your kids birthday, the day you got married, when you started dating, when you broke up, your anniversary all of this on a single platform. Social Media is the best place to keep yourself up to date about everything but it isn’t the only way to look up someone. Go on LinkedIn and find out what people do for a living it works like a charm.
Google Search

Compared to Social Media platforms Google gets more results, because instead of a single profile Google gets you everything it can find on your search, not to mention that the Social Media profiles also get indexed on Google. So, a simple Google search is how you should start.
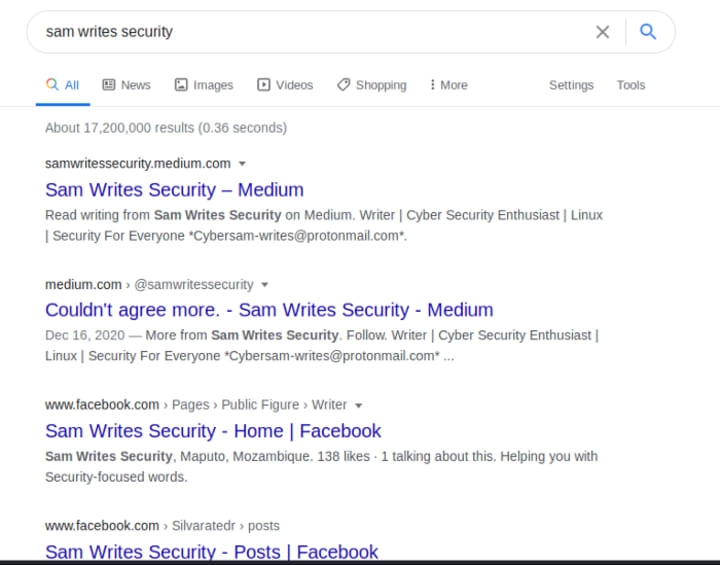
I looked up myself on Google, and it brought me 17,000,000 results. Obviously not everything it found is related to me or Vocal, the first 3 to 4 pages were useful. I didn’t use any special parameters for this search as it wasn’t really necessary, for precise Google Hacking results results read this.
With just a simple search, and still on the first page I found my medium profile, a comment, Facebook page, and Instagram page. All in a matter of seconds. My email is part of my medium bio so it shows up as well. Imagine if your home address and phone number had to go on your bio, with a single search anyone and everyone would know everything about you just like that.
I assume you don’t search for people on the web for a living, that being the case a paid people finder tool isn’t necessary Social Media platforms and search engines like Google or Bing aren’t the only free resources you can use to find people on the internet you can also try;

Username search is a Social Media search engine with over 600 sites to search from. This reverse search tool uses usernames, emails, and phone numbers. Usersearch.org is also great for searches on crypto forums. |
The website uses SSL encryption to ensure your searches on the website are safe. Based on their about page, searches are run live in RAM and are wiped every 4 minutes to improve performance, you can read more on this here. These are some of the many ways people can look you up without having to use Brute-force attacks to find out more about you. Stay safe!
This article was previously published on Medium https://medium.datadriveninvestor.com/information-gathering-how-hackers-look-you-up-without-having-to-code-2fc6e56a9080






Comments
There are no comments for this story
Be the first to respond and start the conversation.